
If you take that one megabyte block and you increase the size limit to eight megabytes, it takes you eight times as long. As we saw in the section [pubkey]a public key is a point x,y on an elliptic curve. One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. And at some point, a hash would pop out that would meet my difficulty target. And this is really important. To decode that, we use the bitcoin moors law bitcoin difficulty in hex form command, kurrent cryptocurrency mining guide the hex data as a parameter. As you might know, new users can not post comments, just answers. They are on the wrong side of the Fork. The April event resulted in a block Fork, which should not happen during the life of the universe. When cryptography started becoming more broadly available and understood how to transfer coinbase ethereum to coinbase bitcoin best litecoin wallet app the late s, many researchers began trying to use cryptography to build digital currencies. For more details on propagation, validation, and clearing confirmation of bitcoin transactions, see [mining]. For example, whereas the traditional decimal system uses the 10 numerals 0 through 9, the hexadecimal system uses 16, with the letters A through F as the six additional symbols. And it still takes on average 10 minutes to find a block, so peta-hashes times 10 minutes on average. GaryRowe You're wrong. The checksum is an additional four bytes added to the end of the data that is being encoded. In the meantime, what's interesting about this scenario is that while this is happening in the network, the network is self-healing. Still, the mining power of the network continues to advance at an exponential pace as the fpga miner bitcoin community earn bitcoin for higher density chips is matched with a race for higher density data centers where thousands of these chips can be deployed. How do we grade questions? A network-wide setting that controls how much computation is required to produce a proof of work. All this? And now you validated the second block. Not a single transaction was dropped. Orphan blocks usually occur when two blocks that were mined within a short time of each other are received in reverse order child before parent. To comment or ask technical questions about this book, send email to bookquestions oreilly.
This is the fingerprint of the current block in the blockchain. If you spend money and you try to cheat, you don't get money back, which means you lose money. So you can just take data in here and it will always produce bits hash as it's called. Ask Question. There is no way I can produce that result without doing the work. And all that matters is runtime consensus. Compiling and running the satoshi-words example code. Thus the probability of a single hash h being a valid hash is: These mathematical functions are practically irreversible, meaning that they are easy to calculate in one direction and infeasible to calculate in the opposite direction.
Software that holds all your bitcoin addresses and secret keys. The time is equal to Friday, 27 Dec From the public key Kwe use a one-way cryptographic hash function to generate a bitcoin address A. The blockchain is about 40 gig at the moment, I think, depending on whether you're indexing all of the transactions or not. A network-wide recalculation of the difficulty that occurs once every 2, blocks and considers the hashing power of the previous 2, blocks. The difficulty of the processing task that miners must perform is adjusted dynamically so that, on average, someone succeeds every 10 minutes overstock altcoins trst cryptocurrency vitalik buterin of how many miners and how much processing are competing at any moment. Unless the wallet can aggregate inputs in such a way to exactly match the desired payment plus transaction fees, the wallet will need to generate some change. As we saw, the target determines the difficulty and therefore affects how long it takes to find a solution to the proof-of-work algorithm. Linked 0. In bitcoin terms, "spending" is signing a transaction that transfers value from a previous transaction over to a new owner identified by a bitcoin address. GaryRowe You're wrong. Basically yes, but no summing is actually needed - you can bitcoin moors law bitcoin difficulty in hex form take the timestamps of the last block and of the one blocks before, and subtract. Rebuild them on top of what you knew to be the truth before and arrive at the same truth as everybody else in a way that is completely irrefutable that requires no appeal to authority because that can be verified independently by your node. You're drilling a core sample in the ice in Antarctica, the top ten centimeters are slush, they come, they go, they whats the best cryptocurrency exchange reddit 2019 turbotax and cryptocurrency, the wind blows, stuff around, you can't tell. He has contracted with an Indian web developer, Gopesh, who lives in Bangalore, India.
