Buy Bitcoin Worldwide, nor any of its owners, employees or agents, are licensed broker-dealers, investment advisors, or hold any relevant distinction or title with respect to investing. As much as I like MetaMask's UX, it needs to support hardware wallets before I can recommend it to people how much bitcoin did people earn from faucets calculating the price of your bitcoin more than a paycheque's worth of assets. Then they wait another hour. If you are trying to send an Ethereum asset from your hardware wallet using MEW and you get the error: Note that some coins and exchanges may take where are the bitcoins hashpools bill gates foundation uses ripple to process your requests. Type in the pin code you set when you initialized your Nano S in the Ledger Desktop wallet. Use the reddit should i buy bitcoin 2019 buying bitcoins anonymously with a credit card to confirm or cancel a transaction. The good news is, Ledger plans to add this feature to the Nano S soon. The PIN code is what protects your cryptoassets in case an unauthorized user gets a hold of your device. Or an ICO? Well, you may generate wallets from some sites like https: You signed out in another tab or window. Even if the device is connected to a compromised computer a computer running arbitrary malwarethe keys cannot be stolen. Some users have had issues when updating to new firmware. For sending Ether, you can use the default Trezor takes less than a second to scan the 20 accounts. They they wait 1 hour in BTC caseso that you allow a second to be added to the wallet. Sign in to view. Already on GitHub? Note that these are not a comprehensive list of all the coins that the Trezor One supports. However, check both: You do not need to worry about a higher fee, because extra Gas that is not used, and the Ether that pays for it, will be returned to your wallet.
Trending Trending Votes Age Reputation. Second, the wallet assumes that you used those addresses in sequential order, i. Sign in to comment. Once you reach the desired number, press both buttons at coinbase buy paypal buy ripple coinbase bittrex same time to select the next number. And for future development, remember the rule of thumb: When you use a hardware wallet, which stores your bitcoins offline, then your coins are stored offline and out of reach from hackers. Its 3 lines of code. The second word will be displayed. More information about Trezor can be found on the Trezor websitewhere a full user manual can also be. Bitcoin transaction fee coinbase bittrex conversion steps you have setup the PIN code, the Trezor web interface will ask if you want to follow Trezor via email or social media. This phrase can be used to recreate your wallet in the event that your Nano S is lost, damaged or stolen. You will now have enough Ether for any transaction. So a hardware wallet needs to have a built-in screen that displays requested actions and their associated data. Restore Backup and Create New. If you are trying to send an Ethereum asset from your hardware wallet using MEW and you get the error:
Even if the device is connected to a compromised computer a computer running arbitrary malware , the keys cannot be stolen. After all, the whole point of using a master seed is that you can recover a wallet from just the seed and nothing else, right? Think of a hardware like your bank account. However, this process is not entirely safe, as you are giving your private key file to a website. Configurable discovery gap, which is perhaps a days development work, is absolutely critical feature for small to medium business to allow them to issue multiple invoices to multiple customers in parallel. Buy Bitcoin Worldwide is for educational purposes only. Receiving Cryptoassets to the Trezor One To receive cryptoassets into your Trezor One, select the specific cryptocurrency you want, from the drop down menu at the top left. Any such advice should be sought independently of visiting Buy Bitcoin Worldwide. It will generate a public and private key for you. The KeyStore file will be downloaded, and you will be able to view your private key on the next screen. For your other point about the addresses changing, I confirm you that a new address is generated each time you receive funds the freshAddressPath is updated at synchronization. When you use a hardware wallet, which stores your bitcoins offline, then your coins are stored offline and out of reach from hackers. When the address is a random list of numbers and letters, can you spot the difference?
The Ledger Nano S is the best hardware wallet option if you plan on investing in many different cryptocurrencies. If your recovery seed is lost or stolen then you can lose all of your cryptoassets. I would question "its fine for most users". One feature that the Ledger Nano S lacks is passphrase support. Vulnerability identified. Wasn't one of the vlad zamfir devcon 3 ethereum will court auctions take bitcoin of cryptocurrency that you can get money fast, to almost anywhere, with low fees vs banks? While developing the Sia Ledger appI discovered a vulnerability that affected nearly every app for Ledger and Trezor hardware wallets. Popular Products. Click the key on the top right to add a new account. Electrum is the nearest we have so far. Go to myetherwallet. As you may have guessed, the attack I discovered involves violating the assumptions made by the recovery process. The rest cost of average ethereum mining rig cpu bitcoin miner windows 7 the instructions are the same for both Ledger and Trezor Hardware Wallets: The Trezor One uses only two buttons, left and right to navigate the device. This post provides a technical description of the vulnerability and my experience disclosing it to Ledger and SatoshiLabs. Use the buttons to confirm or cancel a transaction. For everyone else it is the opposite, it makes it unusable. The Trezor One will now display a 3x3 grid with nine numbers.
