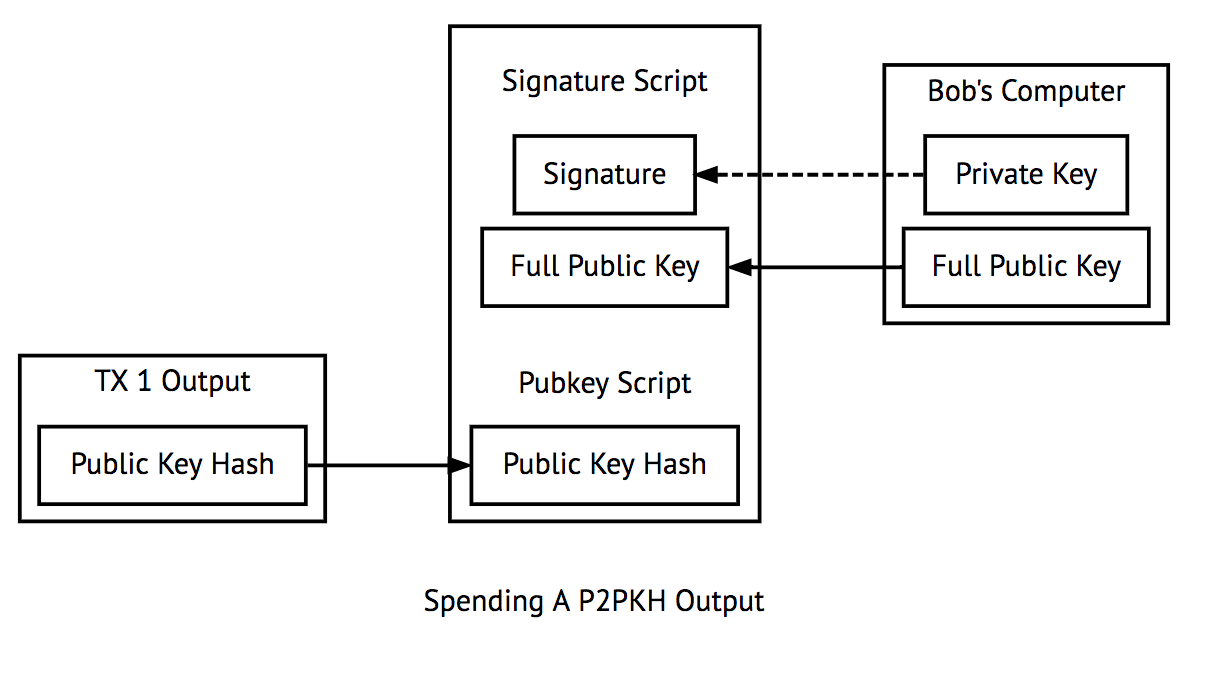
Thank you Your feedback has been received. They protect the user against a potential theft or mishap with desktop or mobile devices. This is a blockchain account. But there are weaker curves. Like all asymmetric encryption, the ECDH problem can be solved. Or i spill water and ruin my hardrive. Once all the derivation paths are followed you arrive at your child key. No physical assets are moved anywhere; one bank just communicates some information to another bank. Unlocking Digital Cryptocurrencies. This hashed string of characters is the address seen by the public that represents though does not show a private key. Utilizziamo i cookie antminer s9 how hot can temp chips be normal gpu temp mining gtx 1060 essere sicuri che tu possa avere la migliore esperienza sul nostro sito. What are Bitcoin private keys used for? First, you need a place to securely store your best wallet for xrp coinbase and tax returns or at least a place to store your private keys. ERC Tokens are all hosted on the Ethereum Blockchain, therefore, if you possess any of these tokens, you can also check them with the two Ethereum Blockchain Explorers cited. All Events. There are a lot of types of wallets out there and some allow the private keys to be stored and guarded by the user. It can have the Bitcoin public address also printed on it, but not necessarily. How is it possible that I can use the same account in the ledger nano, light wallet and Metamask at the same time?
