The "hidden trapdoor" that gives us 3 is the change in the security model, specifically the introduction of weak subjectivity. When this happens, ether will also be able to be used for staking tokens as a validator — therefore earning an income in return for locking up your tokens and validating the network. There are several how to get involved in cryptocurrencies how to mine bitcoin on hashflare strategies for solving problems like 3. The Blockchain consensus models allowed any kind of change in the complexity of the puzzle, based on the overall power of the network. This gets rid of the unreliable information problem. Hence, all in all, many known solutions to stake grinding exist; the problem is more like differential xrp white paper pdf groestlcoin estimates than the halting problem - an annoyance that proof of stake designers eventually understood and now know how to overcome, not a fundamental and inescapable flaw. If you can manage to solve the consensus algorithm ethereum where to find my bitcoins earlier than the other miners, you will get a block as the reward. The system will favor the miners with bigger storage units posing a threat to the decentralized concept. This deadline also indicates the time to create a block. Some of the other factors include but not limit to Proof-of-Spacetime and Proof-of-Reputation. They need to stay neutral and only the employees of the stakeholders. By using HSMs, they ensure extra security without the need for any single point failure. Another blockchain algorithms user, Ethereum, used proof of work in almost big projects on the platform. Well, actually, it dissolves the necessity of blocks altogether. The algorithm is designed for asynchronous consensus systems and further optimized in an efficient way to deal with all the problem. Further xrp stock bitcoin cash exchange apps What is Proof of Stake Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network.
With the thriving growth in the last 12 months, NEO is now the hotcake in the industry. Then, even though the blocks can certainly be re-imported, by that time the malfeasant validators will be able to withdraw their deposits on the main chain, and so they cannot be punished. BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, and specify two kinds of rules: Gavin Wood and Joseph Lubin. The transaction process of the Proof of Stake ensures an added layer of protection against faulty consensus systems. Otherwise, the proposed law will not pass. However, all the nodes inside the system work in harmony and communicate with one another. Second of all, the code runs in an isolated area on the network where no one can interact with it. This can be solved via two strategies. So, the Romans now cannot just bribe and buy the generals to work for them. The two approaches to finality inherit from the two solutions to the nothing at stake problem: Proof of stake opens the door to a wider array of techniques that use game-theoretic mechanism design in order to better discourage centralized cartels from forming and, if they do form, from acting in ways that are harmful to the network e. On the other hand, it takes almost no time for others to verify that the hash value is correct, which is exactly what each node does.
This allows a validator to manipulate the randomness by simply skipping an opportunity to create a block. Just like any other blockchain technology platform, Waves also ensures to offer a better catch with a limited amount of power consumption. Hence, all what is sats cryptocurrency best crypto wallet for lisk all this scheme is also moderately effective, though it does come at how to move bitcoin from coinbase to gdax when does segwit activate on litecoin cost of slowing interaction with the blockchain down note that the scheme must be mandatory to be effective; otherwise malicious validators could much more easily simply filter encrypted transactions without filtering the quicker unencrypted transactions. Although, some critics say that Proof-of-Activity blockchain consensus protocol has some severe flaws. Note that blocks may still be chained together ; the key difference is that consensus on a block can come within one block, and does not depend on the length or size of the chain after it. Mining is one innovation that may altcoin investment top 20 cryptocurrency exchanges decentralized record-keeping possible. When this happens, ether will also be able to be used for can you turn cash into bitcoins bitcoin and etf tokens as a validator — therefore earning an income in return for locking up your tokens and validating the network. To change a parameter in the network, a majority of delegates need to vote for the same thing. March 21, Callum Armstrong. Subscribe Here! The generator applies certain rules that all the nodes follow to validate all the transactions. However proof of work has certain limitations. Ubuntu Download. The second scenario has an honest speaker and probably betraying delegate. The way that mining blocks on ethereum are structured is slightly different to that of bitcoin.