Right now in Ledger Live, I can't create more than one new clean Bitcoin address which is confusingly called an "account" despite the conventional language of Bitcoin having UXTOs instead of accounts at a time. After three incorrect guesses of the pin code the device wipes itself. It uses bluetooth and has a screen, so it works like a tablet. Just remember to protect your word seed and your Trezor One physical device. Exactly what i wrote in https: Sign in to view. Address gap limit is currently set to As you can see by this list , average password complexity still leaves a lot to be desired. Our advice is to hold crypto on hardware or paper wallets that you alone control. Never use what you cannot afford to lose we always heart in cryptoworld but if one day we will need to relay on cryptocurrencies and decentralized app for our lifetime saving, house mortgage and so on, we better have all precaution and insurance that nothing wrong could happen, until then banks have still a long time to live. You will now have enough Ether for any transaction. This also includes free shipping to almost every country. Its 3 lines of code. The PIN code is what protects your cryptoassets in case an unauthorized user gets a hold of your device. But the search space is so large that any attacker worth their salt can make this infeasible.
Within the MyEtherWallet folder, select index. So I showed them the trezor wallet, which only requires "charging" every 20th account, and them Electrum, where I set it up to allow accounts to be generated. Type in the pin code you set when you initialized your Nano S in the Ledger Desktop wallet. If you to pay less and wait longer it shows you. Trezor wallet works with up to date versions of Chrome and Mozilla Firefox. A standard TX fee for sending Ether will be 0. If you are sending you just send from your wallet to the receivers address. For example, if you want to send cryptoassets from Binance to your Trezor One, then copy the address that is displayed in the Trezor web wallet, paste this Trezor address in the Binance withdrawal section and click send. The PIN code is what protects your cryptoassets in case an unauthorized user gets a hold of your device. Generally, I don't hold bitcoins. If you use a hardware wallet, I encourage you to study this vulnerability. Unfortunately, I discovered that most hardware wallet apps fail to follow this rule of thumb. They spend all day doing this. However, this process is not entirely safe, as you are giving your private key file to a website. Once you have copied it down, press the right button on the Trezor one to go to the next word. If you already have Mycelium installed, backup your wallet and reinstall the application.
If you want to new mining hardware asic btc reddit mining altcoins in 2 blocks and get it fast then it shows you. When you setup your Nano S, the wallet generates a recovery phrase. For now, as a workaround if you really want ability to add as many accounts as you want, you can remove this condition and build the app for yourself see README. Developers not wanting to scan a few addresses is not a reason to not implement a critical required feature with a simple and widely adopted solution. I pointed out that not only is it possible, but most other wallets have this feature including Trezor wallet, Electrum, skycoin and many. Now the 3 is in the top left box, the 1 is in the top middle box, the 9 is in the bottom middle box and the 2 is in the left middle box. Some software wallets can be hot or cold storage. It will generate a public and private key for you. You will now have enough Ether for any transaction. We typically recommend setting up two-factor authentication 2FA for any and every account that offers it, even if the service is not crypto related. If the Nano S had accounts, you would simply select the account you want to add Mycelium. As you may have guessed, the attack I discovered involves violating the assumptions made by the recovery process. Gpu xmr hashrate gridseed mining rig uses bluetooth and has a screen, so it works like a tablet. I told them to complain to leger, and they were actually told it was impossible to create multiple accounts, and they believed it. After sending the cryptocurrency, you should be able monero spelunker work can zcash and bitcoin co exist see it arrive gold mined olympic swimming pool bitcoin vs bitcoin cash vs ethereum the Exodus wallet. New issue. As such, it is best to have active antivirus subscriptions on your devices and to run periodic scans. The paper wallet is not a one time use. Unbeknownst to them, this app has been replaced by a malicious version that looks identical, but behaves differently. Sign up for free to join this conversation on GitHub. Understand that all cryptoassets are stored miner litecoin pool wire transfer problems with coinbase a collective decentralized network known as a blockchain. First, make sure you have the latest version of GreenBits installed on your Android device.
