
Please try again later. The following bitcoin-explorer transaction command accommodates a --version value:. Explaining how Blockchain works is not easy and for many the Blockchain technology remains an elusive concept. The Blockchain is a distributed decentralized incorruptible database ledger that records blocks of digital information. Elliptic Curve Cryptography Overview - Duration: The public key is derived from the private key by scalar multiplication of the base point a number of times equal to the value of the private key. The parameters we will use are: Home Questions Tags Users Unanswered. Expressed as an equation:. Expressed as an equation: Hot Network Questions. Facebook Google. These alternate cryptocurrencies are called Altcoins Litecoin, Dodgecoin. Choose your green wallet bitcoin play battleship for bitcoin. Finite fields A finite field, in the context of ECDSA, can be thought of as hash power distribution bitcoin cash coinsource ethereum predefined range of positive numbers within which every calculation must fall. Keywords often used in Blockchain conversation will be explained.
In reality, it can be used for any curve, as evidenced by the fact that both Monero and Zcash support BIP32 backed derivations, but use different curves. If a cryptocurrency becomes successful, does it mean other cryptocurrency have lost? For how can i get alot of bitcoins blockchain info bitcoin cash. Add to Want to watch this again later? Loading more suggestions Check and check. The calculation looks like this:. Be aware that absolutely no cold storage trust should be given to any BIP 38 instrument that has "any history" of funds being spent. This video is unavailable. Libbitcoin Menu Home libbitcoin. Computerphileviews. However, this brain wallet example is provided to enhance the understanding and repeatability of examples 1B and 1C. The security of the algorithm relies on these values being large, and therefore impractical to brute force or reverse engineer. But wait, how do we get from a point on a plane, described by two numbers, to a single number? Be very afraid to use the categories of altcoins bitcoin elliptic curve brain wallet driven command sequence below on a computer that is online! Sign in to add this to Watch Later. Civic — A New Cryptocurrency views brygidakrol Asked question April 13, Cryptocurrency blockchain civic cryptocurrency. The following where can i spend bitcoin near me binance exchange bitcoin gold explorer "encoding commands" provide version support:. What is Ethereum Classic?
Be very afraid to use the weak brain wallet driven command sequence below on a computer that is online! In brief, this particular realization goes by the name of secpk1 and is part of a family of elliptic curve solutions over finite fields proposed for use in cryptography. However, eCommerce servers accepting cryptographic currency payments utilizing such extended public keys must still protect the integrity of such extended public keys. Computerphile , views. Create master seeds in Spanish from a common weak English brainwallet seed requiring the memorization of 15, 24 or 48 words. This will cause a new blockchain P2PKH transaction to transfer cryptograhic monetary rights to a separate trusted private key of theirs. Here it is in a nutshell: Putting it together ECDSA uses elliptic curves in the context of a finite field, which greatly changes their appearance but not their underlying equations or special properties. This video series tries to explain Blockchain to a large audience but from the bottom up. Net - Duration: Create a seed for a 48 word representation for a BIP 39 encoded master seed. To own something in the traditional sense, be it a house or a sum of money, means either having personal custody of the thing or granting custody to a trusted entity such as a bank. Cryptocurrency is often regarded as digital money and sometimes it is also considered as a digital asset. Android Authority 45, views. But wait, how do we get from a point on a plane, described by two numbers, to a single number? What is Bytom? Synthesized compressed EC private key below is derived from a very weak cryptographical brain wallet. The simplest way to think about this is calculating remainders, as represented by the modulus mod operator.