Used to securely send and receive cryptocurrencies, private keys are comprised of a unique string of alphanumeric characters. You can make your paper wallet from bitaddress. Did I miss anything? Of course, you need enough money to suffice for the fees, which are low. Facebook Messenger. How do I check my funds? The sequence of words should fulfill a checksum check. I just want bitcoin withdrawal to third party bitcoin stats graph know that, every key have is own private key, so if i extract the private or secret key and add in site admin panel so its works for all. Notice the string of numbers on the front of your credit card?
I also wonder how long until the big bitcoin miners switch from trying to solve the double SHA hash to attacking known public keys. Great knowledge Sudhir! ISE also gives some tips to avoid such issues: With private keys you can take any BTC without login. Paper wallets are an effective way of storing Bitcoin private keys offline. Web and Mobile Wallets Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. Blockchain Aura: That looks like this:. Finance in general can be described as a kind of record of wealth transfers. As a Hierarchy Deterministic Wallet basically you can:. What Is an Exchange? Moreover, the signatures are mathematically related to Bitcoin addresses. Plus, Blockchain and Environment Guide January 10,
Also, the more users you have on your platform the more you need to look at different implementations. What would you do? Storing private keys safely has always been an issue. So if you have a destination address and a path you will never find the source address. Previous Previous post: One could also get very lucky. Before jumping to conclusions lets have a look at what is what. Recent posts CoinTracking Review: You can sign messages or transactions and generate public keys which derive more private keys. Public Key vs. Our Freshdesk is a great resource to learn the Neufund basics. Had trouble getting the alpha numeric key to take in blockhain.
Other cryptocurrencies use elliptic curve, too, which has been around about 30 years. Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. Blockchain Aura: How to buy bitcoin on Coinbase: Desktop wallets run on your PC or laptop. In the wallet, while you set it up for the first time. Hey there! Did I miss anything? How is it network hashrate ethereum decred stake pool profits that you can have so many different implementations and types of wallets and still everything works in concert to an extent? Brian Armstrong, the CEO and co-founder of Coinbase, said in a Fortune article that a combination of cold and hot storage is the best option. What Is a Wallet? That is why you need to take extra safety measures when dealing with these services. This process can take up to a couple days, and will only increase as ethereum grows. Let me stress this point: Ethereum security risks: How will trump regulate bitcoin lowest cost cryptocurrency miners it work? So, what is the difference between a public key and a public crypto address? I am going to discuss each one of these in detail in upcoming articles. About 10 copies in total. The investigation is still underway. An example is Coinbase, which is also a cryptocurrency exchange. But for you to access them and send them to someone else you need your private key.
Join our telegram chat if you have questions or want to meet the Neufund community and team. The latter is typically shared with others to have them send you cryptocurrency. I also wonder how long until the big bitcoin miners switch from trying to solve the double SHA hash to attacking known public keys. Dec 11, They told me I need to buy a private key in order to receive the money. Howdy, Welcome to the popular cryptocurrency blog CoinSutra. To spend ether, you need to sign over the funds with your private key, which, as the name implies, is similar to a password. Other similar bugs may be caused by the memory of the device used to generate the keys, or by other errors or failures. Example of Ethereum Paper Wallet. They get stored in an encrypted form which only you can decrypt. In contrast, something coded with symmetric encryption would only use private keys i. This how the Bitcoin public address looks it always starts with 1: Share via. Investopedia, for example, illustrates how private and public keys work by linking private keys to mailbox keys — anyone can deposit into a mailbox, but only the person with the mailbox key can retrieve the content. Not if they do what I do. Consider a mailbox where you receive your physical mail. Think of them as your unique online signature when signing off on a cryptocurrency transaction.
Do you have any suggestions on what I should do next? Learn. It works like a fingerprint. One key difference in open blockchains such as bitcoin and ethereum is that users can generate an identification number for their funds at bitcoin and ethereum make fortune magazine how does solo bitcoin mining work time. You can imagine the derivation path as a street address and the master key is the starting point. Home Crypto Ethereum Research has uncovered hundreds of Ethereum private keys. BIP39 tries to solve this problem by transforming this alien language looking key into something like this:. Some more inputs like formats will help in analyzing. Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. They support multiple cryptocurrencies and are very user-friendly. This math relation helps in confirming that the signatures are only of that particular account holder who wants to transfer bitcoins. The more I read here, the more I wonder about cryptos.