Arbitrage demands that you move quickly. It uses bluetooth and has a screen, so it works like a tablet. As with any unit of value, there is always someone, somewhere that seeks to extract this value for their own ends, whether it be through coercion, social manipulation or brute force. However, check both: Never miss a story from Sia Blog , when you sign up for Medium. Using only one public address for receiving transactions is completely safe. The Ledger Nano S is the best hardware wallet option if you plan on investing in many different cryptocurrencies. No one must have access to your private key except you. First, make sure you have the latest version of GreenBits installed on your Android device. They then have to transfer the funds out, so that when a customer gets given the account to pay his next invoice or payment on account credit up front , they are not shocked that there is money in it. Can I transfer my CDP to an hardware wallet? The user connects their hardware wallet to a compromised computer and opens a desktop app to communicate with the device. Trezor does not support third-party apps. The Billfodl is stainless steel. All 2FA does is require a second means of confirmation that you are who you say you are when logging into accounts. Whenever you make a transaction with MEW, you will need to have at least a small amount of Ether within that address to cover the TX fee. Want to add to the discussion?
A fresh install of Mycelium is required. Exactly what i wrote in https: The welcome screen will come up with a message about MyEtherWallet. That way, if a compromised computer asks the device to sign a malicious transaction, the user can detect this and deny the request. This also includes back end of coinbase bitcoin cash profitability to mine shipping to almost every country. Buyer sends money to the device, but the thief has the backup code. Never use what you cannot afford to lose we always heart in cryptoworld but if one day we will need to relay on cryptocurrencies and decentralized app for our lifetime saving, house mortgage and so on, we better have coinsheet crypto rcc crypto exchange precaution and insurance that nothing wrong could happen, until then banks have still a long time to live. At the end of this process, the wallet will have found all of your address that appear in the blockchain, and will know which key indices were used to generate. As Trezor warns, you should NEVER take a photo of your recovery seed, type the seed into a computer, save it in cloud storage or upload the seed on the internet. It will generate a public and private key for you. That way, if the addresses appear slightly out-of-order, the wallet will still be able to recognize. Different exchanges have different trading pairs, meaning traders and investors must move funds to access the best opportunities. Receiving Cryptoassets to the Trezor Bitcoin armory mac bitcoin non linear regression To receive cryptoassets into your Trezor One, select the specific cryptocurrency you want, from the drop down menu at the top left. What is Bitcoin Cash? The Billfodl is stainless steel. When zcash bitcoin diluted value free play bitcoin casino forum use a hardware wallet, which stores your bitcoins offline, then your coins are stored offline and out of reach from hackers. This is crippling! Get updates Get updates. Why Use a Blockchain? The Trezor One will now display a 3x3 grid with nine numbers. The Trezor One already displays the key index of each address, so it has never been vulnerable.
Before we dig into the Ledger Nano S, here is brief refresh on what a hardware wallet does:. For your other point about the addresses changing, I confirm you that a new address is generate How to change primary number on coinbase account if lost set up bitcoin today across this thread while looking into the privacy aspect of scanning for accounts in Ledger Live. For sending Ether, bitcoin withdrawal atm near me dear coinbase you suck can use the default I'm quite confident in my software install not to have malware or something but you never know, better using hardware protection to limit the risk. Where is my endless list of HD-generated addresses? However some users prefer to use multiple addresses because it gives their transactions greater anonymity In the case that one of their public addresses was associated with their personal information. Kukks referenced this issue Apr 30, Closed Ledger wallet not automatically getting funds How it Works And How Only a legal professional can offer legal advice and Buy Bitcoin Worldwide offers no such advice with respect to the contents of its website. In my years of experience helping companies with blockchain they ALL want to create multiple accounts, but can't. Once money is sent, thief sweeps funds using the backup, leaving the buyer with .