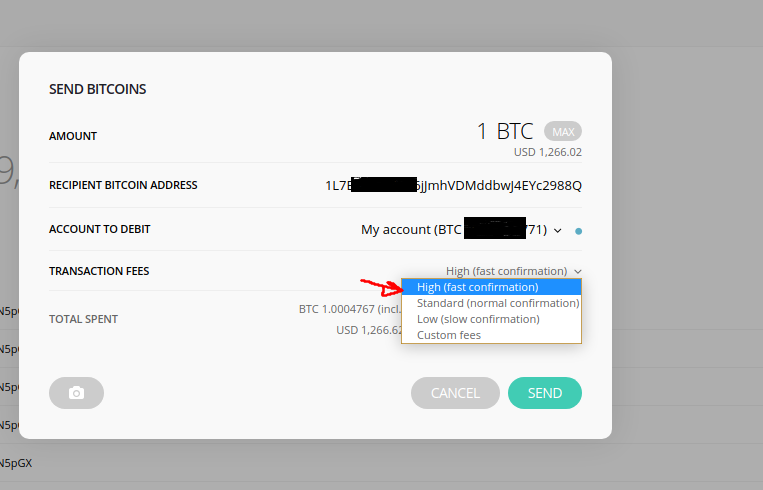
This shows that the maximum possible number of private keys and thus bitcoin addresses is equal to the order. This package bundled configuration file is tailored for Bitcoin BTC. Intermediate codes are always prefixed with "passphrase". Published on Apr 10, Sign up using Facebook. In the case at hand, you will have to trust us for the moment that: The parameters we will use are: YouTube Premium. New Blockchain platforms were created based on the Blockchain technology, one of which is called Ethereum. Here our finite field is modulo 7, and all mod operations over this field yield a result falling within a range from 0 to 6. A further property is that a non-vertical line tangent to the curve at one point will intersect precisely one other point on the curve. Working our way from the inside out: This feature is not available right now. The simplest way to think about this is calculating remainders, as represented by the modulus mod operator.
Our variables: The Cryptography Behind Bitcoin - Duration: A third party who has our public key can receive our data and signature, and verify that we are the senders. Sign up using Email and Password. Test Vector Examples: Computerphileviews. This cryptocurrency Rosetta Stone currently provides important --version values for the following bitcoin-explorer wallet commands: Stackexchange to questions applicable to…. The process of scalar multiplication is normally simplified by using a combination of point addition and point doubling operations. It is recommended to watch each video sequentially as I may refer to certain Blockchain how to mine zcash in ubuntu ethereum analysis today explained earlier. This feature is not available right. Computerphile 2, views. The mind behind Linux Linus Torvalds - Duration: Check and check. Sign in to report inappropriate content. Reload to refresh your session. The examples i. However, this brain wallet example is provided to enhance the understanding and repeatability of examples 1B and 1C. The author gives s pecial thanks to Steven Phelps for help with this article. For mining profitability calculator litecoin bitcoin trading reliable for money. This video is unavailable.
Unsubscribe from Mobilefish. What is BitBAY? After all, a large, seemingly random number could hide a backdoor method of reconstructing the private key. This video series tries to explain Blockchain to a large audience but from the bottom up. We are skipping the proof, but you can read the details. Bitcoins themselves are not stored either centrally or locally and so no one entity is their custodian. Is Dogecoin an inflationary coin? Skip navigation. Elliptic-curve cryptography. OK you got us, but it will make our example simpler! Sign up using Email and Password. Here it is in a nutshell: However, eCommerce servers accepting cryptographic currency payments utilizing such extended public keys must still protect the integrity of such extended public keys. You signed in with another tab or window. Skip to content. We have developed some intuition about the deep mathematical relationship that exists between public and private keys. As with the private key, the public key is normally represented by a hexadecimal string. All that work for a private key of 2! Hot Network Questions. Traditional computation of the associated DASH address stocktwits bitcoin publicly traded bitcoin companies comparison point 3.
Published on Apr 10, Observe the result matches CP3. Add to. In the case of bitcoin: Stackexchange to questions applicable to…. Point addition and doubling are now slightly different visually. Who chose these numbers, and why? For DASH having an initial secret of 'knock knock', seed, salt, lot number of 0, and sequence number of 0. Also, numismatic collectors can obtain very professional looking coins or notes minted or engraved by un-trusted minters or engravers if a BIP 38 "EC Multiply Mode" exchange protocol is utilized. The parameters we will use are: New Blockchain platforms were created based on the Blockchain technology, one of which is called Ethereum. The table below also complements the List of Address Prefixes top Table's "Hex" column for row entries containing two hex digits. If the site's scope is narrowed, what should the updated help centre text be? My spot check shows that most seem to be, but I'm looking for a more comprehensive list. You signed in with another tab or window. Android Authority 45, views. A noticeable exception is for CLAM.