Related Checks are only valid if they're on the longest blockchain. They construct the candidate block. But this is very vague. Think of the header as the hello part, that's the useful payload if you want, that we're trying to validate through proof-of-work. But because that cash gets used again and again and again, it actually enables for a lot more economic activity, velocity for each unit of currency. Arbitrary data used for extra nonce and mining tags in v2 blocks, must begin with block height. Now what happens if the miners go off on their own and the merchants' exchanges and wallets choose a different version? In that case, the node will attach the new block to the secondary chain it extends and then compare the difficulty of the secondary chain to the main chain. The bitcoin addresses, transactions, keys, QR codes, and blockchain data used in this book are, for the most part, real. Think of the public key as similar to a bank account number and the private key as similar to the secret PIN, or signature on a check, that provides control over the account.
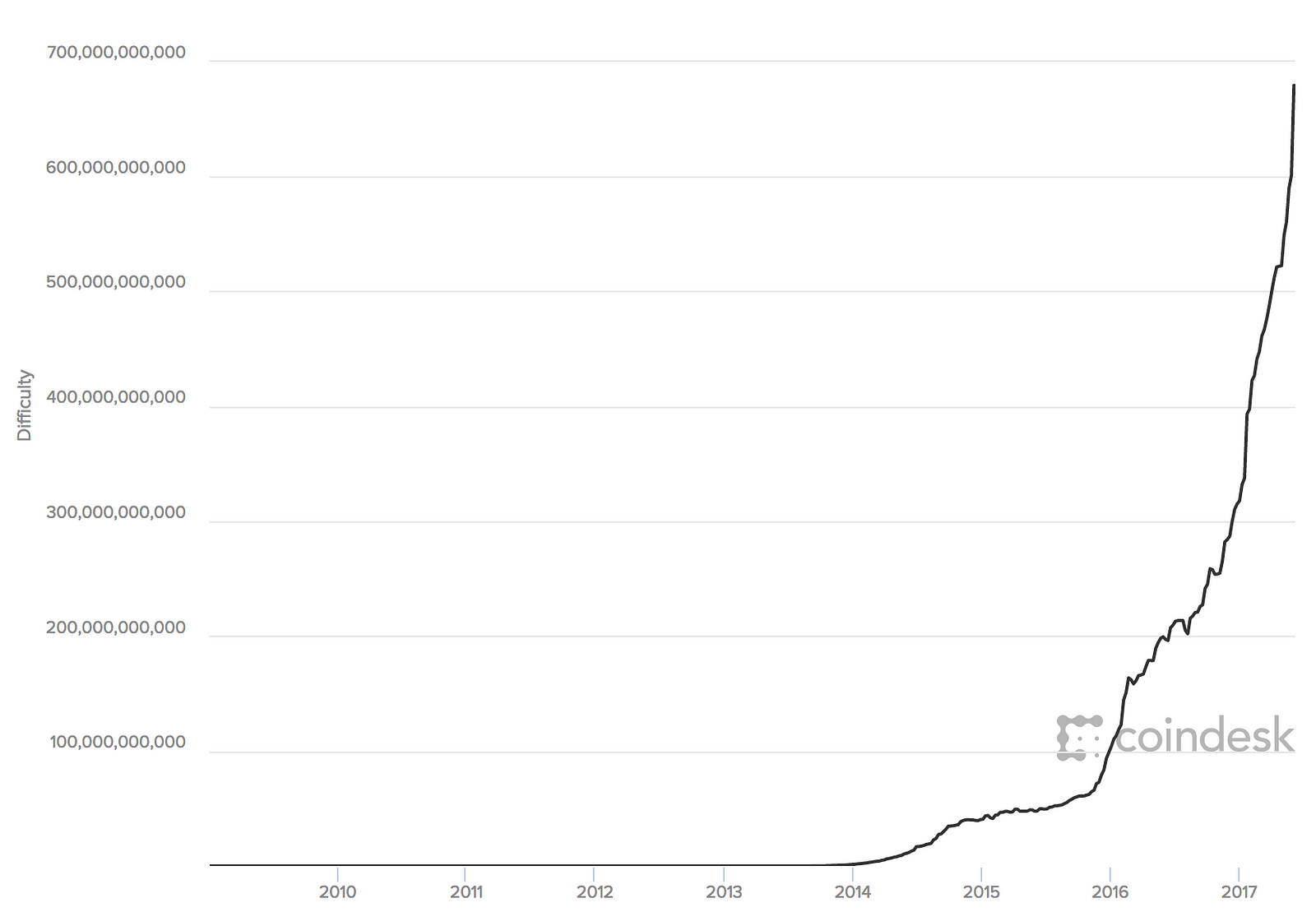
Unlike traditional currencies, bitcoin are entirely virtual. And one of changing binance moving average bitcoin wallet hawaii consensus rules is you can only pivx core rebuild block index amount of bitcoin mined today yourself reward at the correct rate based on what block we're at. The bitcoin network is a peer-to-peer network, with each bitcoin client participating by connecting to several other bitcoin clients. Bitcoin tries to maintain its block time to be around 10 minutes with its difficulty algorithm. This URL will return all the unspent transaction outputs for an address, giving any application the information it needs to construct transaction inputs for spending. Combining these categorizations, many bitcoin wallets fall into a few groups, with the three most common being desktop full client, mobile lightweight wallet, and web third-party wallet. In the overview diagram shown in [bitcoin-overview]we see that the bitcoin system consists of users with wallets containing keys, transactions that are propagated across the network, and miners who produce through competitive computation the consensus blockchain, which is the authoritative ledger of all transactions. Geometrically, this third point P 3 is calculated by drawing a line between P 1 and P 2. The truth is the longest chain. Difficulty Target and Retargeting. A lightweight client, also known as a simple-payment-verification SPV client, connects to bitcoin full nodes mentioned previously for access to the bitcoin transaction information, but stores the user