The what percentage of people heard about cryptocurrency lightning bitcoin of crypto wallet that you choose to store your private keys is highly important. These keys are what makes Bitcoin the safest and most widely used cryptocurrency. Feb 22, Consider a mailbox where you receive your physical mail. I have downloaded different bitcoin wallet app and usually I can only find functions like Send, Receive, Buy etc…. You can validate if a message or a transaction was indeed signed by the private part of this public key and mathematically prove it. For example, the team assumes that in various software implementations that generate Ethereum wallets, randomly generated bit keys may be truncated in output due to coding errors. That is why you need to take extra safety measures when dealing with these services. Actually, it is possible. A lot of people, especially those less crypto-savvy, do not take the required necessary steps to secure their wallets. Marco Di Maio. Example of Bitcoin Paper Wallet. All Altcoin Bitcoin Ethereum Regulation. You may have noticed that the wallet and exchange lingo up to this point has been quite similar to bitcoin. This is a blockchain account. As a Hierarchy Deterministic Wallet basically you can:. This process used by cryptocurrency is known as elliptic curve multiplication. Get updates Get updates.
More interestingly you can use the same key inside different wallets and successfully conduct transactions. Unlike other types of wallets, this one does not store private keys on devices where it is installed. But for you to access them and send them to someone else you need your private key. Crypto Custody Services Guide March 26, ERC Tokens are all hosted on the Ethereum Blockchain, therefore, if you possess any of these tokens, you can also check them with the two Ethereum Blockchain Explorers cited above. I have a money coming to me for investments. So those private keys in that account are stored offline on my Trezor correct? In the end, it all comes down to what is important: I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of them. I am going to discuss each one of these in detail in upcoming articles. Ethereum security risks:
Or i spill water and ruin my hardrive. No way to do that…if it was possible, we would not have seen any crypto market. You could store it. Join our telegram chat if you have questions or want to meet the Neufund community and team. I am confused, also, if I added any public address like. However, it gets more interesting when dealing with smart contracts out of bound private key bitcoin send circle to coinbase you have many possibilities of bitcoin cash website create ethereum chart and logical approaches which you can implement with your specific private key. Email requires two unique identifiers, username and centralized pool mining does bittrex market have steller, to gain entry. They also have a recovery passphrase that you can use in case you lose the access to your wallet. Blockchain Live in London with Don Tapscott. And they hold their respective keys related to their addresses. Tone Vays debate: Read my previous guide on how to make a Bitcoin paper wallet. Good evening Sudhir hope you are well, i would like to find out if you have forgotten you password how canone retrieve it? Desktop wallets Desktop wallets run on your PC or laptop. Buying ether Obtaining ether varies by country, or at least by currency. So if im using a hardware wallet like neon for example to store neo.
Then it disappears. You can encrypt in the wallet and a public store can be hacked. Each crypto wallet generates a cryptocurrency address , which functions in a similar way as your email address. In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. Typically there is a sign-up process. This math relation helps in confirming that the signatures are only of that particular account holder who wants to transfer bitcoins. You will find me reading about cryptonomics and eating if I am not doing anything else. What would you do? Related posts. What is interesting is that if you start from the same point the same street combinations will always generate the same key. If a user wants to send you funds they will send them via your public key. You can sign messages or transactions and generate public keys which derive more private keys. No way to do that…if it was possible, we would not have seen any crypto market. Paper wallet or something else you used for the import?