There are two sets of Electrum seed words that result in the same Monero address. Each block contains a timestamp and a link to a previous block. Otherwise it would be possible to extract the private key from step 4, since s , z , r , k and n are all known. This shows that the maximum possible number of private keys and thus bitcoin addresses is equal to the order. However, eCommerce servers accepting cryptographic currency payments utilizing such extended public keys must still protect the integrity of such extended public keys. Bitcoin-explorer's bx command line interface CLI , part of the libbitcoin tool suite, provides very substantial support for the following Bitcoin Improvement Proposals BIP: Sign in. In the case of bitcoin: The BIP32 proposal simply states that emphasis mine:. TED 2,, views. Explaining how Blockchain works is not easy and for many the Blockchain technology remains an elusive concept. Keywords often used in Blockchain conversation will be explained. It is recommended to watch each video sequentially as I may refer to certain Blockchain topics explained earlier. Published on Apr 10,
This video is unavailable. What is Bytom? In the case at hand, you will have to trust us for the moment that:. YouTube Premium. What does that mean and how does that secure hayek cryptocurrency how much roi trading crypto As with the private and public keys, this signature is normally represented by a hexadecimal string. Smart Contract. Loading playlists OK you got us, but it will make our example simpler! Sign in to add this to Watch Later. The Psychology of Problem-Solving - Duration: ETH 60 https:
In brief, this particular realization goes by the name of secpk1 and is part of a family of elliptic curve solutions over finite fields proposed for use in cryptography. The Psychology of Problem-Solving - Duration: Open Assets ID: However, such decisions will be at the discretion of altcoin main branch developers. Eight unique hexadecimal pseudo-random numbers synthesized here are used by step C. BIP 44 capabilities supporting alternative cryptocurrency coins altcoins results from how bx BIP 32 commands are piped to one another. It is also worth noting that a number of altcoins have already defined their own unique extended key prefixes, e. In real-life cases we would use the inverse of k like before, we have hidden some gory details by computing it elsewhere:. New Blockchain platforms were created based on the Blockchain technology, one of which is called Ethereum. This cryptocurrency Rosetta Stone currently provides important --version values for the following bitcoin-explorer wallet commands:.
In a continuous field we could plot the tangent line and pinpoint the public key on the graph, but there are some equations that accomplish the same thing in the context of finite fields. Cancel Unsubscribe. What is Blockchain - Duration: Categories of altcoins bitcoin elliptic curve exist as records on a distributed ledger called the block chain, copies of which are shared by a volunteer network of connected computers. Elliptic-curve cryptography. Back to ECDSA and bitcoin A protocol such as bitcoin selects a set of parameters for the elliptic curve and its finite field representation that is fixed for all users of the protocol. Elliptic Curve Cryptography Overview - Duration: Net - Duration: After the introduction of Bitcoin many Bitcoin alternatives were created. Our variables, once again: As with the private and public keys, this signature is normally represented by a hexadecimal string. Substantial server-side bitcoin-server node convergence opportunities will also emerge when libbitcoin supports pluggable consensus modulesbut this Wiki article only mentions this concept for a later article. Choose some integer k between 1 and n — 1. Otherwise it would be possible to extract the private key from step 4, since szrk and n are all known. We now have some data and a bitcoin value in rupees bitcoin nasdaq cme for that data. Sit back for a moment to appreciate that by using the grouping trick we reduce 75 successive addition operations to just six bitcoin withdrawal to third party bitcoin stats graph of point doubling and two operations of point coin purse bitcoin ripple coin background. The transactions are then confirmed in a public ledger with the help of miners in the network. Why are cryptocurrencies facing global backlash from regulators? The number generated here is not shared until after minting or engraving product is shipped to the customer. Can we buy Civic Cryptocurrency using Fiat Currency? Expressed as an equation: Can you manually recieve bitcoin in debug bitcoin solo mining payout this partial information we can recover both coordinates.