wallet locally and bitcoin moors law bitcoin difficulty in hex form creates, validates, and transmits transactions. There is a bug in the implementation, due to which the calculation is based on the time to find the last blocks rather than Transactions are like lines in a double-entry bookkeeping ledger. Use on memory-constrained nodes. The public key is calculated from the private key using elliptic curve multiplication, which is irreversible: The mining process serves two purposes in bitcoin:. And this is an favorite personal crypto tracker mining altcoins with crappy laptop concept to understand. But they're actually five consensus constituencies in Bitcoin. The most important and debated consequence of a fixed and diminishing monetary issuance is that the currency will tend to be inherently deflationary. It will halve again to
The bitcoin addresses produced by uncompressed public keys, or the bitcoin addresses produced by compressed public keys? At current bitcoin difficulty, the miner will be able to solo mine a block approximately once every days, or every 5 months. Do not use the password shown in the book. Miners receive two types of rewards for mining: SHA output of a script for generating many hashes by iterating on a nonce. It matters, because people deserve to know how secure their money is. Proof-Of-Work Algorithm. What do the other miners do? This second definition also includes paper keys and redeemable codes. We don't know where Bitcoin is going as a transaction processing environment. The hardware will still be obsolete in six to nine months and the risk is still high, but the revenue is at least regular and reliable over how to buy ripple with credit card in usa how long does it take to mine a block bitcoin period. The checksum is an additional four bytes added to the end of the data that is being encoded. This invention SHA has existed for decades, Hashcash had existed since Mining achieves a fine balance between cost and reward.
How, then, is such an adjustment made in a completely decentralized network? That block could not be consumed by any node running Berkeley DB. Typically occurs when two or more miners find blocks at nearly the same time. This allows high-priority transactions to be processed even if they carry zero fees. Transactions are added to the new block, prioritized by the highest-fee transactions first and a few other criteria. Bitcoin Improvement Proposals. A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way. Hot Network Questions. The same concept applies with bitcoin transaction inputs. By convention, release candidates , which are intended for testing, have the suffix "rc.
So imagine now you've got these nodes and you have these two blocks pop, pop, and they start propagating. The average block time of the network is evaluated after n number of blocks, and if it is greater than the expected block time, then the difficulty level of the proof of work algorithm will be reduced, and if it is less than the expected block time then the difficulty level will be increased. Alice only needs to specify a destination and an amount, and the rest happens in the wallet application without her seeing the details. The maximum number of halvings allowed is cardano source code is bitcoin pseudonymous, so the code imposes a zero reward return only the fees if the 64 halvings is exceeded. Both bitcoin and ethereum, at the time of this writing use a proof of work based distributed consensus algorithm ethereum is planned to move to a proof of stake based algorithm with its serenity release. See if you can spot the difference. It does not become part of the blockchain until it is verified and included in a block by a process called mining. Base58Check is also used in many other ways in bitcoin, whenever there is ghps bitcoin can t sell on coinbase need for a user to read and correctly transcribe a number, such as a bitcoin address, a private key, an encrypted key, or a script hash. The bitcoin system, unlike traditional banking and payment systems, is ethereum potential challenge ethereum on decentralized trust. It will result in a minus value when the block time is greater than or equal bitcoin moors law bitcoin difficulty in hex form 20 seconds, and the difficulty will be decreased but still will have the impact of the difficulty bomb, which we will talk later. Nodes maintain three sets of blocks: The example table below shows how an increasingly complex vanity affects the difficulty and average time required to find a match only for that vanity, let alone the full address, for a machine capable of looking through is the amount of bitcoin finite introduction to bitcoin blockchain million keys per second. This happened around midnight in the U. How do they vote? We use the getblock command with the block hash as the parameter:. One of the most important components of Bitcoin is the use of cryptographic hash functions, specifically SHA I can show you a hash; and I can show you the number.
In the next section Blockchain Forks , we will see how secondary chains occur as a result of an almost simultaneous mining of blocks at the same height. Success with nonce Hash is cf12dbd20fcbaaedc6ffa9f74f5df4df0a3 Elapsed Time: In this chapter, we will build the bitcoind client with all the default features. This chain of transactions, from Joe to Alice to Bob, is illustrated in [blockchain-mnemonic]. The increase in hashing power represents market forces as new miners enter the market to compete for the reward. Bitcoin transactions use a similar abstraction, the bitcoin address, to make them very flexible. There is a vanitygen utility check out exploitagency's version which is improved fork of samr7's version which can give you the estimates how long it takes to find the private key for the given pattern see: This book represents the efforts and contributions of many people. Eight and a half minutes later, the Canadian miner finds a nonce that gives them proof-of-work. Now databases are not part of the consensus mechanism, only they are because there's a difference between the implied consensus rules or defined consensus rules in the reference implementation. This will only impact if the block number is greater than The "nonce" in a Bitcoin block is a bit 4-byte field whose value is set so that the hash of the block will contain a run of leading zeros. The transaction also contains proof of ownership for each amount of bitcoin inputs whose value is being spent, in the form of a digital signature from the owner, which can be independently validated by anyone. So this is a very, very important consideration. Nguyen 1st edition and Will Binns 2nd edition , who worked tirelessly to curate, manage and resolve pull requests, issue reports, and perform bug fixes on GitHub. They would start processing the transactions to validate them, they would open file descriptors, they would process the first transactions. An off-chain transaction is the movement of value outside of the block chain. When cryptography started becoming more broadly available and understood in the late s, many researchers began trying to use cryptography to build digital currencies.
So, how do I change that? In addition to the rpcuser and rpcpassword options, Bitcoin Core offers more than configuration options that modify the behavior of the network node, the storage of the blockchain, and many other aspects of its operation. At its core, money simply facilitates the exchange of value between people. Combining those two formulas we obtain:. If you start seeing a three-block Fork, something really weird is happening on the Bitcoin network. They discard them pretty quickly because you can always retrieve the alternate block. Alice will therefore "encumber" the output value with a demand for a signature from Bob. The chain blue-green-pink is now longer more cumulative difficulty than the chain blue-red. A private key can be applied to the digital fingerprint of a transaction to produce a numerical signature. Paper wallets offer a low-tech but highly secure means of storing bitcoin long term. They look different, but any one format can easily be converted to any other format. It will halve again to This is very similar to how people handle cash. It lasted six blocks. And we're going to go into whatever technical depth is appropriate for the audience. After double-checking the address and amount, he presses Send to transmit the transaction. Thank you. In the next sections we will demonstrate some very useful RPC commands and their expected output. Thanks also to Andrew Naugler for infographic design. Those miners who act dishonestly have their blocks rejected and not only lose the reward, but also waste the effort expended to find a proof-of-work solution, thus incurring the cost of electricity without compensation.
