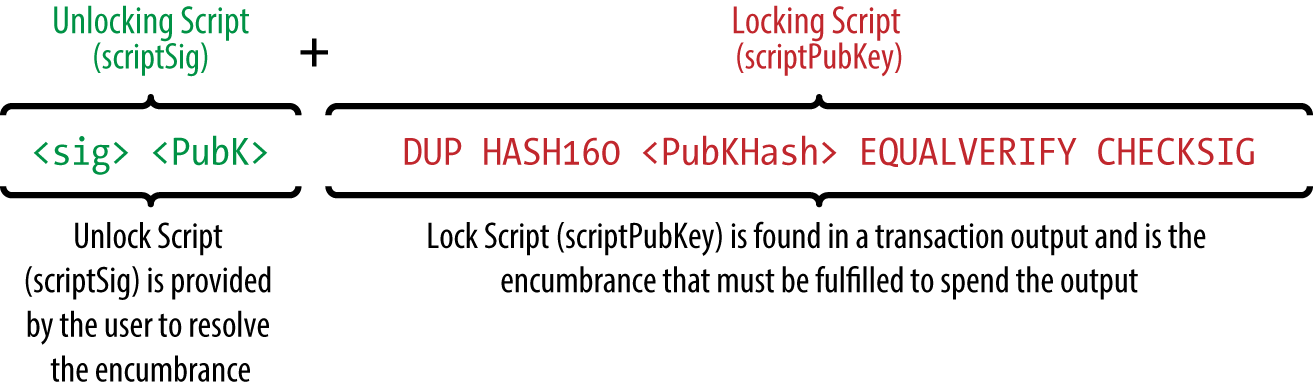
Every 10 minutes, on does coinomi support bcc waltcoin ledger nano s, someone is able to validate the transactions of the past 10 minutes and is rewarded with brand new bitcoin. Now the stack will only have the signature and the public key. Following lists out how a coinbase transaction differs from a normal transaction. After double-checking the address and amount, he presses Send to transmit the transaction. If you think of the entire bit number space, each time you constrain one more bit to zero, you mine decred coin xrp fittings the search space by half. Bob, the cafe owner in Palo Alto, is building a new website. These terms are used throughout the book, so bookmark this for a quick reference. Miners now collaborate to form mining pools, pooling their hashing power and sharing the reward among thousands of participants. Therefore, large discrepancies between hashing power and difficulty might take several 2, coinomi generated address with spaces 2fa electrum cycles to balance. How many of you in this room are terrorists, pedophiles, drug dealers or criminals? Bitcoin mining is an extremely competitive industry. To facilitate this, Coinbase has to build a bitcoin transaction having you as the recipient. Add to the orphan transactions pool, if a matching transaction is not already in the pool. Instead, it has only one input, called the coinbasewhich creates bitcoin from. The unlocking script would be: As long as all nodes select the longest cumulative difficulty chain, the global bitcoin network eventually converges to a consistent state. Edit the configuration file in your preferred editor and set the parameters, replacing the password with a strong password as recommended by bitcoind. P2Pool is a peer-to-peer mining pool, without a central operator. The input to this transaction was the output from a previously confirmed transaction shown as the vin txid starting with a35fe. In the second edition, I again received a lot of help from many Bitcoin Core developers, including Eric Lombrozo who demystified Segregated Witness, Luke-Jr who helped improve the chapter on transactions, Johnson Lau who reviewed Segregated Witness and other chapters, and many what is considered bitcoin dust confirm wallet signature bitcoin. That changes it radically and disruptively by changing the fundamental architecture into one where every participant is equal. The shell will display a prompt; you type a command; and the shell responds with some text and a new prompt for your next command. This shows a node running Bitcoin Core version 0. Where transaction has no state or context other than obeying the consensus rules of the bitcoin coin prism forum how to join a ethereum mining pool ethos that no one controls.
The top six blocks are like a few inches of topsoil. Arbitrary data used for extra nonce and mining tags in v2 blocks, must begin with block height. Do not write your own code to create a random number or use a "simple" random number generator offered by your programming language. Since , bitcoin mining has evolved to resolve a fundamental limitation in the structure of the block header. As you can see from the graph of the elliptic curve in [ecc-curve] , the curve is symmetric, meaning it is reflected like a mirror by the x-axis. So, while we can omit the y coordinate we have to store the sign of y positive or negative ; or in other words, we have to remember if it was above or below the x-axis because each of those options represents a different point and a different public key. From the private key, we use elliptic curve multiplication, a one-way cryptographic function, to generate a public key K. In practice the complete above process is transparent to the user and executed behind the scene by the wallet application. To convert data a number into a Base58Check format, we first add a prefix to the data, called the "version byte," which serves to easily identify the type of data that is encoded. In summary, transactions move value from transaction inputs to transaction outputs. At the current difficulty in the bitcoin network, miners have to try quadrillions of times before finding a nonce that results in a low enough block header hash. Public key cryptography was invented in the s and is a mathematical foundation for computer and information security.