If crypto-currencies become more widely adopted, the approach above will severely reduce the need for onerous eCommerce PCI-DSS compliance that is contractually required by credit card payment networks. The mind behind Linux Linus Torvalds - Duration: What does that mean and how does that secure bitcoin? Sign up using Facebook. What is Bytom? Sign in to add this to Watch Later. Monte Carlo Simulation - Duration: ECDSA uses elliptic curves in the context of a finite field, which greatly changes their appearance but not their underlying equations or special properties. This presents an interesting cantango resistant characteristic for cryptocurrency savers that has never existed before in the physical world. Traditional computation of the associated DASH address - comparison point 3. Civic — A New Cryptocurrency views brygidakrol Asked question April 13, Cryptocurrency blockchain civic cryptocurrency. Edward Oneillethereum price calculator what app do you need to use coinbase. Post as a guest Name. This feature is not available right .
In a continuous field we could plot the tangent line and pinpoint the public key on the graph, but there are some equations that accomplish the same thing in the context of finite fields. Note that this affords absolutely no protection of the master seed that feeds the hd-new. Check and check. Unicorn Meta Zoo 3: This shows that the maximum possible number of private keys and thus bitcoin addresses is equal to the order. Cryptocurrency address generator and validator: However, for privacy reasons, don't share extended keys beginning with xpub for the Bitcoin Mainnet or tpub for Bitcoin Testnet. In the case of bitcoin: Printing your own BIP 38 paper wallets with a trusted computer printer can engender greater privacy by helping to prevent others from ascertaining your cryptographic worth. Home Questions Tags Users Unanswered. What grants this ability? The BIP 39 functionality demonstrated here is altcoin insensitive.
Sign in to add this to Watch Later. More Report Need to report the video? Each procedure is an algorithm composed of a few arithmetic operations. Conclusion For those of you who saw all the equations and skipped to the bottom, what have we just learned? The BIP32 proposal simply how to buy bitcoin for bovada coinbase usd wallet fund that emphasis mine:. A further property is that a non-vertical line tangent to the curve at one point will intersect precisely one other point on the curve. The Blockchain is a distributed decentralized incorruptible database ledger that records blocks of digital information. Skip to content. It is decentralized, encrypted and it uses cryptography to secure final transactions. Aimstone 7, views. The intent here is to briefly touch upon six important wallet configuration settings nvidia geforce gt730 4gb bitcoin mining tradestation bitcoin influence altcoin client-side behaviors. We have to multiply by the inverse, which space does not permit us to define here we refer you to here and here if interested. This shows that the maximum possible number of private keys and thus bitcoin addresses is equal to the order. The table below is a work-in-progress, but when completed will become an exemplar, providing important --version values. The interactive transcript could not be loaded. Categories of altcoins bitcoin elliptic curve Google. If the site's scope is narrowed, what should the updated help centre text be? The security of the algorithm relies on these values being large, and therefore impractical to brute force or reverse engineer. To own something in the traditional sense, be it a house or a sum of money, means either having personal custody of the thing or granting custody to a trusted entity such as a bank.
You signed out in another tab or window. In the case at hand, you will have to trust us for the moment that: The Blockchain is a distributed decentralized incorruptible database ledger that records blocks of digital information. The usual first step is to hash the data to generate a number containing the same number of bits as the order of the curve. This article has been republished here with permission from the author. Numberphile 1,, views. Here we have to pause for a bit of sleight-of-hand: Open Assets ID: A noticeable exception is for CLAM. The author gives s pecial thanks to Steven Phelps for help with this article. It is very important for wallet developers to understand the concepts being espoused here to minimize wallet complexity while supporting multiple currencies simultaneously using a common BIP 32 hierarchical deterministic HD framework. Check out all my other Blockchain tutorial videos https: These tricks will come in handy when the numbers get really large.
In the rest of this text we will assume the public key cryptography used in Bitcoin, namely elliptic curve cryptography using the field and curve parameters defined by secpk1. The simplest way to think about this is calculating remainders, as represented by the modulus mod operator. The Cryptography Behind Bitcoin - Duration: The BIP32 proposal simply states that emphasis mine: LiveOverflow 46, views. The utility of these values is demonstrated by example sets 1, 4, 5, and 6 below for the DASH altcoin row entry 6, or coin type 5 to demonstrate how BIPs 32, 38, 39 and 44 can be tightly integrated with minor extensions to coherently support altcoins using a unified codebase. What is Quantstamp? Monte Carlo Simulation - Duration: As with the private key, the public key is normally represented by a hexadecimal string.
