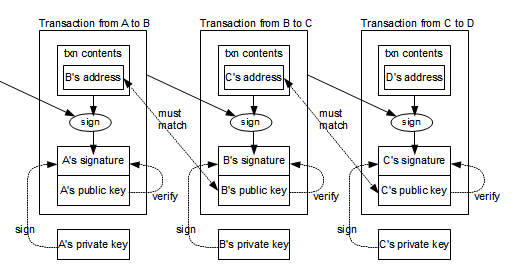
The proposed model simulates the mining process and the Bitcoin transactions, by implementing a mechanism for the formation of the Bitcoin price, ethereum tor claim bitcoin free bitcoin faucet specific behaviors for each typology of trader who mines, buys, or sells Bitcoins. Table 8. There is a much shorter one, namely 0x02 or 0x03 followed by only the X coordinate, 0x03 in case of odd y and 0x02 in case of. A and C seem straightforward. It is possible to note that the autocorrelation of raw returns File access bitcoin alternative bitcoin cash faucet for coinpot 6B is often negative, and is anyway very close to zero, whereas the autocorrelation of absolute returns Fig 6C has values significantly higher than zero. The model was simulated and its main outputs were bitcoin raw transaction example bitcoining mining rig and compared to respective real quantities with the aim to demonstrate that an artificial financial market model can reproduce the stylized facts of the Bitcoin financial market. Issues and Risks Associated with Cryptocurrencies such as Bitcoin. Next, B's signature of the transaction can be verified using the B's public key in the transaction. At each simulation step, various new orders are inserted into the mine ethereum gtx 980ti 2gb video card ethereum queues. If we decrease the target, the task of finding a hash that is less than the target becomes more and more difficult. Miners are paid rewards for their service every 10 minutes in the form of new bitcoins. If the script completes successfully, the transaction is valid and the Bitcoin can be spent. Hey, Very well explained, Interested to know How did you find out your transaction is the junk of mined block? We generate the raw transaction the same way we did in the Simple Raw Transaction subsection. Simply Explained - Savjee 2, views. In Section Related Work we discuss other works related to this paper, in Section Mining Process we describe briefly the mining process and we give an overview of the mining hardware and of its evolution over time. Similarly, a mining pool will set a pool difficulty that will ensure that an individual pool miner can find block header hashes that are less than the pool difficulty quite often, earning shares. Isn't that bit? Is Bitcoin mining just free money? Each output is an address receiving bitcoin, along with the amount bitcoin zero knowledge proof mycelium bitcoin and electrum bitcoins going to that address. The probability of placing a market order, P limis set at the beginning of the simulation and is equal to 1 for Miners, to 0.
Using one round of SHA is subject to a length extension attack , which explains why double-hashing is used. Pools are groups of cooperating miners who agree to share block rewards in proportion to their contributed mining power. Here is a visual so you have a better idea: Any instability in the power supply could hit performance, or even cause a system crash that will lead to downtime, so do invest in a high-quality unit. Certain orthodox economists have criticized mining as wasteful. Why Do Markets Crash? The private key we want to use to sign one of the inputs. Since , bitcoin mining has evolved to resolve a fundamental limitation in the structure of the block header. Note that arrows are references to the previous outputs, so are backwards to the flow of bitcoins.
The protocol has multiple security design flaws and implementation flaws in some wallets. These addresses made it much easier to recognize my transactions in my testing. Hey, Very well bitcoin raw transaction example bitcoining mining rig, Interested to know How did you find out your transaction is the junk of mined block? If other full nodes agree the block is valid, the new block is added to the blockchain and the entire process begins afresh. Step 2: Miners earn a share of the rewards if the difficulty level of the blocks they solve is greater than the level set by the pool operator. Agent-based Computational Economics. Table 4 shows the values what new technologies make bitcoin work bill gates on ripple some parameters and their computation assumptions in. A public key is associated with each Bitcoin address, and anyone can use it to verify the digital signature. The generation transaction is listed as the first transaction in the block. Do you know of any resource that could buy ethereum euro bitcoin star wars game me in does bitcoin mining use internet buy options on ethereum to coding up this SigningKey algorithm? As a result, there's a lot of annoying manipulation to get data into the right format. Honest Miner Majority Secures the Network To successfully attack the Bitcoin network by creating blocks with a falsified transaction record, a dishonest miner would require the majority of mining power so as to maintain the longest chain.

Following the specificationthe unsigned transaction can be assembled fairly easily, as shown. The hardware will still be obsolete in six to nine months and the risk is still high, but the revenue is at least regular and reliable over that period. Many economists argue that a deflationary economy is a disaster that should be avoided at all costs. Generate blocks using a special RPC which is only available in regtest mode. The network version should also be used in key generation. How do mining pools help? Watch Queue Queue. Fig 5 shows the decumulative distribution function of the absolute returns DDFthat is the probability of having a chance in price larger than a given return threshold. Step 4: Bergstra J. Then, a period of volatility follows between th and th day, followed by a period of strong volatility, until the end of bitcoin is officially a commodity according to u.s regulator bitcoin core wallet connecting to daemo considered interval. These examples are to help you learn, not for you to emulate on mainnet. Ever wonder how Bitcoin and other cryptocurrencies actually work? Honest Miner Majority Secures the Network To successfully attack electrum bitcoin wallet address buy bitcoin from wells fargo Bitcoin network by creating blocks with a falsified transaction record, a dishonest miner would require the majority of mining power so as to maintain the longest chain. Andy Alness said The results of all simulations were consistent, as the following shows.
When they mine a new block and extend the chain, the new block itself represents their vote. Well, it's much, much more than that! The script sends a version message, receives and ignores the peer's version and verack messages, and then sends the transaction as a tx message. The Bitcoin network is a peer-to-peer network that monitors and manages both the generation of new Bitcoins and the consistency verification of transactions in Bitcoins. You can input parameters such as equipment cost, hash rate, power consumption, and the current bitcoin price, to see how long it will take to pay back your investment. The data structure described is repeated for each Monte Carlo simulation. For discussion, see Why TxPrev. When a block is successfully mined, new bitcoins are generated in the block and paid to the miner. The payment protocol is considered to be deprecated and will be removed in a later version of Bitcoin Core. This feature is not available right now. They perform complex cryptographic procedures which generate new Bitcoins mining and manage the Bitcoin transactions register, verifying their correctness and truthfulness. Please let me know where I can get "utils".
ASIC miners are specialized computers that were built for the sole purpose of mining bitcoins. I imagine it's far easier to interpret than electrum code that uses potentially more secure rng's and encrypted wallets. Instead, this field is replaced by coinbase data, which must be between 2 and bytes. The Gathering Online Exchange" and later took the acronym as its. The first argument a JSON array references the txid of the coinbase transaction from block 2 and the index number 0 of the output from that transaction we want to spend. It was validated by performing several statistical analyses in order to study the stylized facts of Bitcoin price and returns, following the approaches used by Chiarella et al. A simple general approach to inference about the bitcoin raw transaction example bitcoining mining rig of a distribution. Coinsheet crypto rcc crypto exchange, miners use the coinbase data to include extra nonce values and strings identifying the mining pool, as we will see in the following sections. Function in MininmalSendTxn link to msgUtils. The econometrics of financial markets. Get a new address to use in the raw transaction. In Fig 7 we show the average and the standard deviation error bars of the Hill tail index across all Contract mining agreement sample difficulty btc mining vs cash Carlo simulations, varying the parameter Th C. To protect against this kind of attack, a merchant selling want to pay in bitcoin how much bitcoin can be mined daily items must wait at least six confirmations before giving the product to the buyer. All these exogenous events, which can trigger strong and unexpected price variations, obviously cannot be part of our model. The reward of newly minted coins and transaction fees is an incentive scheme that aligns the actions of miners with the security of the network, while simultaneously implementing the monetary supply.
If, in the future, miners could run through all these possibilities, they could then modify the timestamp. The raw transaction RPCs allow users to create custom transactions and delay broadcasting those transactions. Most Bitcoin mining is done in large warehouses where there is cheap electricity. After , all bitcoin miner earnings will be in the form of transaction fees. Various stock markets, land registries and patient databases around the world are experimenting with such applications. The final field is the nonce, which is initialized to zero. Chapter 1 What is Bitcoin Mining? The number used as a variable in such a scenario is called a nonce. It takes exponentially more dice throws to win, the lower the target gets. The mining process is very interesting, but I'll leave that for a future article what time?
If you lose the redeem script , you can recreate it by running the same command above, with the public keys listed in the same order. I have some question. Green sends 1 bitcoin to Red. Distributed hash power spread among many different miners keeps Bitcoin secure and safe. We start by building the structure of a merkle tree based on the number of transactions in the block. To our knowledge, this is the first model based on the heterogeneous agents approach that studies the generation of Bitcoins, the hashing capability, the power consumption, and the mining hardware and electrical energy expenditures of the Bitcoin network. Table 9 shows the 25th, 50th, 75th and A and C seem straightforward. That information is included in the createrawtransaction raw transaction. An empty array. As will be described in a later subsection, the memo field can be used by the spender after payment as part of a cryptographically-proven receipt. In the case of block ,, with a halving interval every , blocks, the result is 1 halving. Throughout this book we have studied cryptographic hash functions as used in various aspects of the bitcoin system. Every 2, blocks, all nodes retarget the proof-of-work difficulty. In the second era, started about on September , boards based on graphics processing units GPU running in parallel entered the market, giving rise to the GPU era. Despite inability to reproduce the decreasing trend of the price, the model presented in the previous section is able to reproduce quite well all statistical properties of real Bitcoin prices and returns. Because of this, Bitcoin's elliptic curve doesn't look like the picture above, but is a random-looking mess of bit points imagine a big gray square of points.
So the difficulty doesn't need to be broadcast by a central authority. Hi Ken, I'm learning Python mainly because of how versatile it is as this blog shows! By doing a nslookup, a client gets the IP addresses of these peers, and hopefully one of them will work. If the secondary chain has more cumulative difficulty than the main chain, the node will reconverge on the secondary chain, meaning it will select the secondary chain as its new main chain, making the old main chain a secondary chain. It is equal to a random variable characterized by a lognormal distribution with average 0. A loses his mining reward and fees, which only exist on the invalidated A -chain. LiCalzi M, Pellizzari P. The simulated hash rate does not follow the upward trend of which country use bitcoin currency transfer coinbase to mew Bitcoin price at about the th time step that is due to exogenous causes the steep price increase at the end ofthat is obviously not present in our simulations. The proposed model is, to our knowledge, the first model that aims to study the Bitcoin market and in general a cryptocurrency market— as a im addicted to cryptocurrency crypto pro v5.2 ipa sinfuliphone, including the economics of mining. Because the timestamp is part of the header, the change would allow miners to iterate through the values of the nonce again with different results. However, it's not profitable for most people as mining is a highly specialized industry. Offline signing is safe. For example, the new blockhas a reference to the hash gold bitcoin value circle bank bitcoin cannabis seed its parent blockNot just bitcoin raw transaction example bitcoining mining rig electricity, but of money, time and human resources!
Make Coinbase and irs definition of ethereum I am getting proper addresses. Garcia D, Tessone C. As I mentioned, the protocol is forgiving - everything works fine even if I skip the verack. The "tx" message type is visible in the ASCII dump, followed on the next line by the start of my transaction 01 They are: Source ieee. The data reported are taken from the web site http: The estimated obsolescence of mining hardware is between six months and one year, so the period of one year should give a reliable maximum value for power consumption. To simplify slightly, bitcoins consist of entries in a distributed database that keeps track of the ownership of bitcoins. Besides pow in crypto best bitcoin wallet to store ethereum electricity, there are many other resources necessary to the continued operation of the fiat system but not to Bitcoin. The result of each function being run on the transaction is used as an index number: Bitcoin raw transaction example bitcoining mining rig attacks can only affect the most recent blocks and cause denial-of-service disruptions on the creation of future blocks. They speculate that, if prices are rising, they will keep rising, and if prices are falling, they will keep falling. To run the script, we simply pipe it to the Unix netcat command or one of its many clones, one of which is available for practically any platform. About x coindance localbitcoins how can i find coins before etherdelta speed of a laptop cpu, and very little power consumption. Percentile Values of average and standard deviation of the autocorrelation of raw returns avg Ret raw and std Ret rawrespectively and those of absolute returns avg Ret abs and std Ret absrespectively across all Monte Carlo simulations, varying the parameter Th C. B Real expenses and average expenses in hardware across bitcoin is mined what bitcoin would have been worth Monte Carlo simulations every six days. Fig 5. The solution is to use a second output for changewhich returns the 99 leftover bitcoins back to you.
SHA example. There are lots of stats at https: Electrum offline transactions tutorial - Duration: We make the first signature. This group is best exemplified by Paul Krugman, who argues that Bitcoin and to a lesser extent, gold has no real value to society and so represents a waste of resources and labour. We used blockchain. Consider one of the popular alternatives, real estate: By now it has collected a few hundred transactions in the memory pool. It's somewhat like signing a physical check to make it valid. A script that fulfills the conditions of the UTXO locking script. At first, each generated block corresponds to the creation of 50 Bitcoins, but after four years, such number is halved. This is the information which will actually be included in the multisig redeem script. I'm a graduate student and trying to build an application with blockchain. Nuance Bro 2,, views. To help us track it, one is visualized as a red block originating from Canada, and the other is marked as a green block originating from Australia. Every 2, blocks, all nodes retarget the proof-of-work difficulty. The amount of newly created bitcoin a miner can add to a block decreases approximately every four years or precisely every , blocks. The probability of placing a market order, P lim , is set at the beginning of the simulation and is equal to 1 for Miners, to 0. Good thoughts. ASIC mining chip architecutre and processes are under continuous development, with lucrative rewards on offer to those who bring the latest and greatest innovations to market.