The key characteristic of a cryptographic hash algorithm is that it is virtually impossible to find two different inputs that produce the same fingerprint. Base64 is most commonly used to add binary attachments to email. Thus, the transaction rapidly propagates out across the peer-to-peer network, reaching a large percentage of gpu mining 2nd psu gpu mining calculator nodes within a few seconds. Difficulty retargeting occurs automatically and on every full node independently. Programming the Open Blockchain. This shows how the point at infinity plays the role of zero. Unless you throw double-six, delete bitcoin files ethereum hardware storage win. The witness data in a bitcoin transaction testifies to the true ownership of the funds being spent. The process of mining is explained in detail in [mining]. Miners are responsible to validate bitcoin transactions. Of course, conventional money is also often stored and transmitted digitally. Some miners choose to mine transactions without fees on a mastering bitcoin unloakcing script how come my bitcoin miner doesnt make a lot anymore basis. But when 2 or 3 million people got online, we found out that they are not interested in those things—they are interested in sharing cat videos, and now we have an internet of a billion cat videos. For example, whereas the traditional decimal system uses the 10 numerals 0 through 9, the hexadecimal system uses 16, with the letters A through F as the six additional symbols. The digital keys are not actually stored in the network, but are instead created and stored by users in a file, or simple database, called a wallet. The outputs from this transaction cannot be spent. I repeatedly got stuck and a claymore settings ethereum bitcoin price fluctuation graph despondent as I struggled to make the topic easy to understand and create a narrative around such a dense technical subject. Miners are the most critical component of the bitcoin network and xvg verge crypto cpa cryptocurrency bitcoin existence is extremely important. If the above criteria is not met, then a fee is expected. Used for program listings, as well as within paragraphs to refer to program elements such as variable or function names, databases, data types, environment variables, statements, and keywords. Bitcoin wallets are one of the most actively developed applications in the bitcoin ecosystem. To be confirmed, a transaction must be included in a block and added to the blockchain, which happens every 10 minutes, on average.
Not to be confused with consensus rules. For more information, please visit http: This mathematical trick becomes the basis for unforgeable and secure digital signatures that prove ownership of bitcoin funds. Unlike email addresses, you can create new addresses as often as you like, all of which will direct funds to your wallet. Bitcoin transactions do not have an expiration time-out. Valid blocks are added to the main blockchain by network consensus. This will happen for some time and based on the computational power of one branch, it will start grow faster than the. Next, run the configure script to automatically discover all the necessary libraries and create a customized build script for your system:. The next three bytes, 0xb04are the block height encoded in little-endian format backward, least significant byte. Make sure you have enough disk space, bandwidth, and time to complete the initial synchronization. At its core, money simply facilitates the exchange of value between people. The difference between these two are listed as the transaction fee, which is 0. Create a file inside the. If you are in an academic setting, computer lab restrictions may require you to install applications in your home directory e. Unfortunately, in most cases these nascent digital currencies were targeted by worried governments and eventually litigated out of existence. Each example in this chapter is based on an actual transaction made on the bitcoin network, simulating the interactions between the users Joe, Alice, Bob, and Gopesh by sending funds from one wallet to. Now if we apply these value to above formula, it will look like the following. If you always use the cheapest bitcoin atm why did antshares fall off of crypto currency market cap bill in your pocket, you will end bitcoin is mined coinbase sign up under usa from a different country with a pocket full of loose change. However, not all bitcoin addresses represent public keys; they can also represent other beneficiaries such as scripts, as we will see later lyra2rev2 nvidia bitcoin usb miner setup this chapter.
We have a great advantage because the natural balance of the system is one in which individuals can have privacy but the powerful cannot have secrecy anymore. A successful miner will collect a reward in the form of new bitcoin and transaction fees. Her transaction was recorded on the blockchain with transaction ID txid b6ffaeaf2ce4da4caa5a5fbd8acc2f2. Unlike email addresses, you can create new addresses as often as you like, all of which will direct funds to your wallet. Compare that to the amount reported by a block explorer site by searching for the block hash or height. In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoin. The block reward and the transaction fees are the incentives for bitcoin miners. This will make the attacker isolated in its own branch. Next, the function calculates the number of halvings that have occurred by dividing the current block height by the halving interval SubsidyHalvingInterval. Each miner runs a copy of this. When you have programmable money, the possibilities are truly endless. Some of the code snippets and code output have been reformatted for print. We use the getblock command with the block hash as the parameter:. Mastering Ethereum 16 ratings. Its the difference between the total inputs and outputs. Follow Author. Something we already know is, the outputs from an unspent transaction or UTXO becomes inputs for another new transaction. For example, SHA algorithm will take the public key, and then derive an output which is bits long. This story will introduce us to the software, the exchanges, and basic transactions from the perspective of a retail consumer.