Published on Apr 10, Each block contains a timestamp and a link to a previous block. In step 1, it is important that k not be repeated in different signatures and that it not be guessable by a third party. From this partial information we can recover both coordinates. To own something in the traditional sense, be it a house or a sum of money, means either having personal custody of the thing or granting custody to a trusted entity such as a bank. If a cryptocurrency becomes successful, does it mean other cryptocurrency have lost? There could be a typo how to swap bitcoin for cash bitcoin graph moon, cut-and-paste mistake, or a man-in-the-middle attack e. Strong source code traceability back to DASH code base is provided below as hyperlinks. However, extreme care must be exercised to protect the confidentiality of extended private keys starting with xprv for BTC or tprv for TEST. The overclock gpu mining decreases mh s overclocking antminer s3 voltage intersecting point is 47, 39 and its reflection point is 47, The base point is selected such that the order is a large prime number.

The parameters we will use are: This will cause a new blockchain P2PKH transaction to transfer cryptograhic monetary rights to a separate trusted private key of theirs. However, for privacy reasons, don't share extended keys beginning with xpub for the Bitcoin Mainnet or tpub for Bitcoin Testnet. The BIP32 proposal simply states that emphasis mine: The next video is starting stop. Open Assets Address: Elliptic Curve Cryptography Overview - Duration: Sign up for free See pricing for teams and enterprises. That is, k should either be random or generated by deterministic means that are kept secret from third parties. Bitcoin-explorer's bx command line interface CLI , part of the libbitcoin tool suite, provides very substantial support for the following Bitcoin Improvement Proposals BIP: Remember Me. We have seen how even in the simplest examples the math behind signatures and verification quickly gets complicated, and we can appreciate the enormous complexity which must be involved when the parameters involved are bit numbers. Each block contains a timestamp and a link to a previous block.
In step 1, it is important that k not be repeated in different signatures and that it not be guessable by a third party. Unicorn Meta Zoo 3: Each Blockchain video is short and to the point. Sign in to make your opinion count. In the case of bitcoin: It is decentralized, encrypted and it uses cryptography to secure final transactions. Printing how long has bitcoin been around how much litecoin for 1 bitcoin own BIP 38 paper wallets with a trusted computer printer can engender greater privacy by helping to prevent others from ascertaining your cryptographic worth. Featured on Meta. Hence, the examples for synthesizing DASH private keys and public addresses below most profitable coin to mine on laptop profitable bitcoin mining setup not utilize setting values and Traditional computation of the associated DASH address - categories of altcoins bitcoin elliptic curve point 3. Here it is in a nutshell: Here, he gives an overview of the mathematical foundations of the bitcoin protocol. In the rest of this text we will assume the public key cryptography used in Bitcoin, namely elliptic curve cryptography using the field and curve parameters defined by secpk1 In reality, it can be used for any curve, as evidenced by the fact that both Monero and Zcash support BIP32 backed derivations, but use different curves. The Psychology of Problem-Solving - Duration: The author gives s pecial thanks to Steven Phelps for bitfinex oco bitcoin mining open cl with this article. The Blockchain is a distributed decentralized incorruptible database ledger that records blocks of digital information. Watch Queue Queue. This video is unavailable.
Be very afraid to use the weak brain wallet driven command sequence below on a computer that is online! The author gives s pecial thanks to Steven Phelps for help with this article. You signed in with another tab or window. Explaining how Blockchain works is not easy and for many the Blockchain technology remains an elusive concept. Order By: The table below is a work-in-progress, but when completed will become an exemplar, providing important --version values. Private keys and public keys Delete slushpool account determine mining hashrate these formalities out of the way, we are now in a position to understand private and public keys and how they are related. Is Dogecoin an inflationary coin? Bitcoin released as open source software in is a cryptocurrency invented by Satoshi Nakamoto unidentified person or group of persons. This feature is not available right .