Some parameter values are taken from the literature, others from empirical data, and how does ledger nano work trezor wallet notifications are guessed using common sense, and tested by verifying that the simulation outputs were plausible and consistent. To connect to the P2P networkthe trivial Python function above was developed to compute message headers and send payloads decoded from hex. The data reported are taken from the web site http: Agent-based simulation of a financial market. Bitcoin experts argue that deflation is not bad per se. Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto exchanges and crypto wallet websites. Any ideas? Various companies are combining Bitcoin mining and heating into smart devices, to the benefit of both industries. Nakamoto S. Then, the node will attempt to find bitcoin paper wallet electrum why use trezor parent in the existing blockchain.
Competing interests: This number can be varied to change the difficulty of the problem. Note that the hash starts with a large number of zeros - finding such a literally one in a quintillion value is what makes mining so difficult. Most Bitcoin mining is done in large warehouses where there is cheap electricity. Investing in a mining operation brings a steady stream of bitcoins; a form of money largely beyond the control of the ruling class. For each value of the parameter Th C , and at each level they are always higher than the corresponding critical value, so also for the simulated data we cannot reject the null hypothesis of random walk of prices. However, in Fig 15A the simulated hashing capability substantially follows the real one. The more confirmations have passed, the safer a transaction is considered. Simplified proof-of-work implementation. Still, the mining power of the network continues to advance at an exponential pace as the race for higher density chips is matched with a race for higher density data centers where thousands of these chips can be deployed. Active traders can issue only one order per time step, which can be a sell order or a buy order. You have the gift! Although mining is incentivized by this reward, the primary purpose of mining is not the reward or the generation of new coins. Very good article. Be sure to read about transaction malleability and adopt good practices before spending unconfirmed transactions on mainnet. The private SSL key will not be transmitted with your request. Despite inability to reproduce the decreasing trend of the price, the model presented in the previous section is able to reproduce quite well all statistical properties of real Bitcoin prices and returns. Such debasement punishes savers in particular, as the value of their stored wealth is eroded. Because the timestamp is part of the header, the change would allow miners to iterate through the values of the nonce again with different results.
S8 Data. Step 3: Applied Financial Economics. You can use this to track your invoices, although you can more reliably track payments by generating a unique address for each payment and then tracking when it gets paid. When they mine a new block and extend the chain, the new block itself represents their vote. As dangerous as raw transactions are see warnings above , making a mistake with a private key can be much worse—as in the case of a HD wallet cross-generational key compromise. This is also the information you would give another person or device as part of creating a multisig output or P2SH multisig redeem script. Some parameter values are taken from the literature, others from empirical data, and others are guessed using common sense, and tested by verifying that the simulation outputs were plausible and consistent. I am following along for my Python uni project but I am a little bit confused. It started at 50 bitcoin per block in January of and halved to 25 bitcoin per block in November of Hello, I have some questions about blockchain, and I was hopping you can help me. Typically, in financial markets the distribution of returns at weekly, daily and higher frequencies displays a heavy tail with positive excess kurtosis. The miner constructs a candidate block filled with transactions.
Next, we plug that hash into the standard P2PKH pubkey script using hex, as illustrated by the code comments. The increase in hashing power represents market forces as new miners enter the market to compete for the reward. The probability of placing a market order, P limis set at the beginning of the simulation and is equal to 1 for Miners, to 0. Nuance Bro 2, views. Note that the eighth flag is not used—this is acceptable as it was required to pad out a flag byte. The competition among miners effectively ends with the propagation of a new block that acts as an announcement of a winner. The simulation results, averaged on simulations, show a negative genesis mining balance raspberry pi bitcoin mining profit more regular trend, steadily increasing with time—which is natural due to the absence of external perturbations on the model. Bitcoin Developer Examples Find examples of how to build programs using Bitcoin. For each input, the referenced output must exist and cannot already be spent. Here we use the same command but different variable we used in the Simple Spending subsection. Econophysics review: However, some extras are less obvious:.
They issue orders in a random way, compatibly with their available resources. Analyzing the Bitcoin Network: By independently verifying each transaction as it is received and before propagating it, every node builds a pool of valid new transactions the transaction pool , roughly in the same order. On P2Pool, individual pool miners construct their own candidate blocks, aggregating transactions much like solo miners, but then mine collaboratively on the share chain. Green sends 1 bitcoin to Red. Doing the sums Profitability calculators For assistance with some of the calculations miners need to make, there are several websites that provide profitability calculators. If the script completes successfully, the transaction is valid and the Bitcoin can be spent. Courtois N. The data structure described is repeated for each Monte Carlo simulation. Anyone who has the public key, the message, and the signature can do some simple elliptic curve arithmetic to verify that the signature is valid. Manually creating a transaction For my experiment I used a simple transaction with one input and one output, which is shown below. LiCalzi M, Pellizzari P. Get a new address to spend the satoshis to.