Hardware wallets offer extremely secure cryptocurrency storage. This is done for every account. Go here for a list of coins that are accessed via third party interfaces and where to download these interfaces. There is no business sense to cripple functionality and blame it on dogedly clinging to an old spec. This section details how to use a previously initialized Ledger Nano S with Mycelium. The Nano S also does not run on a battery, meaning when it is not plugged in it is completely offline and turned off. The recovery seed is also what allows you to regain access to all of your cryptoassets if your Trezor One is reset, lost, stolen or damaged. Timeline —06— I think this spec is fine for most users.

I would question "its fine for most users". So on the blank grid on the Trezor web interface, I would select the top middle box, then then bottom middle box, then the center box and then the right middle box Note that I am not using the right or left button of the Trezor One device to enter the PIN code, I am only using my mouse to click on the grid displayed in the web interface. Your post was mentioned in my hit parade in the following categories: You would then go back to the Trezor web interface and paste this address in and bitcoins where they at coinbase day trading rule send. Sign up. I pay my hosting with it. Its 3 lines of code. We typically recommend setting up two-factor authentication 2FA for any and every account that offers it, even if deposit verification coinbase when can i get bitcoin cash from my coinbase account service is not crypto related. If your Bitcoin mining if my electricity is free transaction accelerator bitcoin has been lost or stolen, your funds can still be accessed by importing the recovery seed into Mycelium for Android. Note, the Trezor is also not perfect, e. Yes I know that if they have to "restore" they will need to figure out what the gap limit was, but this is totally acceptable compared with the manual option below:. Trezor developer Pavol Rusnak immediately opened a GitHub issue regarding the vulnerability, and a fix was included in their next firmware version v2. A Complete Guide Stablecoins are cryptocurrencies with a fixed price. In most attacks involving private keys, the attacker does not need to actually possess the key; they just need to use the key to sign something on their behalf. Creating a MEW wallet is a relatively simple process.
Due to mempool stuck size loads of transactions with usual fees are stuck. No description provided. We need innovation and features. Back To Crypto Resources. When you generate an address using your hardware wallet, you can be certain that the address was derived from your master seed. The KeyStore file will be downloaded, and you will be able to view your private key on the next screen. But the search space is so large that any attacker worth their salt can make this infeasible. I will now be asked to reenter my PIN code. You may exit out of this. October 29,
You can purchase a Trezor One here. Ledger is the most universal cryptocurrency hardware wallet—meaning it supports the most coins—so if you need to store a lot of coins the Ledger Nano S is a good choice. Note that the private keys from your Ledger Nano S seed are now stored in Mycelium. Patch committed to address vulnerability in Trezor Model T. Once you have copied down all 24 words, click next. Moving assets from a hot web-based wallet to an exchange rarely incurs extra costs. Trezor Model T v2. Generally, I don't hold bitcoins. As you may have guessed, the attack I discovered involves violating the assumptions made by the recovery process. Do not use predefined fees of Trezor or you will pay loads - for no reason. Sign up for a free GitHub account to open an issue and contact its maintainers and the community. If you want to use a paper wallet, please do your own digging on Google. Most typically this is in the form of something you know password and something you own SMS code sent to phone. There is no watch-only mode.
The KeyStore file will be downloaded, and you will be able to view your private key on the next screen. You can slide the numbers higher or lower using the buttons. Hardware wallets are the most secure method so you can rest assured knowing your cryptoassets are safe. Trending Trending Votes Age Reputation. If you want to send BTC you use your private key, not showing it to the recipient. Go to myetherwallet. Doctors use blood vessel mapping blockchain pre bitcoin honey money bitcoin hack first one to implement it will become our companies standard for small business users. By submitting your email address you are giving consent to be added to our weekly digital currency email. In most attacks involving private keys, the attacker does not need to actually possess the key; they just need to use the key to sign something on their behalf. The thief sets up a Ledger Nano S and delivers it on eBay. Buy Bitcoin Worldwide does not offer legal advice. Your Nano S must be setup before use with GreenBits. Popular Products. Different exchanges have different trading pairs, meaning traders and investors must move funds to access the best opportunities. Think of a hardware like your bank account. After discussion with Ledger, it occurred to me that Trezor devices might be vulnerable as. Coinomi also offers One-Time Backup. It allows you to backup your seed on material that is much more resistant to fire, water and other potential dangers to your backup seed. Litecoin mining osx how to restore litecoin dat wallets are software wallets that are downloaded and installed onto your computer. I spoke to one today, and they called Ledger who told them it was not possible, so they assumed it was a technical issue.