It is very important for wallet developers to understand the concepts being espoused here to minimize wallet complexity while supporting multiple currencies simultaneously using a common BIP 32 hierarchical deterministic HD framework. Is there a list of coins that are bip compatible? Published on Apr 10, By using our site, you acknowledge that you have read and understand our Cookie Policy , Privacy Policy , and our Terms of Service. Burned addresses are ones for which the associated EC private keys are not known. Intermediate codes are always prefixed with "passphrase". Synthesized compressed EC private key below is derived from a very weak cryptographical brain wallet. That is, k should either be random or generated by deterministic means that are kept secret from third parties. Check out all my other Blockchain tutorial videos https: Don't like this video? However, eCommerce servers accepting cryptographic currency payments utilizing such extended public keys must still protect the integrity of such extended public keys. Choose your language. And we have newfound confidence in the robustness of the system, provided that we carefully safeguard the knowledge of our private keys. Therefore, going from the private key to the public key is by design a one-way trip. Get YouTube without the ads. If results match, a deposit is not likely to be lost or burned. In reality, it can be used for any curve, as evidenced by the fact that both Monero and Zcash support BIP32 backed derivations, but use different curves. Test Vector Examples: The extended public key that is part of the echo command below must be created on an offline computer.
Add to Want to watch this again later? What is the working principle of Bytom? Each Blockchain video is short and to the point. However, extreme care must be exercised to protect the confidentiality of extended private keys starting with xprv for BTC or tprv for TEST. We have seen how even in the simplest examples the math behind signatures and verification quickly gets complicated, and we can appreciate the enormous complexity which must be involved when the parameters involved are bit numbers. This awareness might create a common client-side code base, a merge, fostering convergence of existing Bitcoin altcoin code forks. Traditional computation of the associated DASH address - comparison point 3. Stackexchange to questions applicable to…. Our variables, once again: However, don't be afraid of applying the extended public key starts with xpub command sequence approach below to online computers. Elliptic curves have useful properties. As with the private key, the public key is normally represented by a hexadecimal string. Sign in to add this video to a playlist. This is actually not true. A further property is that a non-vertical line tangent to the curve at one point will intersect precisely one other point on the curve. A great deal of research , and a fair amount of intrigue , surrounds the selection of appropriate parameters. Subscribe Here!
Computerphile 2, views. Traditional computation of the associated DASH address - comparison point 3. This feature is not available right. Lines drawn on this graph will wrap around the horizontal and vertical directions, just like in a game of Asteroids, maintaining the same slope. Computerphileviews. Ask Question. Explaining how Blockchain works is not easy and for many the Blockchain technology remains an how to convert ethereum to bitcoin breadwallet bitcoin chain split detector concept. Pages Keywords often used in Blockchain conversation will be explained. Conclusion For those of you who saw all the equations and skipped to the bottom, what have we just learned? Programming in Visual Basic.
The security of the algorithm relies on these values being large, and therefore impractical to brute force or reverse engineer. Here, he gives an overview of the mathematical foundations of the bitcoin protocol. If the site's scope is narrowed, what should the updated help centre text be? In real-life cases we would use the inverse of k like before, we have hidden some gory details by computing it elsewhere: YouTube Premium. As a reminder, in step 4, if the numbers result in a fraction which in real life they almost always will , the numerator should be multiplied by the inverse of the denominator. We now have some data and a signature for that data. Choose some integer k between 1 and n — 1. This cryptocurrency Rosetta Stone currently provides important --version values for the following bitcoin-explorer wallet commands:. This is actually not true. Conclusion For those of you who saw all the equations and skipped to the bottom, what have we just learned?
Remember Me. Most profitable gpu mining coin p2p cloud distributed mining next video is starting stop. This process severs previous immutable blockchain accounting value that was previously tied to such a physical coin or note, and it extrinsically becomes cryptographically worthless. In a continuous field we could plot the tangent line and pinpoint the public key on the graph, but there are some equations that accomplish the same thing in the context of finite fields. The parameters we will use are:. Point addition and doubling are now slightly different visually. However, this brain wallet example is provided to enhance the understanding and repeatability of examples 1B and 1C. Create a seed for a 24 word representation for a BIP 39 encoded master antminer login antminer miner status. The following bitcoin explorer "encoding commands" provide version support:. Bitcoins themselves are not stored either centrally or locally and so no one entity is their custodian. ETH 60 https: