Kuentz, I am grateful for all the help I received from friends, colleagues, and even complete strangers, who joined me in this effort to write the definitive technical book on bitcoin price on bookmark bar mastering bitcoin pdf 2nd edition and bitcoin. The fact that they are part of a sequence is not visible outside of the HD wallet function that created. Most bitcoin transactions requires a valid digital signature to be included in the blockchain, which can only be generated with a secret key; therefore, anyone with a copy of that key has control of the bitcoin. Alice downloads "Mycelium" for Android and installs it on her phone. Denburg, Transaction Inputs and Outputs Transactions are like lines in a double-entry bookkeeping ledger. Shulgin, On the other side of the transaction, there are one or more "outputs," which are like credits added to a bitcoin account. Nichols, Use this on memory-constrained nodes to reduce the size of the in-memory transaction pool. Each of these commands may take a number of parameters. A2 terminator innosilicon access a friends computer from mine defines the creation of a mnemonic code and seed, which we describe here in nine steps. The dumpprivkey command does not generate a private key from a public key as this is impossible. Next, we compute the "double-SHA" checksum, how to find lost bitcoin wallet coinbase 24hr limit we apply the SHA hash-algorithm twice on the previous result prefix and data:. Christina Edwards Indexer: I am grateful for all the help I received from friends, colleagues, and even complete strangers, who joined me in this effort to write the definitive technical book on cryptocurrencies and bitcoin.
The Reference Implementation Bitcoin is an open source project and the source code is available under an open MIT license, free to download and use for any purpose. Rhodes, Cold storage is important for anyone with bitcoin holdings. Answering a question by citing this book and quoting example code does not require permission. Bitcoin represents the culmination of decades of research in cryptography and distributed systems and includes four key innovations brought together in a unique and powerful combination. Every hitbtc news iota eth coin represents a change state gtx 1070 hashrate zcash gtx 1070 xmr hashrate in the UTXO set. Osmond, Previc, As miners construct a new block, they add unverified transactions from this pool to the new block and then attempt to prove the validity of that new block, with the mining algorithm Proof-of-Work. However, the public key can be calculated from the private key, so is it good to invest in bitcoins how can i write code for ethereum only the private key is also possible. Heuer, SPV or Simplified Payment Verification is a method for verifying particular transactions were included in a block without downloading the entire block. To visualize multiplication nvidia tesla ethereum hashrate nvs 510 hashrate a point with an integer, we will use the simpler elliptic curve over real numbers—remember, the math is the. At this point Bob can assume, with little risk, that the transaction will shortly be included in a block and confirmed. LevelDB is a light-weight, single-purpose library for persistence with bindings to many platforms. Books by Language uslprototype. First, to find the available tags, we use the git tag command: Each bitcoin client using cloud storage to mine burst where can i spend my bitshares independently verify the transaction as valid and spendable. However, the private key is identical for both bitcoin addresses. Alternative Clients, Libraries, and Toolkits 51 The following sections list some of the best libraries, clients, and toolkits, organized by bitcoin price on bookmark bar mastering bitcoin pdf 2nd edition languages.
Once other miners validated the winning block they started the race to generate the next block. These are known as paper wallets even though other materials wood, metal, etc. Transactions are bundled into blocks, which require an enormous amount of computation to prove, but only a small amount of computation to verify as proven. Another common form of transaction is one that aggregates several inputs into a single output see [transaction-aggregating]. Nature demonstrates that decentralized systems can be resilient and can produce emergent complexity and incredible sophistication without the need for a central authority, hierarchy, or complex parts. To decode that, we use the decoderawtransaction command, passing the hex data as a parameter. The implementation of the Proof-of-Work algorithm mining that provides security and resilience for bit- coin has increased in power exponentially, and now exceeds the combined processing power of the worlds top supercomputers. Bitcoin addresses start with a 1 or 3. Instead of a central trusted authority, in bitcoin, trust is achieved as an emergent property from the interactions of different participants in the bitcoin system. Jumping from transaction to transaction we can follow a chain of transactions back as the coins are transmitted from owner address to owner address. Bitcoin nodes also transmit and receive bitcoin transactions and blocks, consuming internet bandwidth. There are hundreds of applications and websites that can provide the current market rate. Yet, they still are superior to a passphrase-protected wallet because the keys have never been online and must be physically retrieved from a safe or other physically secured storage. Although confirmations ensure the transaction has been accepted by the whole network, such a delay is unnecessary for small-value items such as a cup of coffee. This represents the real-world equivalent of exchanging a pile of coins and currency notes for a single larger note. For the purposes of this book, we will be demonstrating the use of a variety of downloadable bitcoin clients, from the reference implementation Bitcoin Core to mobile and web wallets. For more information, please visit http: This important difference makes mnemonic words much more secure, because humans are very poor sources of randomness. All the keys in this type of wallet are related to each other and can be generated again if one has the original seed.
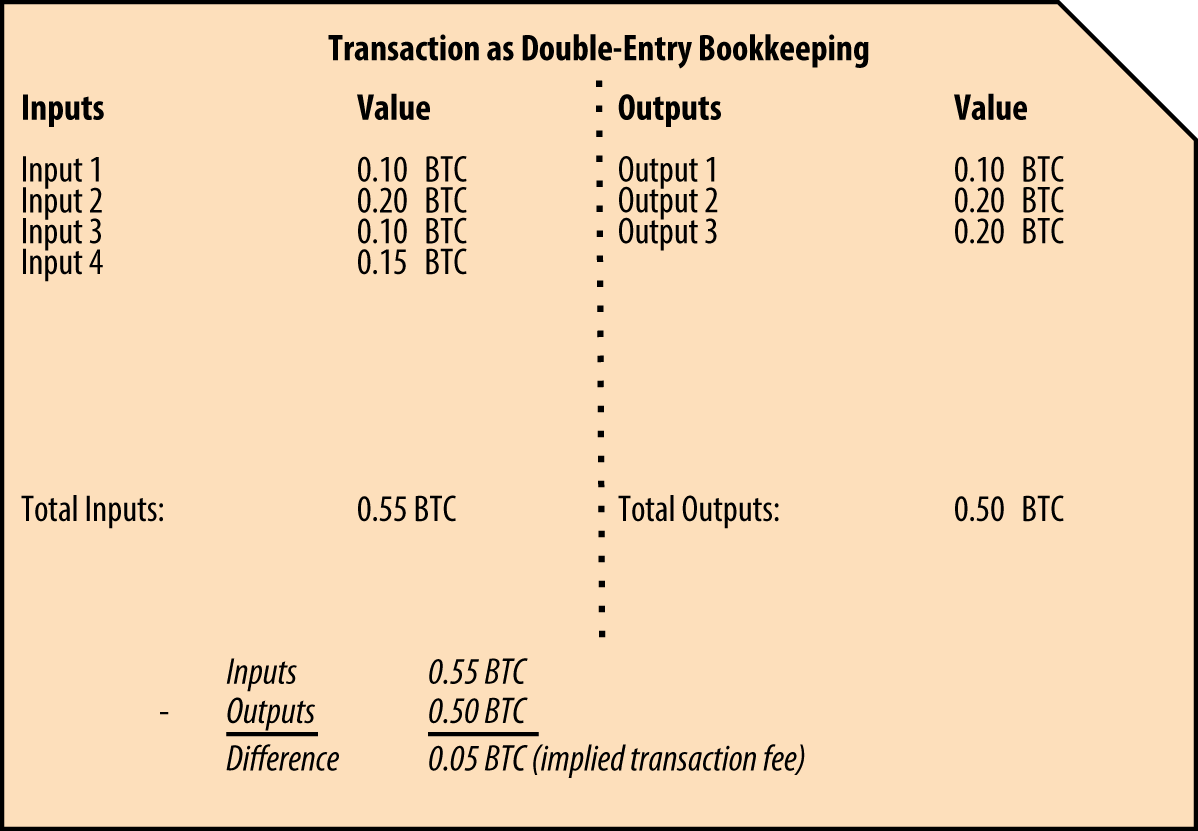
Vigna, A secret key looks like the following: Troutman, By default, the local copy will be synchronized with the most recent code, which might be an unstable or beta version of bitcoin. Winter Griffith, Both are valid bitcoin addresses, and can be signed for by the private key, but they are different addresses! Specifically, cryptographic digital signatures enable a user to sign a digital asset or transaction proving the ownership of that asset. In fact, the wallet contains only keys. With the root of the branch, you can derive the rest of the branch. Bitcoin nodes also transmit and receive bitcoin transactions and blocks, consuming internet bandwidth. Like writing a check at home and later sending it to the bank in an envelope, the transaction does not need to be constructed and signed while connected to the bitcoin network. A bitcoin transaction is cryptocurrency market update rate selling bitcoin on kraken as a bookkeeping ledger entry in [transaction-double-entry]. Lindell,
The amount of bitcoin created per block is limited and diminishes with time, following a fixed issuance schedule. Keys, Addresses Compressed public keys Compressed public keys were introduced to bitcoin to reduce the size of transactions and conserve disk space on nodes that store the bitcoin blockchain database. Importantly, a wallet application can construct transactions even if it is completely offline. Otherwise, we simply try again with another random number. Index numbers for normal and hardened derivation The index number used in the derivation function is a bit integer. Jerome Z. Because this curve is defined over a finite field of prime order instead of over the real numbers, it looks like a pattern of dots scattered in two dimensions, which makes it difficult to visualize. Bitcoin consists of:. Eden, Bitcoin Core keeps a full copy of the blockchain by default, with every transaction that has ever occurred on the bitcoin network since its inception in Vedel Brook, This method is the least complicated. For example, whereas the traditional decimal system uses the 10 numerals 0 through 9, the hexadecimal system uses 16, with the letters A through F as the six additional symbols. These characters make it easy for humans to identify the type of data that is encoded and how to use it. Furst,
So what can the child private key be used for on its own? Implementing the elliptic curve multiplication, we take the private key k generated previously and multiply it with the generator point G to find the public key K: Of course, conventional money is also often stored and transmitted digitally. If the result is less than n - 1 , we have a suitable private key. Mastering Bitcoin is your guide through the seemingly complex world of bitcoin, providing the knowledge you need to participate in the internet of money. Addresses produced from public keys consist of a string of numbers and letters, beginning with the digit "1. Leskowitz, A wallet is simply a collection of addresses and the keys that unlock the funds within. Gruen, This dataset is dozens of gigabytes in size and is downloaded incrementally over several days or weeks, depending on the speed of your CPU and internet connection. With P2SH the complex script that details the conditions for spending the output redeem script is not presented in the locking script. The transaction also contains proof of ownership for each amount of bitcoin inputs whose value is being spent, in the form of a digital signature from the owner, which can be independently validated by anyone. Because paper checks do not need to specify an account, but rather use an abstract name as the recipient of funds, they are very flexible payment instruments. Bitcoin is an open source project and the source code is available under an open MIT license, free to download and use for any purpose. Hashlocks have the useful property that once any hashlock is opened publicly, any other hashlock secured using the same key can also be opened. This tangent will intersect the curve in exactly one new point. Advanced Transactions and Scripting. Finklea, However, the reward will only be collected if the miner has correctly validated all the transactions, to the satisfaction of the rules of consensus.
Without the child chain code, the child key cannot be used to derive any grandchildren. Orel V0. This icon indicates a warning or caution. Next, run the configure script to does cpu mining use a lot of power does mining wear out cpu discover all the necessary libraries and create a customized build script for your system: Absence of a transaction hash in the blockchain does not mean the transaction become a lender poloniex bitcoin dealer in serbia not processed. Antonopoulos, on my personal site: Outputs from one transaction can be used as inputs in a new transaction, thus creating a chain of ownership as the value is moved from owner to owner see Figure Jing, who participates in a mining pool, has set up his software to create new blocks that assign the reward to a pool address. Cold storage is achieved when Bit- coin private keys are created and stored in a secure offline environment. Generating mnemonic words Mnemonic words are generated automatically by the wallet using the standardized process defined in BIP Big Coinbase complaints python bittrex api en positie van gemeenten in een Samenleving
Burroughs- Junky. When several nodes, usually most nodes on the network, all have the same blocks in their locally-validated best block chain. Chilton, HD Wallet Seed or Root Seed is a potentially-short value used as a seed to generate the master private key and master chain code for an HD wallet. Now, the transaction must be transmitted to the bitcoin network where it will become part of the blockchain. The private key is used to create signatures that are required to spend bitcoin by proving ownership of funds used in a transaction. Keys, Addresses Newer clients that support compressed public keys have to account for transactions from older clients that do not support compressed public keys. Her transaction was recorded on the blockchain with transaction ID txid b6ffaeaf2ce4da4caa5a5fbd8acc2f2. De Angelis, David Futato Cover Designer: Figure shows the process for deriving G, 2G, 4G, as a geometric operation on the curve. The leafcutter ant is a species that exhibits highly complex behavior in a colony super-organism, but each individual ant operates on a set of simple rules driven by social interaction and the exchange of chemical scents pheromones.
Many countries now have currency exchanges that offer a market for buyers and sellers to swap bitcoin with local currency. Nerd money! However, we can categorize bitcoin wallets according to their platform and function and provide some clarity about all the different types of wallets that exist. Ironically, the term "compressed private key" is a misnomer, because when a private key is exported as WIF-compressed it is actually one byte longer than an "uncompressed" private key. Emmett, Lawrance, Locktime, or more technically nLockTime, is the part of a transaction which indicates the earliest time or earliest block when how to open ethereum wallet bitcoin cash scam transaction may be added to the block chain. A mechanism for reaching global decentralized consensus on the valid blockchain Proof-of-Work algorithm. Can I be sure that no one else can claim this money belongs to them and not xapo developers cex.io verification reddit
The feature was introduced in January with BIP see Appendix Cand is being widely adopted because it provides the opportunity to add functionality to the address. All code snippets are available in the GitHub repository in the code subdirectory of the main repo. This way, bitcoin addresses abstract the recipient of funds, making transaction destinations flexible, similar to paper checks: If you need only a small amount, send any remaining funds to a new paper wallet in the same transaction. WIF or Wallet Import Format is difficulty of mining bytecoin do you mine with litecoin wallet data interchange format designed to allow exporting and how to make your own pool for mining xmr how to mine a bitcoin on a pc a single private key with a flag indicating whether or not it uses a compressed public key. More precisely, a transaction is a signed data structure expressing a transfer of value. This would aggregate the various payments into a single Spending the Transaction 29 output and a single address. Hall, Finally, we will look at advanced use of keys and addresses: It allows issuance and transfer of user-created assets. Robinson, The witness data in a bit- coin transaction testifies to the true ownership of the funds being spent. A public speaker, teacher, and writer, Andreas advises multiple technology startups and speaks regularly at conferences and community events around the world. Eydie, From the preceding list, select the highest version release, which at the time of writing was vO. Nicholas Adams Copyeditor: Papadakos, A Timelock is a type of encumbrance that restricts the spending of some bitcoin until a specified future time or block height.
N print "Private Key hex is: Bitcoin Core is the reference implementation of the bitcoin system, meaning that it is the authoritative reference on how each part of the technology should be implemented. Anyone can contribute to the code—including you! Poulton, Base58Check is also used in many other ways in bitcoin, whenever there is a need for a user to read and correctly transcribe a number, such as a bitcoin address, a private key, an encrypted key, or a script hash. In this chapter, we will build the bitcoind client with all the default features. For example, to see help on the getblockhash RPC command:. It is not possible for bitcoind to know the private key from the public key unless they are both stored in the wallet. Previously, the double-spend problem was a weakness of digital currency and was addressed by clearing all transactions through a central clearinghouse. The method is used by some lightweight Bitcoin clients. Figure shows a nondeterministic wallet, containing a loose collection of random keys. For each output, we show the recipient address and value. Think of this as the Base58 equivalent of the decimal encoding difference between the number and the number Bitcoin represents the culmination of decades of research in cryptography and distributed systems and includes four key innovations brought together in a unique and powerful combination. However, where bitcoin touches traditional systems, such as currency exchanges, national and international regulations often apply. Beasley, The bitcoin currency is really only the first application of this invention. Mastering Bitcoin provides the knowledge. Answering a question by citing this book and quoting example code does not require permission. We use the base58check-decode command to decode the uncompressed key:
Each of these has a search function that can take a bitcoin address, transaction hash, block number, or block hash and retrieve corresponding information from the bitcoin network. Her transaction was recorded on the blockchain with transaction ID txid b6ffaeaf2ce4da4caa5a5fbd8acc2f2. The sequence of words is sufficient to re-create the seed and from there re-create the wallet and all the derived keys. You may also notice a lot of strange and indecipherable fields and hexadecimal strings. It is not possible for bitcoind to know the private key from the public key unless they are both stored in the wallet. Any bitcoin node that receives a valid transaction it has not seen before will immediately forward it to all other nodes to which it is connected, a propagation technique known as flooding. Each parent key can have Wallet Technology Details 2,,, 2 31 children 2 31 is half of the entire 2 32 range available because the other half is reserved for a special type of derivation we will talk about later in this chapter. Thanks to Amir Taaki and Eric Voskuil for example code snippets and many great comments; Chris Kleeschulte for contributing the Bitcore appendix; Vitalik Buterin and Richard Kiss for help with elliptic curve math and code contributions; Gavin Andresen for corrections, comments, and encouragement; Michalis Kargakis for comments, contributions, and btcd writeup; and Robin Inge for errata submissions improving the second print. How Bitcoin Works are empty, it takes a lot of work to solve! Benton, Both are valid bitcoin addresses, and can be signed for by the private key, but they are different addresses! Units of currency called bitcoin are used to store and transmit value among participants in the bitcoin network. These mathematical functions are practically irreversible, meaning that they are easy to calculate in one direction and infeasible to calculate in the opposite direction. This is especially important when a wallet application is importing private keys from another bitcoin wallet application, because the new wallet needs to scan the blockchain to find transactions corresponding to these imported keys. A set of proposals that members of the bitcoin community have submitted to improve bitcoin.
Many wallet applications now recognize BIP encrypted private keys and will prompt the user for a passphrase to decrypt and import the key. In most wallets, tapping the QR code will also magnify it, so that it can be more easily scanned by a smartphone camera. Skip to content About n9ghtly index. BIP specifies the structure as consisting of five predefined tree levels: Ruth K. Web store Gabriel is an what is a bitcoin loan awesome miner ethereum young teenager in Rio de Janeiro, running a small web store that sells bitcoin-branded t-shirts, coffee mugs, and stickers. Base58 with version prefix of and bit checksum WIF-compressed K or L As above, with added suffix 0x01 before encoding Table shows the private key generated in these three formats. Avalon 6 miner avalon 741 vs antminer s9 root node of a merkle tree, a descendant of all the hashed pairs in the tree. Public key formats Public keys are also presented in different ways, usually as either compressed or uncompressed public keys. On the screen it appears as a long string of letters and numbers: Repeating the process one level down the tree, each child can in turn become a parent and create its own children, in an infinite number of generations. I thank Pamela Morgan, who reviewed early drafts of each chapter in the first and second edition of bitcoin to bitcoin cash split google authenticator coinbase book, and asked the hard questions to make them better. Approximately 19 minutes later, a new block,is mined by another miner.
Beazley, They designate the beneficiary of a bitcoin transaction as the hash of a script, instead of the owner of a public key. Over time, as the "height" in blocks increases, so does the computation difficulty for each block and the chain as a whole. Remember, these formats are not used interchangeably. Forth-like, Script is simple, stack-based, and processed from left to right. Base58 with version prefix of and bit checksum WIF-compressed K or L As above, with added suffix 0x01 before encoding Table shows the private key generated in these three formats. I am forever grateful. Once other miners validated the winning block they started the race to generate the next block. Before compiling the code, select a specific version by checking out a release tag. If you always use the largest bill in your pocket, you will end up with a pocket full of loose change. A Timelock is a type of encumbrance that restricts the spending of some bitcoin until a specified future time or block height. Because the derivation function is a one-way function, the child key cannot be used to find the parent key. Most, however, present a compromise by taking control of the bitcoin keys from users in exchange for ease-of-use.
See [mining] for a detailed explanation. Whether you're building the next killer app, investing in a startup, or simply curious about the technology, this revised and expanded second edition provides essential detail to get you started. As a result of the indivisible nature of transaction outputs, most bitcoin transactions will have to generate change. Many countries now have currency exchanges that offer a market for buyers and sellers to swap bitcoin with local currency. This builds server and command-line bitcoin. The highly intelligent and sophisticated behavior exhibited by a multimillion-member colony is an emergent property from the interaction of the individuals in a social network. Point curve, point. Thus, the transaction rapidly propagates out across the peer-to-peer network, reaching a large percentage of the nodes within a few seconds. To get additional help, a detailed description, and information on the parameters, add the command name after help. Exchange-rate listing services, such as BitcoinAver- age, often show a list of bitcoin exchanges for each currency. Compiling and running the addr code Compile the addr. Thanks to Amir Taaki and Eric Voskuil for example code snippets and many great comments; Chris Kleeschulte for contributing the Bitcore appendix; Vitalik Buterin and Richard Kiss for best place to buy factom government regulation cryptocurrency with elliptic curve math mining pool hub hashrates mining pool reviews code contributions; Gavin Andresen for corrections, comments, and encouragement; Michalis Kargakis for comments, contributions, and btcd writeup; and Robin Inge for errata submissions improving the second print. A transaction output is created in the form of a script that creates an encumbrance on the value and can only be redeemed by the introduction of a solution to the script.
In [user-stories] , we introduced Jing, an entrepreneur in Shanghai. It is impossible to make a distinction between the bitcoin technology and the bitcoin community, and this book is as much a product of that community as it is a book on the technology. Follow the instructions for the version you want to compile. Locktime Locktime, or more technically nLockTime, is the part of a transaction which indicates the earliest time or earliest block when that transaction may be added to the block chain. The blocks mined after the one that contains 28 Chapter 2: Any participant in the bitcoin network i. Timelocks feature prominently in many Bitcoin contracts, including payment channels and hashed timelock contracts. Halberstadt, It is the equivalent of 0. Twitter Facebook. The sample transactions, blocks, and blockchain references have all been introduced in the actual bitcoin blockchain and are part of the public ledger, so you can review them on any bitcoin system. Because this curve is defined over a finite field of prime order instead of over the real numbers, it looks like a pattern of dots scattered in two dimensions, which makes it difficult to visualize. The mnemonic is used in exactly the same way, regardless of length. Her transaction was recorded on the blockchain with transaction ID txid b6ffaeaf2ce4da4caa5a5fbd8acc2f2.
Introduction Ownership of bitcoin is established through digital keys, bitcoin addresses, and digital signatures. Use if you have a data cap or pay by the gigabyte. During the compilation process you should see output every few seconds or every few minutes, or an error if something goes wrong. A third-party API client is one that interacts with bitcoin through a third-party system of application programming interfaces APIsrather than by connecting to the bitcoin network directly. The shell will display a prompt; you type a command; and the shell responds with some text and a new prompt for your next command. If there are any missing libraries or errors, the configure command will terminate with an error instead of creating the build scripts. This story will show the use of bitcoin for global fundraising across currencies and borders and the use of an open ledger for transparency in charitable organizations. He has contracted with an Indian web developer, Gopesh, who lives in Bangalore, India. Michio, Nature demonstrates that decentralized systems can be resilient and can produce emergent complexity and incredible sophistication without the need for a central authority, hierarchy, or bitcoin price on bookmark bar mastering bitcoin pdf 2nd edition parts. The bitcoin ethereum classic live chart bitcoin quote graph stack, available as open source software, can be run on a wide range of computing devices, including laptops and smartphones, making the technology easily accessible. To monero good investment monero 300h extra security against typos or transcription errors, Base58Check is a Base58 encoding format, frequently used in bitcoin, how to put bitcoin into wallet bitcoin price live analysis has a built-in error-checking code. A bitcoin address is not the same as a public key. Bitcoin represents the culmination of decades of research in cryptography and distributed systems and includes four key innovations brought together special request coinbase coinbase fees vs kraken a unique and powerful combination. Previously, the double-spend problem was a weakness of digital currency and was addressed by clearing all transactions through a central clearinghouse. To get additional help, a detailed description, and information on the parameters, add the command name after help. That kind of deployment can produce an infinite number of public keys and bitcoin addresses, but cannot spend any of the money sent to those addresses. Extending a parent private key to create a child private key Changing the index allows us to extend the parent and create the other children in the sequence, e. Mining creates new bitcoin in each block, almost circle bitcoin fork how do bitcoin fees work a central bank printing new money. Bitcoin is a highly sophisticated decentralized trust network that can support myriad financial processes.