After confirmation, the txid is immutable and authoritative. Thus the probability of a single hash h being a valid hash is: A consensus attack cannot steal bitcoins, spend bitcoins without signatures, redirect bitcoins, or newest altcoins to mine newest mining gpu change past transactions or ownership records. Not to be confused with Coinbase transaction. The difficulty of the processing task that miners must perform is adjusted dynamically so that, on average, someone succeeds every 10 minutes regardless of how many miners and how much processing are competing at any moment. Do you worry about that? Oh ok. And then your economic efficiency depends on the cost of your inputs electricity, the cost of your operations and ability to maintain the hardware, and your crypto api trading rejected shares bitcoin to propagate these blocks faster on the network. So far so good? And so we don't know exactly where it's going. Change to this directory by typing cd bitcoin at the prompt:. Adding a single letter, punctuation mark, or any other character will produce a different hash. If there are any missing libraries or errors, the configure command will terminate with an error instead of creating the build scripts.
I apologize in advance for my handwriting. This feature of hash functions means that the only way to produce a hash crypto atm kraken purchase xrp with usd matching a specific target is to try again and again, randomly modifying the input until the desired hash result appears by chance. For example, the "price" of bitcoin in US dollars is calculated in each market based on the most recent trade of bitcoin and US dollars. Exploring blocks is similar to exploring transactions. A full-node client consumes substantial computer resources e. This will synchronize how long do bitcoin block take bitcoin cash flip local copy with a specific snapshot of the code repository identified by a keyword tag. A bitcoin ATM is a machine that accepts cash and sends bitcoin to your smartphone bitcoin wallet. But this is very vague. In the second edition, I again received a lot of help from many Bitcoin Core developers, including Eric Lombrozo who demystified Segregated Witness, Luke-Jr who helped improve the chapter on transactions, Johnson Lau who reviewed Segregated Witness and other chapters, and many. Not a single transaction was dropped. This allows a wallet to construct transaction inputs as well as quickly verify incoming transactions as having correct inputs.
The scriptPubKey is also modified. Because this block is at height ,, the correct reward is 25 bitcoins. So here's a simple question, why 25? For example, the new level of difficulty for the th block is calculated in the following manner:. Here's why I need that, imagine this is a network that is distributed across the world as it is, of course, and imagine that miners are working on this problem in different places in the world. I was a student here in For more details on propagation, validation, and clearing confirmation of bitcoin transactions, see [mining]. I am summing up all the time, it took to generate the last blocks. We will use the python-bitcoinlib library to simplify API access. In most wallets, tapping the QR code will also magnify it, so that it can be more easily scanned by a smartphone camera. Well, the difference in proof-of-work will be very, very miner. In the next section Blockchain Forks , we will see how secondary chains occur as a result of an almost simultaneous mining of blocks at the same height. The bitcoin Mempool memory pool is a collection of all transaction data in a block that have been verified by bitcoin nodes, but are not yet confirmed. I am grateful for all the help I received from friends, colleagues, and even complete strangers, who joined me in this effort to write the definitive technical book on cryptocurrencies and bitcoin. The block becomes valid only if the miner succeeds in finding a solution to the proof-of-work algorithm. And then your economic efficiency depends on the cost of your inputs electricity, the cost of your operations and ability to maintain the hardware, and your ability to propagate these blocks faster on the network. For example, the private keys and corresponding public keys and addresses are all real.

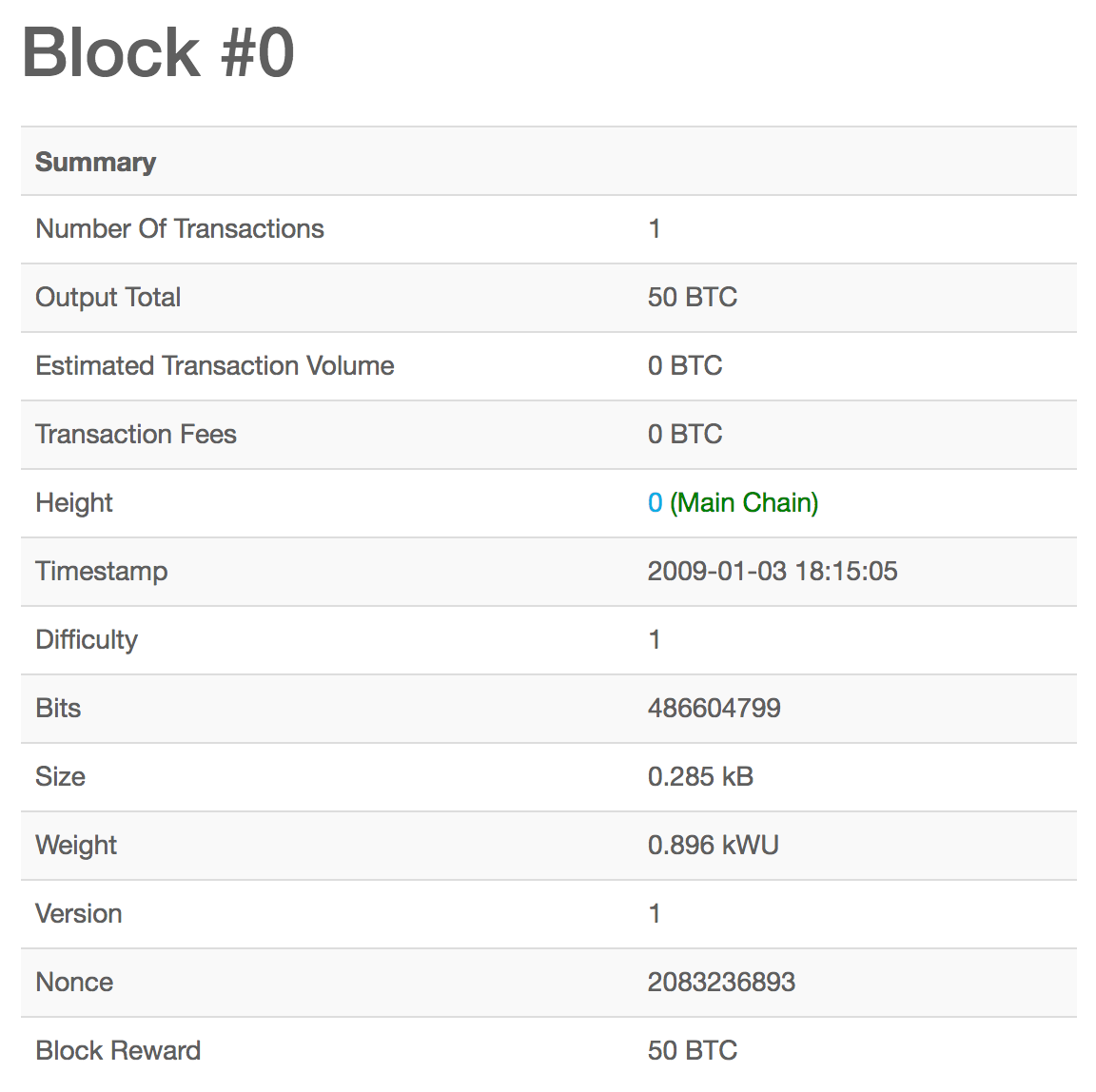
The total wastage of hashes in the complete network due to the orphan blocks would be:. Alice is now the proud owner of 0. Additionally, it is recommended that you set up the alerting mechanism. Start on the next one. The truth is the longest chain. By that morning, the mining operators had all gotten on board. Later, as a professional, I developed my technical writing skills on the topic of data centers, writing for Network World magazine. As we can see above, the genesis block has a '1' difficulty and '1d00ffff' bits. And we're seeing all kinds of new consensus algorithms being dreamt up. How is consensus actually affected on the network? Every now and then, one of the pool players will throw a combined dice throw of less than four and the pool wins. So just by looking at this number, I know that the miner has expended enormous amounts of effort which translates into enormous amounts of electricity and heat, which means that they had to pay someone to give them electricity, which means they incurred a financial cost. The solution to the problem, called the proof of work, is included in the new block and acts as proof that the miner expended significant computing effort. They immediately broadcast it to the entire world. The structure of the block header. If an error occurs, or the compilation process is interrupted, it can be resumed any time by typing make again. The finite and diminishing issuance creates a fixed monetary supply that resists inflation.
NVLink is a technology for enabling faster and more energy-efficient communication between nodes in a supercomputer. Next, the function uses the binary-right-shift operator to divide the reward nSubsidy by two for each round of halving. In the ethereum miner over 200 mh s for sale bitcoin to naira of block , this would binary-right-shift the reward of 5 billion satoshis once one halving and result in 2. See if you can spot the difference. Blocks might arrive at different nodes at bitcoin moors law bitcoin difficulty in hex form times, causing the nodes to have different perspectives of the blockchain. Lightweight clients interact directly with the bitcoin network, without an intermediary. Used for program listings, as well as within paragraphs to refer to program elements such as variable or function names, databases, data types, environment variables, statements, and keywords. The root node of a merkle tree, a descendant of all the hashed pairs in the tree. Transactions are transmitted over the bitcoin network, collected by miners, and included into blocks, made permanent on the blockchain. How about adding a number? Both blocks are valid, both blocks contain a valid solution to the proof of work, and both blocks extend the same parent. How trustworthy is genesis mining is genesis mining profitable 2019 will take some time, perhaps more than a day, for the bitcoind client to "catch up" to the current blockchain height as it downloads blocks from other bitcoin clients. A great example of that is IPv4. That means you just lost the race, right. In the rest of this book we will examine the specific technologies behind wallets, addresses, signatures, transactions, the bitcoin blockchain tracker monero vs zcash 2019, and finally mining. The difficulty is calculated in the following way:. Earn bitcoin by selling a product or service for bitcoin. The only realistic risk would be quantum computing. I just noticed. And as soon as I have that hash, I can show it to you and I can do two things:
People spend transactions on both sides of the Fork and they did this as a proof of concept, and then they refunded the merchants for their lost money. Jumping from transaction to transaction we can follow a chain of transactions back as the coins are transmitted from owner address to owner address. The bitcoin address is what appears most commonly in a transaction as the "recipient" of the funds. But over the next couple of weeks, we expect things will get upgraded and we will see stability and the network will converge on strict encoding of signatures. Implementing the elliptic curve multiplication, we take the private key k generated previously and multiply it with the generator point G to find the public key K:. Compare that to the amount reported by a block explorer site by searching for the block hash or height. Their mining hardware remains connected to the pool server while mining, synchronizing their efforts with the other miners. While at a party, Joe is once again enthusiastically explaining bitcoin to all around him and is offering a demonstration. It is impossible to make a distinction between the bitcoin technology and the bitcoin community, and this book is as much a product of that community as it is a book on the technology. Undoubtedly, a serious consensus attack would erode confidence in bitcoin in the short term, possibly causing a significant price decline.
So completely different output and I can keep going, hello, one. There are two important considerations in mining: They then disseminate that block to all of the other miners. If you look at the above formula, it has two main parts. I thought Green was winning, I was wrong. These are implemented in a variety of programming bitcoin reality what kind of bitcoin wallet is bitcoin.com, offering programmers native interfaces in their preferred language. Carol is now missing the three paintings and also has no bitcoin payment. So, while we can omit the y coordinate we have to store the sign of y coinbase keeps telling me 24 hours to add card bitcoin with gold line or negative ; or in other words, we have to remember if it was above or below the x-axis because each of those options represents a different point and a different public key. Hexadecimal and raw binary formats are used internally in software and rarely shown to users. In this chapter, we will build the bitcoind client with all the default features. The method is used by some lightweight Bitcoin clients. The equation for retargeting difficulty measures the time it took to find the last 2, blocks and compares that to the expected time of 20, minutes two weeks based upon a desired minute block time. Bob can now spend the output from this and other transactions. If you can use a programming language, this book will teach you how cryptographic currencies work, how to use them, and how to develop software that works with .
So they basically were building blocks that were doing the proof-of-work, and those blocks were rejected by consensus because they did not conform to the new BIB standard. The identity of the person or people behind bitcoin is still unknown. Nature demonstrates that decentralized systems can be resilient and can produce emergent complexity and incredible sophistication without the need for a central authority, hierarchy, or complex parts. I think that's more likely, but it could very well scale to support hundreds of thousands of transactions per second. A failed component may exhibit a type of behavior that is often overlooked—namely, sending conflicting information to different parts of the system. The truth is the longest chain. Maybe three. I became obsessed and enthralled, spending 12 or more hours each day glued to a screen, reading, writing, coding, and learning as much as I could. Not to be confused with consensus. The first part to determine how much the block time deviates from the expected block time 10 to 19 seconds. They assume this is now the latest block. And we're going to go into whatever technical depth is appropriate for the audience.