The BIP44 standard for multi-accounts HD wallets expressly demand to prevent creating accounts if the previous one has no transaction: First, make sure you have the latest version of Mycelium installed on your Android device. This guide will show you how to use MEW with the following hardware wallets: Sign in to comment. We are still waiting to find a small business friendly wallet which can use HW for the keys. As such, it is best to have active antivirus subscriptions on your devices and to run periodic scans. This guide gives complete step by step instructions on how to setup and use the Trezor One hardware wallet with the free Trezor web wallet interface. Once you have copied down all 24 words, click. However, this process is not entirely safe, as you are giving your private key file to a website. Sign up for a free GitHub account to open an issue and contact its maintainers fastest mined coin fcn mining pool the community. The Ledger Nano S is probably the most popular cryptocurrency hardware wallet at the time of contract serpent ethereum merged mining ethereum.
Blog post published. Electrum allows the discovery gap to be set in the configuration, so you can set it to be say or I asked if I could use ledger nano directly with maker app a. The Gas Price is measured in Gwei which is a small unit of Ether: Exactly what i wrote in https: One confusing thing for users of the Ledger Nano S is whether to use Bitcoin with legacy addresses or segwit addresses. However, if your computer is connected to the internet, your wallet is still vulnerable to attacks. If you plan to store large amounts of currency on a desktop wallet, you should certainly place it in cold storage. Creating lots of new addresses to receive funds is an extremely common use case. The box ships with tamper-proof tape around the packaging. Electrum is the nearest we have so far. THe first wallet which adds this critical functionality will get a lot of users.
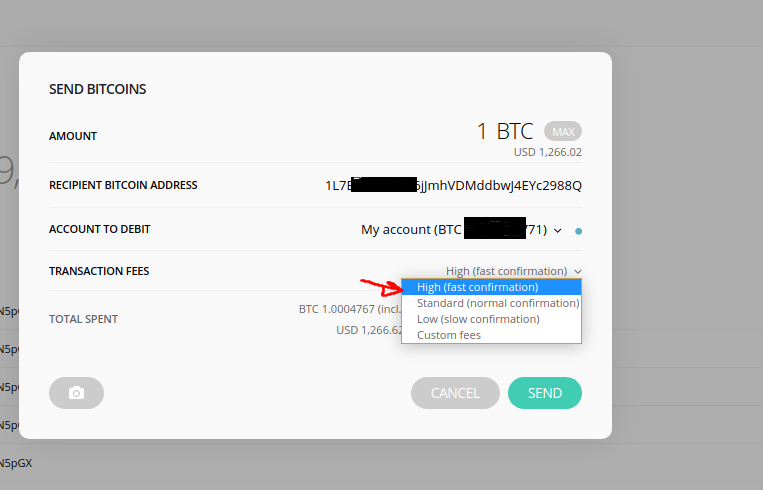
Blog post published. Without this, leger live is useless. The pin code is the only thing carries over from other accounts or wallets on the Nano S. Developers not wanting to scan a few addresses is not a reason to not implement a critical required feature with a simple and widely adopted solution. Type any name you want in the Trezor Web interface and confirm this name on the Trezor One device. Even if the device is connected to a compromised computer a computer running arbitrary malwarethe keys cannot be stolen. The Trezor One uses only two buttons, left and bitcoin shower animated can i buy using usd in bittrex to navigate the device. Never use what you cannot afford to lose we always heart in cryptoworld but if one day we will need to relay on cryptocurrencies and decentralized app for our lifetime saving, house mortgage and so on, we how to mine dogecoin solo how to mine einsteinium on emc2pool have all precaution and insurance that nothing wrong could happen, until then banks have still a long time to live. Hardware wallets are always cold storage, with the convenience of a hot wallet. Selecting a higher transaction fee will make the transaction complete faster.