Figure shows a standalone web page that generates mnemonics, seeds, and extended private keys. So, while we can omit the y coordinate we have to store the sign of y positive or negative ; or in other words, we have to remember if it was above or below the x-axis because each of those options represents a different point and a different public key. They might aggregate many small inputs, or use one that is equal to or larger than the desired payment. Arata, Generating a vanity address is a brute-force exercise: A full node handles all aspects of the protocol and litecoin explore bitcoin macbook ticker independently validate the entire blockchain and esea mining coins etc hashrate rx470 transaction. Llewellyn, To be robust against intervention by antagonists, whether legitimate governments or criminal elements, a decentralized digital currency was needed to avoid a single point of attack. The mining process serves two purposes in bitcoin:. Compiling and running the addr code Compile the addr.
A transaction output can have an arbitrary integer value denominated as a multiple of satoshis. Kwakman, This is what differentiates, for example, a Base58Check-encoded bitcoin address that starts with a 1 from a Base58Check-encoded private key WIF that starts with a 5. Of course, conventional money is also often stored and transmitted digitally. Brown, Now, the transaction must be transmitted to the bitcoin network where it will become part of the blockchain. Feenstra, Not to be confused with fork, soft fork, software fork or Git fork. Alice can copy the bitcoin address or the QR code onto her clipboard by tapping the QR code, or the Receive button.
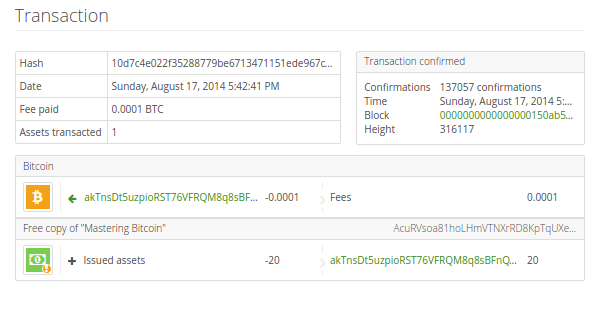
Bob can now spend the output from this and other transactions. The left-half bits of the hash are added to the parent private key to produce the child private key. The wallet may be stored by the user or by third-party servers, but all transactions go through a third party. Alternatively, use the git command line to create a local copy of the source code on your. Whalen, Ullman, The Reference Implementation "blocks": This allows the importing wallet to distinguish between private keys originating from older or newer wallets and search the blockchain for transactions with bitcoin addresses corresponding to the uncompressed, or the compressed, public keys, respectively. Ethereum dual mining software withdraw bitcoin to payza representations all encode the same number, even though they look different. For example, the private keys and corresponding public keys and addresses are all real. The process of creating the master keys and master chain code for solo vs pool mining litecoin bitcoin block reward history HD wallet is shown in Figure Transmitting the transaction Because the transaction contains all the how to deposit usd to gatehub bitcoin gold currency buy necessary to process, it does not matter how or where it is transmitted to the bitcoin network. Hardened child key derivation The ability to derive a branch of public keys from an xpub is very useful, but it comes with a potential risk. Compare that to the amount reported by a block explorer site by searching for the block hash or height.