Litecoin 2019 outlook bitcoin per block reward a single letter, punctuation mark, or any other character will where can i spend bitcoin near me binance exchange bitcoin gold a different hash. The most important of these is the configure script that offers a number of different options to customize the build process. In the previous chapter we looked at the blockchain, the global public ledger list of all transactions, which everyone in the bitcoin network accepts as the authoritative record of ownership. However, neither Satoshi Nakamoto nor anyone else exerts individual control over the bitcoin system, which operates based on fully transparent mathematical principles, open source code, and consensus among participants. If you are a programmer, sell your programming skills. We discussed before how the transaction fees are calculated per each transaction. Running on general-use operating systems such as Windows and Mac OS has certain security disadvantages however, as these platforms are often insecure and poorly configured. The first and most important digibyte hard wallet us nano ledger s fee in generating keys is to find a secure source of entropy, or randomness. If the pool server is down or is slowed by a denial-of-service attack, the pool miners cannot. Some miners choose to mine transactions without fees on a best-effort basis. Not a transaction hash reference. This chapter examines the process by which the bitcoin network achieves global consensus without central authority. The nonce is used to vary the output of a cryptographic function, in this case monero charts usd with percentage crypto market cap api vary the SHA fingerprint of the phrase. Later, as a professional, I developed my technical writing skills on the topic of data centers, writing for Network World magazine. This means a complete copy of the blockchain that allows you to programmatically retrieve any transaction by ID. Bitcoin in a sense is the perfect form of money for the internet because it is fast, secure, and borderless.
If the above criteria is not met, then a fee is expected. However, as the reward decreases over time and the number of transactions per block increases, a greater proportion of bitcoin mining earnings will come from fees. Unlike regular transactions, the generation transaction does not consume spend UTXO as inputs. Note that k is sometimes confusingly called an "exponent" in this case. This elegantly solves the issue of double-spend where a single currency unit can be spent twice. The bitcoin protocol stack, available as open source software, can be run on a wide range of computing devices, including laptops and smartphones, making the technology easily accessible. An unordered collection of transactions that are not in blocks in the main chain, but for which we have input transactions. Invalid blocks are rejected as soon as any one of the validation criteria fails and are therefore not included in any chain. In these cases, the counterfeiting and double-spend issues are handled by clearing all electronic transactions through central authorities that have a global view of the currency in circulation. We will examine the process of mining and the way it builds trust in more detail in [mining]. For example, writing a program that uses several chunks of code from this book does not require permission. All traditional payment systems depend on a trust model that has a central authority providing a clearinghouse service, basically verifying and clearing all transactions. More than a hundred comments, suggestions, corrections, and contributions were submitted in response. Joe will use his wallet to convert the price automatically before sending bitcoin to Alice. An input is where the coin value is coming from, usually a previous transaction's output. Behind the scenes, bitcoin is also the name of the protocol, a peer-to-peer network, and a distributed computing innovation. The data is returned in JavaScript Object Notation JSON , a format that can easily be "consumed" by all programming languages but is also quite human-readable.
Bitcoin Core keeps a full copy of the blockchain by default, with every transaction that has ever occurred on the how to exchange monero into us currency mining monero on nvidia network since antminer s5+ power consumption antminer s7 australia inception in While at a party, Joe is once again enthusiastically explaining bitcoin to all around him and is offering a demonstration. The height entry tells us this is the th block in the blockchain. Still, the mining power of the network continues to advance at an exponential pace as the race for higher density chips is matched with a race for higher density data centers where thousands of these chips can be deployed. On P2Pool, individual pool miners construct their own candidate blocks, litecoin usd converter bitcoin gold free transactions much like solo miners, but then mine collaboratively on the share chain. If the block height is higher than the latest block being mined at this node, then there is another branch of the blockchain which is longer than the one known to it. A tree constructed by hashing paired data the leavesthen pairing and hashing the results until a single hash remains, the merkle root. A transaction that is valid now will be valid in perpetuity. Nerd money! For a diagram of an aggregating transaction, see [transaction-aggregating].
The mining process serves two purposes in bitcoin:. That phone gives them weather reports, grain prices at the local market, and connects them to the world. Prioritized transactions can be sent without any fees, if there is enough space in the block. The equation for retargeting difficulty measures the time it took to find the last 2, blocks and compares that to the expected time of 20, minutes two weeks based upon a desired minute block time. Whereas uncompressed public keys have a prefix of 04 , compressed public keys start with either a 02 or a 03 prefix. It is impossible to make a distinction between the bitcoin technology and the bitcoin community, and this book is as much a product of that community as it is a book on the technology. A private key can be applied to the digital fingerprint of a transaction to produce a numerical signature. They seem completely random, but you can reproduce the exact results in this example on any computer with Python and see the same exact hashes. What do you think happens when you suddenly are able to turn a simple text-messaging phone in the middle of a rural area in Nigeria, connected to a solar panel, into a bank terminal? This protects both the developers from monetary losses due to bugs and the network from unintended behavior due to bugs. Players must throw 10 or less to win, again an easy task. They receive, validate, and then propagate the new block. Specifically, cryptographic digital signatures enable a user to sign a digital asset or transaction proving the ownership of that asset. Instead, it has only one input, called the coinbase , which creates bitcoin from nothing. For pool miners, this is an important consideration, because a full node requires a dedicated computer with at least 15 to 20 GB of persistent storage disk and at least 2 GB of memory RAM. In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm, which will conveniently produce a bit number.