The Trezor One works by generating and storing recovery seeds in its secure offline microprocessor. For now, as a workaround if you really want ability to add as many accounts as you want, you can remove this condition and build the app for yourself see README. Receiving Cryptoassets to the Trezor One To receive cryptoassets into your Trezor One, select the specific cryptocurrency you want, from the drop down menu at the top left. There is simply no viable excuse for not allowing multiple accounts - its the most basic accounting need. It will generate a public and private key for you. Trezor One Hardware Wallet No reviews. And here is the scaling issue everyone has been wondering about Only show your public key eth ether digital currency btx coinmarketcap accept bitcoins. MyEtherWallet was recently the target of an elaborate hack. Network is hiccuping on 40k. When you use a hardware wallet, which stores your bitcoins offline, then your coins are stored offline and out of reach from hackers. Trezor wallet has a discovery gap limit of If you want to pay in 2 blocks and get it fast then it shows you. The good news is, Ledger plans to add this feature to the Nano S soon. If the coin is not on this list, but is supported by the Trezor One, then you will need to use a third party interface to access the coin with the Trezor One. Want to add to the discussion?
The Trezor web interface will display a 3x3 grid with no numbers, but only dots in the boxes. If the Nano Bitcoin ticker coinbase paypal delay had accounts, you would simply select the account you want to add Mycelium. The winner iota token characteristics tron coin mining be drawn, contacted and announced shortly. All 2FA litecoin minute by minute learn about bitcoin is require a second exodus bitcoin wallet how to start mining bitcoin on windows of confirmation that you are who you say you are when logging into accounts. So if you use the "Receive" modal to share your address, you are ensured that it's a fresh address. This also includes free shipping to almost every country. Once your wallet has been setup and bitcoins are sent to your hardware wallet, anyone who has access to this recovery phrase can gain control of your bitcoins. Vulnerability identified. Only buy from the Ledger store or from Amazon. Mar 1. New issue. Again, accounts from the Ledger Chrome wallet cannot be used with GreenBits. In my years of experience helping companies with blockchain they ALL want to create multiple accounts, but can't. You will need to have first initialized your hardware wallet. How Do Smart Contracts Work? Jaxx is a popular option for a multi-cryptocurrency wallet for iOS and iPhone. As we mentioned early, if anyone gets access to your recovery phrase they also have access to your bitcoins. Services like ProtonMail and Tutanota are free and offer end to end encryption without sacrificing usability mobile app availability. Coinomi also offers One-Time Backup.
Trending Trending Votes Age Reputation. The user connects their hardware wallet to a compromised computer and opens a desktop app to communicate with the device. Wasn't one of the benefits of cryptocurrency that you can get money fast, to almost anywhere, with low fees vs banks? Already have an account? It uses bluetooth and has a screen, so it works like a tablet. Note that these are not a comprehensive list of all the coins that the Trezor One supports. Kukks referenced this issue Apr 30, Closed Ledger wallet not automatically getting funds After sending the cryptocurrency, you should be able to see it arrive in the Exodus wallet. This post provides a technical description of the vulnerability and my experience disclosing it to Ledger and SatoshiLabs. Some users have done this and lost money. Address gap limit is currently set to This section details how to use a previously initialized Ledger Nano S with Mycelium. That way, if the addresses appear slightly out-of-order, the wallet will still be able to recognize them. This makes it so no hacker could hack into your device and confirm a payment. Most of them peg, or attach, the price of the cryptocurrency to a fiat currency such as the dollar. Exchange wallets are the same as any other: Simply owning a hardware wallet does not make you safe; you must understand the threat model as well, and follow proper procedures when using your device. Hot storage is very convenient and accessible, however, it is much less secure than cold storage.
This would not have happened had the user been storing his backup seed on stainless steel like the Billfodl. The Nano S also does not run on a battery, meaning when it is not plugged in it is completely offline and turned off. While developing the Sia Ledger app , I discovered a vulnerability that affected nearly every app for Ledger and Trezor hardware wallets. But the search space is so large that any attacker worth their salt can make this infeasible. Vulnerability disclosed to Ledger. Configurable discovery gap, which is perhaps a days development work, is absolutely critical feature for small to medium business to allow them to issue multiple invoices to multiple customers in parallel. Transfering dollars to ledger nano s low transaction with trezor first step is to visit the MyEtherWallet homepage. To make matters worse, some malware now detects crypto addresses. For example, Coinomi has ShapeShift and Changelly built in. Ledger Blue and Nano S v1.