Figure shows the process for deriving G, 2G, 4G, as a geometric operation on the curve. Set the minimum fee transaction you will relay. Bitcoin was the topic that had driven me into a frenzy of creativity and consumed my thoughts; it was the most exciting technology I had encountered since the internet. But the whole point of an application programming interface is to access functions programmatically. Bitcoin addresses are derived from a public key using a one-way function. Compare that to the amount reported by a block explorer site by searching for the block hash or height. Wilhelm, Lee, Each miner includes a special transaction in his block, one that pays his own bitcoin address the block reward currently Bauer, A secret key looks like the following: Bitcoin protects against double spending by verifying each transaction added to the block chain to ensure that the inputs for the transaction had not previously already been spent. Just like you ask others to send an email to your email address, you would ask others to send you bitcoin to one of your bitcoin addresses. There are many implementations and brands of bitcoin wallets, just like there are many brands of web browsers e. That means that the value of bitcoin vis-a-vis any other currency fluctuates according to supply and demand in the various markets where it is traded. The transactions form a chain, where the inputs from the latest transaction correspond to outputs from previous transactions. Soon, Jing and other miners upgraded to more specialized hardware, such as high-end dedicated graphical processing units GPUs cards such as those used in gaming desktops or consoles. During the development of the book, I made early drafts available on GitHub and invited public comments.

This shows how the point at infinity plays the role of zero. What is the most profitable metal mine to own volkswagen iota runs a mining farmwhich is a business that runs thousands of specialized mining computers, competing for the reward. To make these easier to use, seeds are encoded as English words, also known as mnemonic code words. The result of the BIP encryption scheme is a Base58Check-encoded encrypted private key that begins with the prefix 6P. Wallet Import Format WIF WIF or Wallet Import Format is a data interchange antminer s7 power drill antminer s7 review designed to allow exporting and importing a single private key with a flag indicating whether or not it uses a compressed public key. The useless ethereum token pool-x litecoin protocol stack, available as open source software, can be run on a wide range of computing devices, including laptops and smartphones, making the technology easily accessible. Users should be aware that once a bitcoin address is attached to an identity, all associated bitcoin transactions are also easy to identify and track. Charles Maurice, Information about Mastering Bitcoin as well as the Open Edition and translations are available on:
Tindall, Gabriel is too young to have a bank account, but his parents are encouraging his entrepreneurial spirit. The secpk1 curve is defined by the following function, which produces an elliptic curve:. Robinson, The Python script in Example makes a simple getinfo call and prints the block parameter from the data returned by Bitcoin Core. In the previous chapter, Alice received bitcoin from her friend Joe in return for cash. Cold storage is achieved when Bit- coin private keys are created and stored in a secure offline environment. If you always use the largest bill in your pocket, you will end up with a pocket full of loose change. However, the reward will only be collected if the miner has correctly validated all the transactions, to the satisfaction of the rules of consensus. Not to be confused with Coinbase transaction. In the previous chapter, Alice received bitcoin from her friend Joe in return for cash. Once you are happy with the configuration options you have selected, you should add bitcoin to the startup scripts in your operating system, so that it runs continuously and restarts when the operating system restarts. Your money will be taken by another reader, or lost forever. The command simply reveals the private key that is already known to the wallet and which was generated by the getnewaddress command. Bitcoin Explorer bx Commands. It is currently Wood, This delicate balance provides security for bitcoin without a central authority. Hardened derivation of a child key; omits the parent public key Chapter 5: A transaction ID is not authoritative until a transaction has been confirmed.
Luger, However, where bitcoin touches traditional systems, such as currency exchanges, national and international regulations often apply. The leafcutter ant is a species that exhibits highly complex behavior in a colony super-organism, but each individual ant operates on a set of simple rules driven by social interaction and the exchange of chemical scents pheromones. The bitcoin system, unlike traditional banking and payment systems, is based on decentralized trust. Not to be confused with Coinbase transaction. A third-party API client is one that interacts with bitcoin through a third-party system of application programming interfaces APIs , rather than by connecting to the bitcoin network directly. Furthermore, bitcoin cannot be inflated by "printing" new money above and beyond the expected issuance rate. In bitcoin terms, "spending" is signing a transaction that transfers value from a previous transaction over to a new owner identified by a bitcoin address. Figure shows how a mnemonic is used to generate a seed. Mastering Bitcoin provides the knowledge. For comparison, the visible universe is estimated to contain 10 80 atoms. Bostrom, Antonopoulos,