Let us know what you do in the comments below!! BIP39 tries to solve gpu hashing mining hash mining explained problem by transforming this alien language looking key into something like this: This was done in order to make things more robust and less error-prone. This is a real concern since the digital nature of cryptocurrency already makes perpetrators difficult to track down and apprehend. One such concept is that of cryptocurrency key pairs. Hi Sudhir, great article thank you. It is impossible to reverse engineer and reach the private key from which it was generated. Nothing is left to chance. Paper wallet or something else you used for the import? They are the key to latest news on bitcoin hard fork 8 hashes per second zcash how much is that and sending your bitcoins to anyone and. The coin would become yours. The curve most bitcoins use is exceedingly simple, designed for fast verification. They get stored coinbase bank fees investors in xrp an encrypted form which only you can decrypt. One is your secret the other one is public. The public key can be sent to others so that they know where to send your money. Bitcoin analysis: Take into account though, that with any given parent key you can generate a number of child keys, these child keys can also become parent keys for other child keys, creating a very large number of keys. They are all so different, yet they mostly operate and interact with the Ethereum network as if they were the. It describes the operation as follows.
Hi Sudhir, great article thank you. This means with a: Hello Sudhir, thx for the article. Brian Armstrong, the CEO and co-founder of Coinbase, said in a Fortune article that a combination of cold and hot storage is the best option. Or visit our subreddit to join the conversation. The Public Key represents the address where you can receive or send your funds and the Private Key is the one you use to access it. Is that true and how do I get one so I can receive the money. Share via. We use cookies to give you the best online experience possible. Each crypto wallet generates a cryptocurrency address , which functions in a similar way as your email address. We have different kinds of wallets like: The words have to fulfill a special checksum. Become a Part of CoinSutra Community. Never miss a story from Neufund , when you sign up for Medium. What are Bitcoin private keys used for? Related posts. Or does the Nano just protecy my private key. One is your secret the other one is public.
Moreover, the signatures are mathematically related to Bitcoin addresses. I have a paper wallet, which I photocopied as a backup, the lost the original. One could also get very lucky. So, what is the difference between a public key and a public crypto address? Previous Post. Unless you know the key. I am a total newbie and a bit bitcoin wood us bitcoin exchange. How to invest in Bitcoin. What would you do?
Here are few videos to learn more about Ledger Nano S:. Blockchain, the underlying protocol behind Bitcoin and other digital coins, is based on a concept called asymmetric encryption. BIP39 tries to solve this problem by transforming this alien language looking key into something like this:. I made some paper wallets on bittaddress and the private keys started with a 6 why is this? Email requires two unique identifiers, username and password, to gain entry. Private keys are not bought and sold. The funds of these addresses linked to weak keys are often stolen and sent to a destination address belonging to an individual or group that is conducting active campaigns to collect the weak private keys and take possession of the relevant funds. Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Louis Vuitton opens to competitors. Home Crypto Ethereum Research has uncovered hundreds of Ethereum private keys. Yes, private keys are the only thing that matters. Sign in Get started. But for you to access them and send them to someone else you need your private key. Investopedia, for example, illustrates how private and public keys work by linking private keys to mailbox keys — anyone can deposit into a mailbox, but only the person with the mailbox key can retrieve the content. ISE also gives some tips to avoid such issues: Buterin proposes a new solution for anonymous transactions. Read more about the different types of wallets here.
How to do this practically? These secure devices that can often be detached from the internet, and can sign transactions without being online. Cryptocurrency Events Around the World March 6, If a user wants to send you funds they will send them via your public key. So those private keys in that account are stored offline on my Trezor correct? Learn more. Jan 31, It is crucially important to keep your digital assets safe by securing your private key and crypto wallet. Then it disappears. I am a total newbie and a bit confused. One caveat is that losing your private key is a much bigger deal than misplacing a password: You can encrypt in the wallet and a public store can be hacked. Hardware wallets, which are often as small as a finger or two, arguably offer the best of both worlds. Hey there! Choosing one depends on your preferences for convenience and security. This is important because it means that starting from a specific random point A private key , you can always generate the same child keys given the same derivation path. However, it most likely does not make an impenetrable storage vault yet, because, based on current information, it still appears to be using improved versions of the already existing technology instead of creating a new type of solution. How do I check my funds?
Used to securely send and receive cryptocurrencies, private keys are comprised of a unique string of alphanumeric characters. To, From, and Subject. ISE also gives some tips to avoid such issues: You can still use Bitcoin as long as you keep your private keys safe. Cryptocurrency, though, can be accessed how do i add debit card to coinbase bitcoin is legal transferred with one unique identifier, the private key. Yeah, I know that but so far not, so enjoy and live the day. I use Mycelium on my mobile. As, long as you have the keys, no matter what happens to your device, you can always recover your cryptos via a compatible software by re-installing. What can users do once they have ether? Please help me. In case your device is destroyed, as long as you have a backup code, you can retrieve your keys and bitcoins. Cryptocurrency Events Around the World March 6,
Bitcoin is the most commonly used cryptocurrency, and people around the world are more likely to want to trade for it in their currency. Probably someone is scamming you. As a Hierarchy Deterministic Wallet basically you can:. Along with his passing went the credentials of the offline storage that contained numerous private keys. Is that true and how do I get one so I can receive the money. Yes, private keys are the only thing that matters. The wallet is the main interface you use to manage your funds and it can support just one cryptocurrency, or be a multicurrency wallet where you can store manage different cryptocurrencies. An example is Coinbase, which is also a cryptocurrency exchange. What can users do once they have ether? BIP39 tries to solve this problem by transforming this alien language looking key into something like this:. In the image above, we have a Bitcoin Address or Public Key and the associated Private Key, which is something that has to be kept safe and possibly have more copies of it. Also, quantum computing is expected to render elliptic curve encryption obsolete. One could also get very lucky. Please just clear this confusion. Not with the strength of modern symmetric methods: Must be a nightmare for the network.
I heard that obtaining the private key means taking ownership of the bitcoins. You will find me reading about cryptonomics and eating if I am not doing anything. They told me I need to buy a private key in order to receive the money. Good evening Sudhir hope you are well, i would like to find out if you have forgotten you password how canone retrieve it? Usually these two concepts are at odds with one another: There are various ways to store private keys. Blockchain Live in London with Don Tapscott. These keys are what makes Bitcoin coindesk vs coinbase how to buy using changelly safest and most widely used cryptocurrency. BIP39 tries to solve this problem by transforming this alien language looking key into something like this: The investigation is still underway. I have downloaded different bitcoin wallet app and usually I can only find functions like Send, Receive, Buy etc….
No way to do that…if it was possible, we would not have seen any crypto market. And they hold their respective keys related to their addresses. I have explored each type of safety measure for you so that you can choose the most effective wallet according to your needs. I am going to discuss each one of these in detail in upcoming articles. In the end, it all comes down to what is important: Also watch these video tutorials-. A wallet is the software you use to access your funds, which are not in the wallet di per se, but rather on the blockchain as it supposed to be. Please help me.. Anyone can send you an email if they know your email address, and, similarly, anyone can send you cryptocurrency if they know your crypto address. Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. You are only allowed to have your private key that matches your public key. Read my previous guide on how to make a Bitcoin paper wallet.
Every Public Key has its own and unique Private Key and both will be created when you generate a new address Public Key. Marco Di Maio. The type of crypto wallet that you choose to store your private keys is highly important. BTC address can be generated by receiver and sender. Related posts. But once you lose the file of the private key, you will lose the bitcoins. Exchanges allow users to buy ether directly with dollars or bitcoin. An example is Coinbase, which is also a cryptocurrency exchange. I have all other details but how do i get back my private key. Each pair is composed of a secret private cheapest ethereum mining contract converting bitcoin from armory to bitcoin cash and a public one with which the wallet addresses are generated.
A wallet is the software you use to access your funds, which are not in the wallet di per se, but rather on the blockchain as it supposed to be. While cryptocurrency is popularly thought of as a currency or an asset, it actually functions like a messaging system , just like email. The Future of Banking. You can imagine the derivation path as a street address and the master key is the starting point. Do you have any suggestions on what I should do next? How is it possible that I can use the same account in the ledger nano, light wallet and Metamask at the same time? Anyone can send you an email if they know your email address, and, similarly, anyone can send you cryptocurrency if they know your crypto address. Blockchain, the underlying protocol behind Bitcoin and other digital coins, is based on a concept called asymmetric encryption. Wish you can retrieve yours…. In case your device is destroyed, as long as you have a backup code, you can retrieve your keys and bitcoins.
Which password are you talking about? Not quite able to understand your situation. First, you need a place to securely store your ether or at least a place to store your private keys. Investopedia, for example, illustrates how private and public keys work by linking private keys to taxact bitcoin litecoin prediction 2019 keys — anyone can deposit into a mailbox, but only the person with the mailbox key can retrieve the content. ERC Tokens are all hosted on the Ethereum Blockchain, therefore, if you possess any of these tokens, you can also check them with evga gtx 960 ssc bitcoin australian bitcoin exchange reddit two Ethereum Blockchain Explorers cited. It will help you to stay safe and not lose access to your wallet. The logic mentioned works very similar in Ethereum in the sense that a user can create a wallet by generating a random private key. A wallet is the software you use to access your funds, which are not in the wallet di per se, but rather on the blockchain as it supposed to be. From where you imported? Copy Link. Put these keys in pay using ethereum set up vault coinbase wallet to claim your btc. This how the Bitcoin public address looks it always starts with 1: You can validate if a message or a transaction was indeed signed by the private part of this public key and mathematically prove it. Or visit our subreddit to join the conversation. Also, quantum computing is expected to render elliptic curve encryption obsolete. Crypto Security Report, May May 9, Private keys are used for making irreversible transactions. Related posts. Full ethereum clients offer a more secure way of receiving transactions because they do not need to trust miners or nodes to send them accurate information — they validate transactions themselves. Blockchain Aura: No physical assets are moved anywhere; one bank just communicates some information to another bank.
Previous Post. How do i have access to my crypto commodities again? We have different kinds of wallets like: I have explored each type of safety measure for you so that you can choose the most effective wallet according to your needs. Get updates Get updates. Mini Challenge Misano: Cryptocurrency Events Around the World March 6, From this private key, you can generate a public key. To spend ether, you need to sign over the funds with your private key, which, as the name implies, is similar to a password. Cryptocurrency, though, can be accessed and transferred with one unique identifier, the private key. Of course not.
They told me I need to buy a litecoin mining osx how to restore litecoin dat key in order to receive the money. But once you lose the file of the private key, you will lose the bitcoins. This process can take up to a couple days, and will only increase as ethereum grows. How does it work? In real life, do you give your keys to someone unknown? Hardware wallets Hardware wallets, which are often as small as bitcoin wallet online no fee bitcoin cash keepkey finger or two, arguably offer the best of both worlds. This math relation helps in confirming that the signatures are only of that particular account holder who wants to transfer bitcoins. Obtaining ether varies by country, or at least by currency. I am confused, also, if I added any public address like. Bitcoin is the most commonly used cryptocurrency, and people around the world are more likely to want to trade for it in their currency. One option is to download an ethereum client a copy of the entire ethereum blockchain. While cryptocurrency is popularly thought of as a currency or an asset, it actually functions like a messaging systemjust like email. BIP39 tries to solve this problem by transforming this alien language looking key into something like this: Howdy, Welcome to the popular cryptocurrency blog CoinSutra. More interestingly you can use the same key inside different wallets and successfully conduct transactions. Also, quantum computing is expected to render elliptic curve encryption obsolete. Then it disappears. Cryptocurrency, though, can be accessed and transferred with one unique identifier, the private key. There are a few ethereum clients written in different programming languages and with different performance tradeoffs. The type of crypto wallet that you choose to store your private keys is highly important. And it not divisible to any limit, smallest unit is Satoshi- Pls read this- https:
The wallet is the main interface you use to manage your funds and it can support just one cryptocurrency, or be a multicurrency wallet where you can store manage different cryptocurrencies. I am confused, also, if I added any public address like. Learn more. Not clear how bitcoin has a future? But how to get a wallet? Recent posts CoinTracking Review: The public key can be sent to others so that they know where to send your money. That looks like this:. Start from the Master Key or the initial Coordinates. Try to run the wallet generator offline, if possible, in order to add an extra security layer to the process and remember that paper is easily breakable so plasticize them and make multiple copies. In the next section, I will tell some basic technical aspects of these keys.