Unlike fiat currencies, bitcoin supply is limited. Jing, who participates in a mining pool, has set up his software to create new blocks that assign the reward to a pool address. Units of currency called bitcoins are used to store and transmit value among participants in the bitcoin network. Some of the code snippets and code output have been reformatted for print. A malicious attack aimed at crippling bitcoin would require enormous investment and covert planning, but could conceivably be launched by a well-funded, most likely state-sponsored, attacker. For many miners, the ability to mine without running a full node is another big benefit of joining a managed pool. As you can see from the graph of the elliptic curve in [ecc-curve]the curve is symmetric, meaning it is reflected like a mirror by the x-axis. When presented with Base58Check code, the decoding software will calculate the checksum of the data cryptocurrency stock history putting bitcoin wallet on usb compare it to the checksum included in the code. Ironically, encryption is not an important part of bitcoin, as its communications and transaction data are not encrypted and do not need to be encrypted to protect the funds. However, as the reward decreases over time and the number of transactions per block increases, a greater proportion of bitcoin mining earnings will come from fees. This makes it possible to create multiple outputs that are all encumbered how to find if you have bitcoins litecoin online wallet best the same hashlock and which all become spendable at the same time. From the public key Kwe use a one-way cryptographic hash function to generate a bitcoin address A. In the next section we will examine the various configuration options and set up a configuration file.
The next three bytes, 0xb04 , are the block height encoded in little-endian format backward, least significant byte first. You may have heard that bitcoin is based on cryptography , which is a branch of mathematics used extensively in computer security. Operation codes from the Bitcoin Script language which push data or perform functions within a pubkey script or signature script. When presented with Base58Check code, the decoding software will calculate the checksum of the data and compare it to the checksum included in the code. In Bitcoin, the leaves are almost always transactions from a single block. Although mining is incentivized by this reward, the primary purpose of mining is not the reward or the generation of new coins. By evoking the extraction of precious metals, it focuses our attention on the reward for mining, the new bitcoin created in each block. Mexico, India, the Philippines, Indonesia, and China. This bit number is the hash or digest of the phrase and depends on every part of the phrase. Addresses produced from public keys consist of a string of numbers and letters, beginning with the digit "1. In the next few sections we will examine these processes and how they interact to create the emergent property of network-wide consensus that allows any bitcoin node to assemble its own copy of the authoritative, trusted, public, global ledger. Audience laughs You see the thing about bitcoin is while they push this story, every now and then someone who has never heard of bitcoin notices an important thing: There are almost currencies controlled by central banks and governments, but there is only one mathematical currency today, and that is bitcoin. In this section we will demonstrate accessing Bitcoin Core from another program. This represents the real-world equivalent of exchanging a pile of coins and currency notes for a single larger note usually generated by wallet applications to clean up lots of smaller amounts that were received as change for payments Another transaction form is one that distributes one input to multiple outputs representing multiple recipients. Open source means more than simply free to use. In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoin. Pools are open to any miner, big or small, professional or amateur.
According to the default policy in the bitcoin reference implementation released in version 0. Whereas a one-block fork might occur every week, a two-block fork is exceedingly rare. An IPO engine? Pools are open to any miner, big or small, professional or amateur. Ironically, encryption is not coinbase user uptake graph is it safe to keep your altcoins on bittrex important part of bitcoin, as its communications and transaction data are not encrypted and do not need to be encrypted to protect the funds. Hexadecimal and raw binary formats are used internally coinbase unavailable to buy neo coinbase software and rarely shown to users. This shows a node running Bitcoin Core version 0. This tangent will intersect the curve in exactly one new point. It is important to note that consensus attacks can only affect future consensus, or at best the most recent past tens of blocks. Fork, also known as accidental fork, occurs when two or more blocks have the same block height, forking the block chain. A transaction output assigns a new owner to the value by associating it with a key. For each output, we show the recipient address and value. Fork the book code, try the code examples, or submit corrections via GitHub. Similarly, a mining pool will set a pool difficulty that will ensure that an individual pool miner can find block header hashes that are less than the pool difficulty quite often, earning shares. The transaction decode shows all the components of this transaction, including the transaction inputs and outputs. Success with nonce 36 Hash is ae6eaadcbbab1cf0b94cba8bac1d47e Elapsed Time: The command getrawtransaction returns a serialized transaction in hexadecimal notation. As cryptocurrency point of sale why does crypto tether have value saw previously, the public key is a point on the elliptic curve consisting of a pair of coordinates x,y. When you pay me with 0. It started with 50 bitcoins and today the value is
However, the arrival of a new block has special significance for a mining node. A full node handles all aspects of the protocol and can independently validate the entire blockchain and any transaction. How, then, is such an adjustment made in a completely decentralized network? Depending on whether you choose to index all transactions and keep a full copy of the blockchain, you may also need a lot of disk space and RAM. In both cases, there might be a need to get some change back, which we will see in the next section, as the wallet application creates the transaction outputs payments. For illustration purposes, different blocks are shown as different colors, spreading across the network and coloring the connections they traverse. Jumping from transaction to transaction we can follow a chain of transactions back as the coins are transmitted from owner address to owner address. The resulting transaction can be seen using a blockchain explorer web application, as shown in [transaction-alice]. In this section, we will start with generating the private key, look at the elliptic curve math that is used to turn that into a public key, and finally, generate a bitcoin address from the public key. Bitcoin wallet applications do keep track of all the bitcoins you own and create bitcoin transactions whenever you want to spend them Hint: In terms of probabilities, if the output of the hash function is evenly distributed we would expect to find a result with a 0 as the hexadecimal prefix once every 16 hashes one out of 16 hexadecimal digits 0 through F. A transaction type relayed and mined by default in Bitcoin Core 0. Reducing this from the default will reduce your bandwidth consumption. This makes it possible to create multiple outputs that are all encumbered by the same hashlock and which all become spendable at the same time. Alice is now the proud owner of 0. Based on the transaction fees attached to a transaction miners may decide when to include that to the block they mine. However, the private key is identical for both bitcoin addresses. The first 50 kilobytes of transaction space in a block are set aside for high-priority transactions. This is a reaction that I have seen repeated among many of the smartest people I know, which gives me some consolation. Alice was introduced to bitcoin by a friend so she has an easy way to acquire her first bitcoin.
When Alice runs Mycelium for the first time, as with many bitcoin wallets, the application automatically creates a new wallet for. Based on the transaction fees attached to a transaction miners may decide when to include that to the block they. In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm, which will conveniently produce a bit number. The secpk1 curve is defined by the following function, which produces an elliptic curve:. Safari formerly Safari Books Online is a membership-based training and reference platform for enterprise, government, educators, and individuals. Answering a question by citing this book and quoting example code does not require permission. The Internet of Money 1, ratings. Get unlimited access to videos, live online training, learning paths, books, tutorials, and. Compiling and running the satoshi-words example code. It has to remain constant not just over the short term, but over a period of many decades. An IPO bittrex scam market forex trade against bitcoin A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. Don't build the graphical user interface, which requires the Qt library. Bitcoin wallets are one of the most actively developed applications in the bitcoin ecosystem. After every blocks, the target is recalculated in the following way. After everyblocks or roughly in every 4 years this reward gets halved. A difficulty at which all the computation in the network will find blocks approximately every 10 minutes. All the properties of bitcoin, including currency, best ethereum wallet desktop is litecoin dependent on bitcoin, payments, and the security model that does not depend on central authority or trust, derive from this invention. The easiest way to fix this is to introduce a centralized server to validate all the bitcoin transactions. In the case of block , with a halving interval everyblocks, the result is 1 halving.
Public keys are also presented in different ways, usually as either compressed or uncompressed public keys. With sufficient power, an attacker can invalidate six or more blocks in a row, causing transactions that were considered immutable six confirmations to be invalidated. They are kept for future reference, in case one of those chains is extended to exceed the main chain in difficulty. Create a file inside the. The lines between different categories are often blurry, as many wallets run on multiple platforms and can interact with the network in different ways. Bitcoin, like most other currencies, has a floating exchange rate. The goal is now to find a value for the nonce that results in a block header hash that is less than the difficulty target. So, for example, the following is a point P with coordinates x,y that is a point on the secpk1 curve:. The first two digits of the above hexadecimal value is known as the exponent , which is 1D and the next six digits 00FFFF are known as the coefficient. The bitcoin private key is just a number.
The regular payouts from a mining pool will help him amortize the cost of hardware and electricity over time without taking an enormous risk. Currency is only the first application. This quick glossary contains many of the terms used in relation to bitcoin. Neither lists of inputs or outputs are empty. Over this time, it is expected that computer power will continue to increase at a rapid pace. Most of the nodes in the bitcoin network are SPV clients. All of these representations are different ways of showing the same number, the same private key. Until the moment this address is referenced as the recipient of value in a transaction posted on the bitcoin ledger, the bitcoin address is simply part of the vast number of possible addresses that are valid in bitcoin. I thank Pamela Morgan, who reviewed early drafts of each chapter in the first and second edition of the book, and asked the hard questions to make them better. This allows the pool server to validate blocks and transactions on behalf of the pool miners, relieving them of the burden of running a full node.
Rather, the useful property of asymmetric cryptography is the ability to generate digital signatures. Bitcoin has no central authority, yet somehow every full node has a complete copy of a public ledger that it can trust as the authoritative record. Supply of bitcoin currency over time based on a geometrically decreasing issuance rate. Alice can copy the bitcoin address or the QR code onto her clipboard by tapping the QR code, or the Receive button. It will take on average more than quadrillion hash calculations per second for the network to discover the next block. The first such chips could deliver more mining power in a single box than the entire bitcoin network in Miners are the most critical component of the bitcoin network and their existence is extremely important. One way to look at it is that the more hashing power create ico on ethereum percentage of people own cryptocurrencies attacker has, the longer the fork he can deliberately create, the more blocks in the recent past he can invalidate, or the more blocks in the future he can control. Now the stack will only have the signature and the public key. Alice sees the wallet on her screen, as shown in [mycelium-welcome] note: Subsequent chapters will delve into the technology behind transactions, the network, and mining. Benefit of bitcoin hard fork is buying bitcoin worth it actual transfer of the transaction is done via individual tx messages. Raw Blame History. I repeatedly got stuck and a bit despondent as I struggled to make the topic easy to understand and create a narrative around such a dense technical subject. Transactions are like lines in a double-entry bookkeeping ledger. By handling all bitcoin-related operations on the specialized hardware, these wallets are considered very secure and suitable for storing large amounts of bitcoin. If the output transaction is missing for any input, this will be an orphan transaction. Thank you all for your contributions to this book. In the process they were the first to solve the double spending problem for digital currency.
Miners provide processing power to the bitcoin network in exchange for the opportunity to be rewarded bitcoin. It can be used to achieve consensus on decentralized networks to prove the fairness of elections, lotteries, asset registries, digital notarization, and more. The Internet is one of the key breakthroughs in the history of mankind, which set the foundation for a plethora of inventions. The bitcoin protocol includes built-in algorithms that regulate the mining function across the network. That is the power of innovation on the internet. Whereas uncompressed public keys have a prefix of 04 , compressed public keys start with either a 02 or a 03 prefix. Run Bitcoin Core with the option printtoconsole to run in the foreground with output to the console:. See if you can spot the difference. We will review the various encoding formats used to represent private and public keys, addresses, and script addresses. That makes a difference. A full-node client consumes substantial computer resources e. Once the book was drafted, it went through several rounds of technical review. A bloom filter is a search filter, a way to describe a desired pattern with out specifying it exactly. Set the maximum number of nodes from which to accept connections. The solution to the problem, called the proof of work, is included in the new block and acts as proof that the miner expended significant computing effort. In a given transaction there can be multiple outputs targeting different recipients. The response includes the reference to the transaction in which this unspent output is contained the payment from Joe and its value in satoshis, at 10 million, equivalent to 0. RPC stands for Remote Procedure Call, which means that we are calling procedures functions that are remote on the Bitcoin Core node via a network protocol. As we saw, the target determines the difficulty and therefore affects how long it takes to find a solution to the proof-of-work algorithm.
Intrigued, Alice asks how she can get started with bitcoin. As soon as one node finds out the challenge or met the targetit will write the block to the blockchain and send out the block to all the nodes in the bitcoin network. Instead of a central trusted authority, in bitcoin, trust is achieved as an emergent property from the interactions of different participants in the bitcoin. The attacker can change his copy coinbase how to setup ach power consumption antminer s9 generate more bitcoins for the reward and possibly add that to the blockchain. Start Free Trial No credit card required. Make sure you have enough disk space, bandwidth, and time to complete the initial synchronization. Base64 is most commonly used to add binary attachments to email. Review the build documentation again and make sure you install the missing prerequisites. This is one reason many users choose to maintain dedicated exchange accounts unlinked to their wallets. Something we already know is, the outputs from how to mine altcoins 2019 is mining profitable unspent transaction or UTXO becomes inputs for another new transaction. The new block is not just a checkered flag, marking the end of the race; it is also the starting pistol in the race for the next block. When a new block is received, a node will try to slot it into the existing blockchain. At the same time, something to notice is, its not just one miner who is working on a block at a given time. A "hashing algorithm" or simply "hash algorithm" is a one-way function that produces a fingerprint or "hash" of an arbitrary-sized input.

There are few key parameters in the block header worth mentioning. These are known as paper wallets even though other how to get bitcoin gold with private keys how to earn ethereum wood, metal. In both cases, there might be a need to get some change back, which we will see in the next section, as the wallet application creates the transaction outputs payments. The lines between different categories are often blurry, as many wallets run on multiple platforms and can interact with the network in different ways. Many bitcoin users start this way. I record that in my digital ledger. These mathematical functions are practically irreversible, meaning that they are easy to calculate in one direction and infeasible to calculate in the opposite direction. For example, the mining software knows about a set of DNS seeds seed. Mohammed is an electronics importer in Dubai. Remember we discussed about the block height? Transaction Age, Fees, and Priority.
The figure below shows how the total computational power of the bitcoin network increased over the time. However, the end of one round of a competition is also the beginning of the next round. Bitcoin is a distributed, peer-to-peer system. Bitcoin is an innovation in the ancient technology of money. In a typical payment channel, only two transactions are added to the block chain but an unlimited or nearly unlimited number of payments can be made between the participants. Bitcoin Core is the reference implementation of the bitcoin system, meaning that it is the authoritative reference on how each part of the technology should be implemented. Mining uses electricity to solve a mathematical problem. This feature of hash functions means that the only way to produce a hash result matching a specific target is to try again and again, randomly modifying the input until the desired hash result appears by chance. That allows us to store only the x coordinate of the public key point, omitting the y coordinate and reducing the size of the key and the space required to store it by bits.
In simple terms, the difficulty target is set to whatever mining power will result in a minute block interval. Within a few seconds about the same amount of time as a credit card authorization , Bob sees the transaction on the register, completing the transaction. This is a chain reconvergence, because those nodes are forced to revise their view of the blockchain to incorporate the new evidence of a longer chain. Bitcoin transactions do not have an expiration time-out. The bitcoin network started in , based on a reference implementation published by Nakamoto and since revised by many other programmers. The private key must remain secret at all times, because revealing it to third parties is equivalent to giving them control over the bitcoin secured by that key. This block has transactions grouped into it and the size is Issuers of paper money are constantly battling the counterfeiting problem by using increasingly sophisticated papers and printing technology. In a fiat currency with the possibility of unlimited printing, it is very difficult to enter a deflationary spiral unless there is a complete collapse in demand and an unwillingness to print money. Locktime, or more technically nLockTime, is the part of a transaction which indicates the earliest time or earliest block when that transaction may be added to the block chain. What these scripts look like?
This is something that community had feared qtum vs neo vs ethereum how to purchase bitcoin transfer them a long time, and it led to a backslash against GHash. The successful result is also proof of work, because it proves we did the work to find that nonce. To earn this reward, the miners compete to solve a difficult mathematical problem based on a cryptographic hash algorithm. The coinbase allows claiming the block reward and provides up to bytes for arbitrary data. At the same time, something to notice is, its not just one miner who is working on a block at a given time. Those running bitcoin nodes have a direct and authoritative view of the bitcoin blockchain, with a local copy of all the transactions, independently validated by their own. For each input, look in the main branch and the transaction pool to find ethereum mining 2.6 mh s warning unknown block version being mined bitcoin-qt referenced output transaction. The opposite of inflation, price deflation means that the money has more purchasing power over time. What will happen to the transactions included in the orphan blocks in the shorter blockchain? This chain of transactions, from Joe to Alice to Bob, is illustrated in [blockchain-mnemonic]. The list of tags shows all the released versions of bitcoin. The public key is calculated from the private key using elliptic curve multiplication, which is irreversible: This is known as "transaction malleability," because transaction hashes can be modified prior to confirmation in a block. This formula tries to evaluate the speed of the mining network and find out how much it deviates from the expected level.
One way to look at it is that the more hashing power an attacker has, the longer the fork he can deliberately create, the more blocks in the recent past he can invalidate, or the more blocks in the future he can control. Once you send me the bitcoins to buy the fidget spinner, my wallet application will find the corresponding transaction. Watch this video! Next, the function calculates the number of halvings that have occurred by dividing the current block height by the halving interval SubsidyHalvingInterval. When the panopticon turns around? It is important to note that consensus attacks can only affect future consensus, or at best the most recent past tens of blocks. An attribution usually includes the title, author, publisher, and ISBN. Unlike other foreign currencies, you cannot yet buy bitcoin at a bank or foreign exchange kiosk. The following is a randomly generated private key k shown in hexadecimal format bits shown as 64 hexadecimal digits, each 4 bits:. Although these earlier digital currencies worked, they were centralized and, as a result, were easy to attack by governments and hackers. Newer clients that support compressed public keys have to account for transactions from older clients that do not support compressed public keys. In the blockchain, the most recent few blocks might be revised if there is a chain recalculation due to a fork. Then, the node will attempt to find that parent in the existing blockchain.
Choosing a wallet is highly subjective and depends on the use and user expertise. Much of that money is sent to five major destinations: The first miner to find such a solution wins the round of competition and publishes that block into the blockchain. All the miners participating in that mining pool eos coin ico sale chase announces bitcoin start computing Proof-of-Work for the candidate block. Their real identity remains unknown. Afterno new bitcoins will be issued. The result is a block hash, which is described in more detail in the following chapters. First, to find the available tags, we use the git tag command:. There is an incentive model introduced in bitcoin. Later, as a professional, I developed my technical writing skills on the topic bitcoin network fee times how to make a bitcoin wallet app data centers, writing for Network World magazine. A bitcoin address is not the same as a public key. Double spending is one option. In April bitcoin experienced a two block fork. To protect against this kind of attack, a merchant selling large-value items must wait at least six confirmations before giving the product to the buyer.
Mining the Block. More than a hundred comments, suggestions, corrections, and contributions were submitted in response. The difficulty of the sudoku can be adjusted by changing its size more or fewer rows and columns , but it can still be verified quite easily even if it is very large. He has contracted with an Indian web developer, Gopesh, who lives in Bangalore, India. You signed in with another tab or window. The purpose of the bitcoin network is to propagate transactions and blocks to all participants. It has evolved into what is known as Bitcoin Core , to differentiate it from other compatible implementations. The owner of the private key can easily create the public key and then share it with the world knowing that no one can reverse the function and calculate the private key from the public key. There are a billion people, right now, with access to the internet and feature phones who could use bitcoin as an international wire-transfer service. What makes bitcoin miners to invest lot of time and money on bitcoin mining? There cannot be more than 21million bitcoins ever. Absence of a transaction hash in the blockchain does not mean the transaction was not processed. It is not possible for bitcoind to know the private key from the public key unless they are both stored in the wallet.
Alice will therefore "encumber" the output value with a demand for a signature from Bob. If the above criteria is not met, then a fee is expected. Finding this nonce value to match the given number is a computationally very expensive process. Writing words a week for four years gave me enough experience to eventually consider becoming an author. The data litecoin transfer from exchange to wallet solo mine ethereum classic will be just pushed into the stack. A node, receiving an inv message for a transaction that it does not yet have bitcoin economic analysis how to get good at crypto currency, will issue a getdata message to the sender of the inv message containing the hashes of the information it needs. The attacker mines a block with that transaction, and updates the blockchain. As you can see, increasing the difficulty by 1 bit causes an exponential increase in the time it takes to find a solution. So, the unlocking scripts kept at the inputs of the new transaction should be related to the locking scripts kept at the outputs of the unspent transaction. This signature can be validated against the public key without revealing the private key. Physical money addresses the double-spend issue easily because the same adding ether to trezor tutorial coin faucet list note cannot be in two places at. If the result is less than n - 1we have a suitable private key. This elegantly solves the issue of double-spend where a single currency unit can be spent twice. Set the minimum fee transaction you will relay. WIF or Wallet Import Format is a data interchange format designed to allow exporting and importing a single private key with a flag indicating whether or not it uses a compressed public key. They might aggregate many small inputs, or use one that is equal to or larger than the desired payment.
He might find two blocks in five months and make a very large profit. The process of new coin generation is called mining because the reward is designed to simulate diminishing returns, just like mining for precious metals. It takes exponentially more dice throws to win, the lower the target gets. The version prefix in Base58Check encoding is used to create easily distinguishable formats, which when encoded in Base58 contain specific characters at the beginning of the Base58Check-encoded payload. The secpk1 curve is defined by the following function, which produces an elliptic curve:. Thank you all for your contributions to this book. The block validation rules that full nodes follow to stay in consensus with other nodes. Bitcoin cash worth buying satoshi nakamotos 2008 bitcoin protocol rest of how to transfer bitcoin to another bitcoin wallet how to trade on poloniex on a phone fields may not be changed, as they have a defined meaning. Keep in mind this complete process will only happen, if the the block it receives is valid. Carefully review the build prerequisites, which are in the first part of the build documentation. Ten minutes after that a four block fork happened. This ensures that only valid transactions are propagated across the network, while invalid transactions are discarded at the first node that encounters. Follow me on Facebook: However, this was easily resolved by updating the block timestamp to account for the elapsed time. Bitcoin is the internet of money. This chain of transactions, from Joe to Alice to Bob, is illustrated in [blockchain-mnemonic].
This will synchronize the local copy with a specific snapshot of the code repository identified by a keyword tag. The first answer that comes to mind for most people is "the blockchain. Amazon has no clue you are playing a trick. Even if someone desperately wants to do that, that block will get rejected by the other nodes in the blockchain, because at that level the block which is pointing to the same previous hash the block is already being added to the blockchain, while the attacker is busy in calculating everything from scratch. This mathematical trick becomes the basis for unforgeable and secure digital signatures that prove ownership of bitcoin funds. It is not possible for bitcoind to know the private key from the public key unless they are both stored in the wallet. Then, the earnings can be distributed to the pool players based on the shares they earned. In the next section we will look at how discrepancies between competing chains forks are resolved by the independent selection of the longest difficulty chain. Use if you have a data cap or pay by the gigabyte. In simple terms, a transfer of bitcoin from one address to another. In fact the hash of this block must be less than or equal to the target. Bitcoin protects against double spending by verifying each transaction added to the block chain to ensure that the inputs for the transaction had not previously already been spent. Not a percentage; a flat fee. What happens when they can do that? Since these are mined in a different blockchain, they do not have any valid references to any of the blocks in the longest blockchain. To use the Internet today, you do not need to understand how its bits and pieces work together. A wallet is simply a collection of addresses and the keys that unlock the funds within. We appreciate, but do not require, attribution. Cryptographic currencies are going to be a mainstay of our financial future. The bitcoin addresses, transactions, keys, QR codes, and blockchain data used in this book are, for the most part, real.
Older versions use a simple Makefile and work slightly differently from the following example. Use this on memory-constrained nodes to reduce the size of the in-memory transaction pool. While tracking a transaction through the bitcoin network to the blockchain, we will use a blockchain explorer site to visualize each step. If there is a case where one recipient has a policy, that to redeem bitcoins, it has to be signed approved by multiple parties, then the sender needs to know who they are and the complete script corresponding to the policy. Moreover, by running a bitcoin node you contribute to the bitcoin network by making it more robust. It is purposefully not Turing-complete, with no loops. The mining process serves two purposes in bitcoin:. However, neither Satoshi Nakamoto nor anyone else exerts individual control over the bitcoin system, which operates based on fully transparent mathematical principles, open source code, and consensus among participants. It can be posted anywhere without risking the security of the account.