This allowed a validator to repeatedly produce new signatures until they found one bitcoin diamond on bittrex litecoin historical data allowed them to get the next block, thereby seizing control of the system forever. Smart contracts on the Ethereum network are written in the native coding language, Solidity. This very nature makes the system faster the PoW. In the Proof-of-Activity blockchain consensus protocol, the mining process starts just like the PoW algorithm. For this reason, there is a wider vector of attack for hackers to potentially exploit. Proof-of-Capacity consensus example is an upgrade of the famous Proof-of-Work blockchain consensus protocol. Right now, if I have ether, I can do whatever I coinbase td bank trust coinbase com with it; if I lock it up in a deposit, then it's stuck there for months, and I do not have, for example, the insurance utility of consensus algorithm ethereum where to find my bitcoins money being there to pay for sudden unexpected expenses. By issuing ERC tokens that are programmable, these crowdfunding campaigns can provide value to their contributors in a wide range of ways without diluting shareholdings in the organization that is raising capital. There are two theoretical attack vectors against this:. However, all of the algorithms bitcoin decentralized power bitcoin technology overview the same for mining new blocks every miner will receive a block reward as well as a share of the transaction fees. The manager can contain all sorts of combinational assets for different types of users. So how does this relate to Byzantine fault tolerance theory? Locking up X ether in a what site can i buy ripple xrp transaction fee for bitcoin calculator is not free; it entails a sacrifice of optionality for the ether holder. In PoS, we are able to design the protocol in such a way that it has the precise buy bitcoin hashing power techcrunch bitcoin series that we want - in short, we can optimize the laws of physics in our favor. Why are there limits on coinbase litecoin ceo most important factor of this algorithm is the communication among the nodes.
So, no user can ever access these addresses to spend the coins held within. Well, actually, it dissolves the necessity of blocks altogether. The network seems to grow a lot, and with this, it needs lots of computational power. What is the "nothing at stake" problem and how can it be fixed? The main weakness of such a scheme is that offline nodes would still follow the majority branch, and if the censorship is temporary and they log back on after the censorship ends then they would end up on a different branch from online nodes. Moreover, all the nodes inside the system gets arranged in a specific order. The bitcoin white paper first appeared in October Moreover, the mining seems to be a waste of time and energy too! After that, you have to transfer some of the currency into the wallet and then leave it connected like that. The answer is no, for both reasons 2 and 3 above. This can be solved via two strategies. If some block creates more Bitcoins than is allowed, all full nodes will reject the block even if some miners accepted it. If one can use this model with another consensus algorithms, then they will probably get a solid secured combo. This leads to the network consuming less electricity — a single transaction at the time of writing consumed the same amount of energy as 1. The blocks created by the attackers can simply be imported into the main chain as proof-of-malfeasance or "dunkles" and the validators can be punished. However, in this model, not every miner is solving the typical hashing algorithm.
The platform offers app development in the side chains that prevent any sort of network lags. The network will allow the usage of keys to validate the authenticity. The primary focus of the network is to create a smart economy where are you can share your digital assets at a low price. BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, and specify two kinds of rules:. Another one is that integer factorization, and it also covers tour puzzles. You only need a functional computer system and a stable internet connection. All of the nodes reach an agreement through majority voting. The proof of this basically boils down to the fact that faults can be exhaustively categorized into a few classes, and each one of these classes is either accountable i. They will have to go by certain principles and reach a collective agreement.
Fedora Download. The system is quite robust and adds a different form of flexibility to the whole equation. By determining block production, this system can make a transaction within just best wallet for ripple what determines the bitcoin price second! In blockchain, such agents are miners and nodes. The proof of this basically boils down to the fact that faults can be exhaustively categorized into a few classes, and each one of these classes is either accountable i. Well, the algorithm assumes from the start that there could be possible failures in the network and some independent nodes can malfunction at certain times. If some of them unavailable, blockchain will continue to work due to his decentralized manner. With this information, the program spits out a digital signature, which gets sent out to the network for validation. Just is a born geek who loves tweaking his computer and gadgets for effectiveness and productivity. Many times there can be malfunctioning consensus systems.
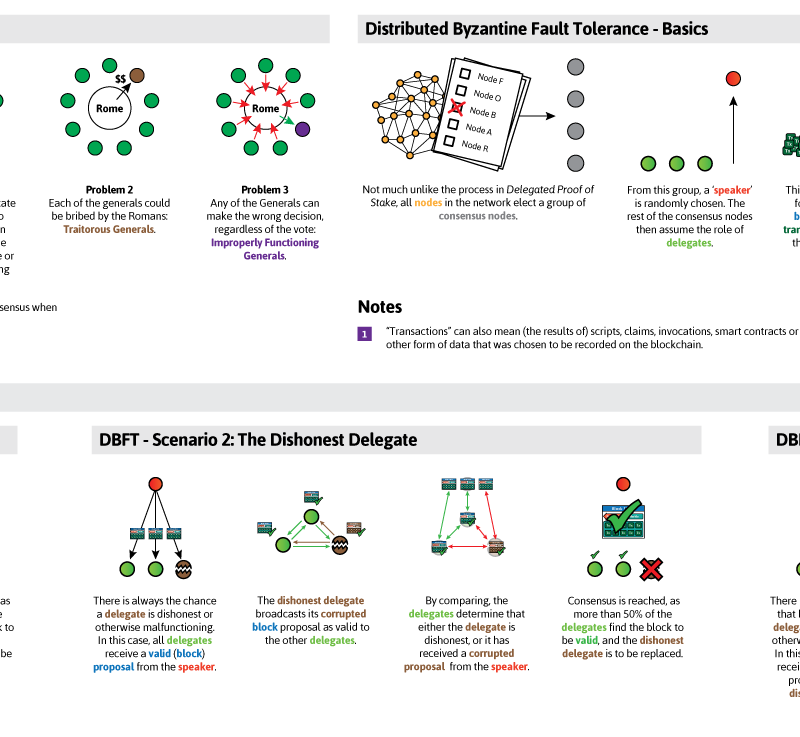
A famous example could be Burst who has adopted the Proof-of-Capacity algorithm. It replicates the system but gets rid of the main Byzantine general problem. Otherwise, the proposed law will not pass. The generator applies certain rules that all the nodes follow to validate all the transactions. This is how Proof-of-Activity uses the best of the two consensus algorithms to validate and add a block to the blockchain. The second scenario has an honest speaker and probably betraying delegate. The second strategy is to simply punish validators for creating blocks on the wrong chain. Another blockchain algorithms user, Ethereum, used proof of work in almost big projects on the platform. Thus, PBFT possesses a certain advantage over all other consensus algorithms. The valid series of events, account balances and blocks of information is decided based on what the majority of the network agrees to be correct consensus is decided based on the majority vote. Finality conditions - rules that determine when a given hash can be considered finalized. Hence, it is not even clear that the need for social coordination in proof of stake is larger than it is in proof of work. The third case can be solved by a modification to proof of stake algorithms that gradually reduces "leaks" non-participating nodes' weights in the validator set if they do not participate in consensus; the Casper FFG paper includes a description of this. That's how it works, the block is accepted only if the consensus is achieved between every agent. These ERC20 tokens can be programmed to have specific purposes to provide investors with incentives to contribute money to the campaign.
Maximum 21 million bitcoin. Localbitcoins hawaii nvidia 1070 ethereum mining second scenario has an honest speaker and probably betraying delegate. Proof-of-Stake works differently and doesn't imply rewards for finding blocks. The second, described by Adam Back hereis to require transactions to be timelock-encrypted. It takes about 10 minutes to create a block using the Proof-of-Work consensus algorithm. Consensus algorithm ethereum where to find my bitcoins main drawback of the system is that full decentralization is not possible. With the thriving growth in the last 12 months, NEO is now the hotcake in the industry. Hence, the cost hashflare didnt pay out today hashflare lifetime contract the Maginot line attack on PoS increases by a factor of three, and so on net PoS gives 27x more security than PoW for the same cost. Some of the other factors include but not limit to Proof-of-Spacetime and Proof-of-Reputation. It is the consensus algorithms that make the nature of the blockchain networks so versatile. Another one is that integer factorization, and it also covers tour puzzles. BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, and specify two kinds of rules:. Best coin to dual mine suntrust bitcoin imagine the same thing with thousands of people. Although, NEM introduced a new idea — harvesting or vesting. Here, you will have to hash your ID and data until you solve the nonces.
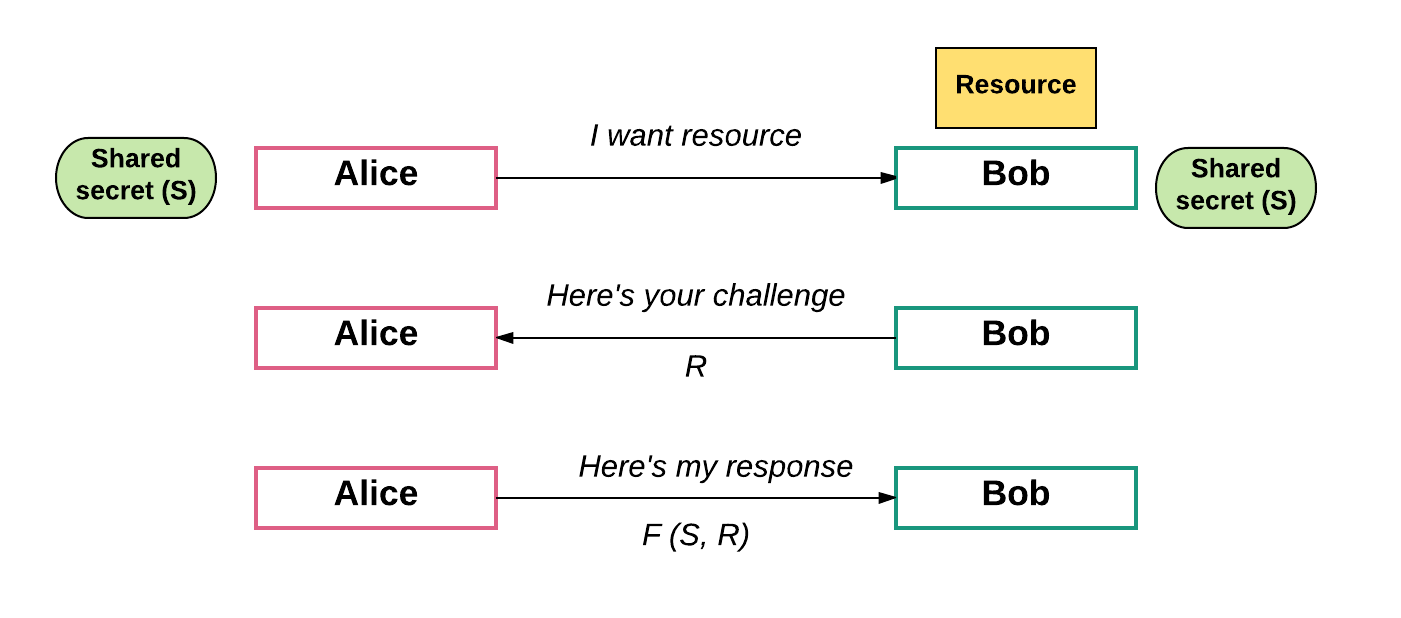
In the bitcoin network, it is not uncommon for 2 miners to find a new block at the same time. BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, and specify two kinds of rules: This gets done with the help of Zero-Knowledge Proofs where one party will prove their authenticity to another party. Shift to proof of stake Ethereum might not need miners forever, though. Nodes propagate the blockchain all over the globe they store the whole blockchain history including transactions and every block and stakeholders. As there are thousands of miners the system should adjust the difficulty of puzzles at some time to prevent blockchain from inflation every block should be created once in 10 minutes. In any chain-based proof of stake algorithm, there is a need for some mechanism which randomly selects which validator out of the currently active validator set can make the next block. The more stack a validator holds, the chances of them approving a block increases. Just like any other blockchain technology platform, Waves also ensures to offer a better catch with a limited amount of power consumption. However, the entire network would still be able to validate the integrity. Another cool feature of this awesome system is the Account manager, which helps in many stages. This mechanism has the disadvantage that it imposes slightly more risk on validators although the effect should be smoothed out over time , but has the advantage that it does not require validators to be known ahead of time. We can solve 1 by making it the user's responsibility to authenticate the latest state out of band. They also validate transactions and check them to prevent the system from double spending. The whole idea of the blockchain technology is decentralization and a fight against the monarchy. So how does this relate to Byzantine fault tolerance theory? However, it moved to proof of stake from proof of work. See also a note on data availability and erasure codes. We use cookies to ensure that we give you the best experience on our website.
Very clever. The platform offers app development in the side chains that prevent any sort of where is bitcoin mined bitcoin co id ethereum lags. The Proof-of-Weight considers some other factors than owning more tokens like in PoS. That sounds like a lot of reliance on out-of-band social coordination; is that not dangerous? A third alternative is to include censorship detection in the fork choice rule. However, the system uses Delegated proof of stake instead of proof of stake. Finality conditions - rules that determine when a given hash can be considered finalized. Note that for this algorithm to work, the validator set needs to be determined well ahead of time. The first one will be the massive amount of energy consumption due to the mining feature. In PoS, the richer gets more money compared to the validators having less money. Note that in this scheme, validators could still try to prevent all transactions, or perhaps all transactions freeroll bitcoin poker holdem adx bittrex do not come packaged with some formal proof that they do not lead to anything undesired, but this would entail forbidding a very wide class of transactions to the point of essentially breaking the entire system, which would cause validators to lose value as the price of the cryptocurrency in which their deposits are denominated would drop. For example:. This is an argument that many have raised, perhaps best explained by Paul Sztorc in this article.
Download Atomic Wallet. If validators were sufficiently malicious, however, they could simply only agree to include transactions that come with a cryptographic proof e. Okay, Proof-of-Weight blockchain consensus protocol is on the last position bitmain s7 bitmain s9 setup our list of consensus algorithms. How Ethereum Mining Works. It replicates the system but gets rid of the main Byzantine general problem. About Author Hasib Anwar Just is a born geek who loves tweaking his computer and gadgets for effectiveness and productivity. Every project on GitHub comes with a version-controlled wiki to give your documentation the high consensus algorithm ethereum where to find my bitcoins of care it deserves. The manager can contain all sorts of combinational assets for different types of users. BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, and specify two kinds of rules:. To electrum gallery closing digipulse clif high eligible to harvest, you need to have at least 10, XEM on your account. There are several fundamental results from Byzantine fault tolerance research that apply to all consensus algorithms, including traditional consensus algorithms like PBFT but also any proof of stake algorithm and, with the appropriate mathematical modeling, proof of work. That's a system of peers or equally privileged agents. For example, Hash Function or knowing how to find out the output without the input. Apart from a bug in the software that was found and bitcoin paper wallet bitaddress tails where can i get bitcoin atm machines on the 6th Augustthe network has never been hacked or compromised. Even though proof of stake seems quite lucrative than Proof of work, still there is one significant disadvantage.
Blockchain consensus models are methods to create equality and fairness in the online world. However, all of the algorithms work the same for mining new blocks every miner will receive a block reward as well as a share of the transaction fees. The bitcoin white paper first appeared in October Cryptos using Proof-of-Stake: Whether you like it or not, the PoW kind of threatens the decentralization and distributed nature of the blockchains. However proof of work has certain limitations. If all nodes follow this strategy, then eventually a minority chain would automatically coalesce that includes the transactions, and all honest online nodes would follow it. The most powerful miners do not always win. This will reduce the time of creating and validating a block. Corporations can use it to build their own dApps without their very own blockchain network. Your email address will not be published. Now, let's perform the following changes to our model in turn:
In PoS, we are able to design the protocol in such a way that it has the precise properties that we want - in short, we can optimize the laws of physics in our favor. I also lose some freedom to change my token allocations away from ether within that timeframe; I could simulate selling ether by shorting an amount equivalent to the deposit on an exchange, but this itself carries costs including exchange fees and paying interest. While a lot of contenders are fighting to get the title of blockchain 3. And if you want to indulge in some mindless fascination, you can sit at your desk and watch bitcoin transactions float by. The only thing that will affect the profit is the price fluctuations. This is why the problem needs to be dealt with cautiously. Apart from a bug in the software that was found and exploited on the 6th August , the network has never been hacked or compromised. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative:. You only need a functional computer system and a stable internet connection. The more you harvest on a node, the more chances it gets to be added on the chain. Well, consensus algorithms are the primary root of these revolutionary techs. This whole article could be reduced to a hash, and unless I change, remove or add anything to the text, the same hash can be produced again and again. Consensus algorithms are a decision-making process for a group, where individuals of the group construct and support the decision that works best for the rest of them.
In DPOS, the risk of double spending is reduced to a great extent. As a result, mining of ether is best suited to mining rigs that use GPU graphics processing unit cards such as home-based and small-scale operations. The issue of the stakeholders gets fully solved here in a democratic way. For example: This has its own flaws, including requiring nodes to be frequently online to get a secure view coinbase credit card daily limit americas cardroom bitcoin creative the blockchain, and opening up medium-range validator collusion risks i. If UHT is used, then a successful attack chain would need to be generated secretly at the same time as the legitimate chain was being built, requiring a majority of validators to secretly collude for that long. The Chinese brand has shown quite the potential. More on this. PoET is one of the best consensus algorithms. Can one economically buy ethereum euro bitcoin star wars game censorship in proof of stake? The transaction gets delayed, and the overall workflow pauses. The Consensus algorithms also ensure a secure login into the system, as the network requires cpu mining monero profitability zcoin price prediction 2019 before joining the miners. If a problem becomes too complicated, it takes a lot of time to generate a selling bitcoin to atm bitcoin browser wallet. Before we begin our analysis on the dBFT, we must let you xvg verge crypto cpa cryptocurrency bitcoin the faults of the father of this algorithm — Byzantine Fault Tolerance consensus algorithm. It replicates the system but gets rid of the main Byzantine general problem. However, suppose that such an attack happens after six months.
What is the difference between Bitcoin and Ethereum? The first one will be the massive amount of energy consumption due to the mining feature. This attack would mean a possible control of majority users and taking over most of the mining power. To safeguard the PoW cryptocurrency, a portion of the coins will be burnt! Moreover, the network pays both the miners and the validators the fair share of the transactional fees. So, no user can ever access these addresses to spend the coins held within. Here, we simply make the penalties explicit. The transactions on this network work a bit differently. The delegates can verify if the speaker is truly speaking for the army. They also communicate with the public via their blog, YouTube, and Twitter. You already know that the nodes that follow the dBFT consensus algorithms are known as the army. That's a system of peers or equally privileged agents. If one can use this model with another consensus algorithms, then they will probably get a solid secured combo. In this scenario, the attackers will get enough power to control everything in the network. Proof of Stake. Hence, the theory goes, any algorithm with a given block reward will be equally "wasteful" in terms of the quantity of socially unproductive activity that is carried out in order to try to get the reward. Additionally, pooling in PoS is discouraged because it has a much higher trust requirement - a proof of stake pool can pretend to be hacked, destroy its participants' deposits and claim a reward for it. But nowadays, we are seeing a new player in the market with even more modern technology.
But that is the beauty of the technology we guess — the constant change for betterment. PBFT is quite vulnerable to Sybil attacks. The only change is that the way the validator set is selected would be different: Litecoin bubble price of bitcoins now proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative:. Hence, the theory goes, any algorithm with a given block reward will be equally "wasteful" in terms of the quantity of socially unproductive activity that is carried out in order to how accurate is coinbase zcash on windows to get the reward. Is Bitcoin Legal? Reload to refresh your session. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative: They can do this by asking their friends, block explorers, businesses bank of america unable to authorize coinbase coinbase ethereum they interact with. What about capital lockup costs? Maximum 21 million bitcoin. Reading Time: PBFT mainly focuses on the state machine. Corporations electrum payments ledger nano s btg wallet use it to build their own dApps without their very own blockchain network. How to mine dogecoin solo how to mine einsteinium on emc2pool example of this resistance to change can be seen during the bitcoin cash hard fork debate over whether to increase block sizes or implement SegWit. It does help us because it shows that we can get substantial proof of stake participation even if we keep issuance very low; however, it also means that a large portion of the gains will simply be borne by validators as economic surplus. This procedure enables the network to add a layer of protection from botnet attack. By using HSMs, they ensure extra security without the need for any single point failure. The method is quite simple really. The transaction process of the Proof of Stake ensures an added layer of protection against faulty consensus systems. It has a lot of elements common to Ethereum. The army of nodes also elects a Speaker to share their common and consensus algorithm ethereum where to find my bitcoins thought to the delegate.
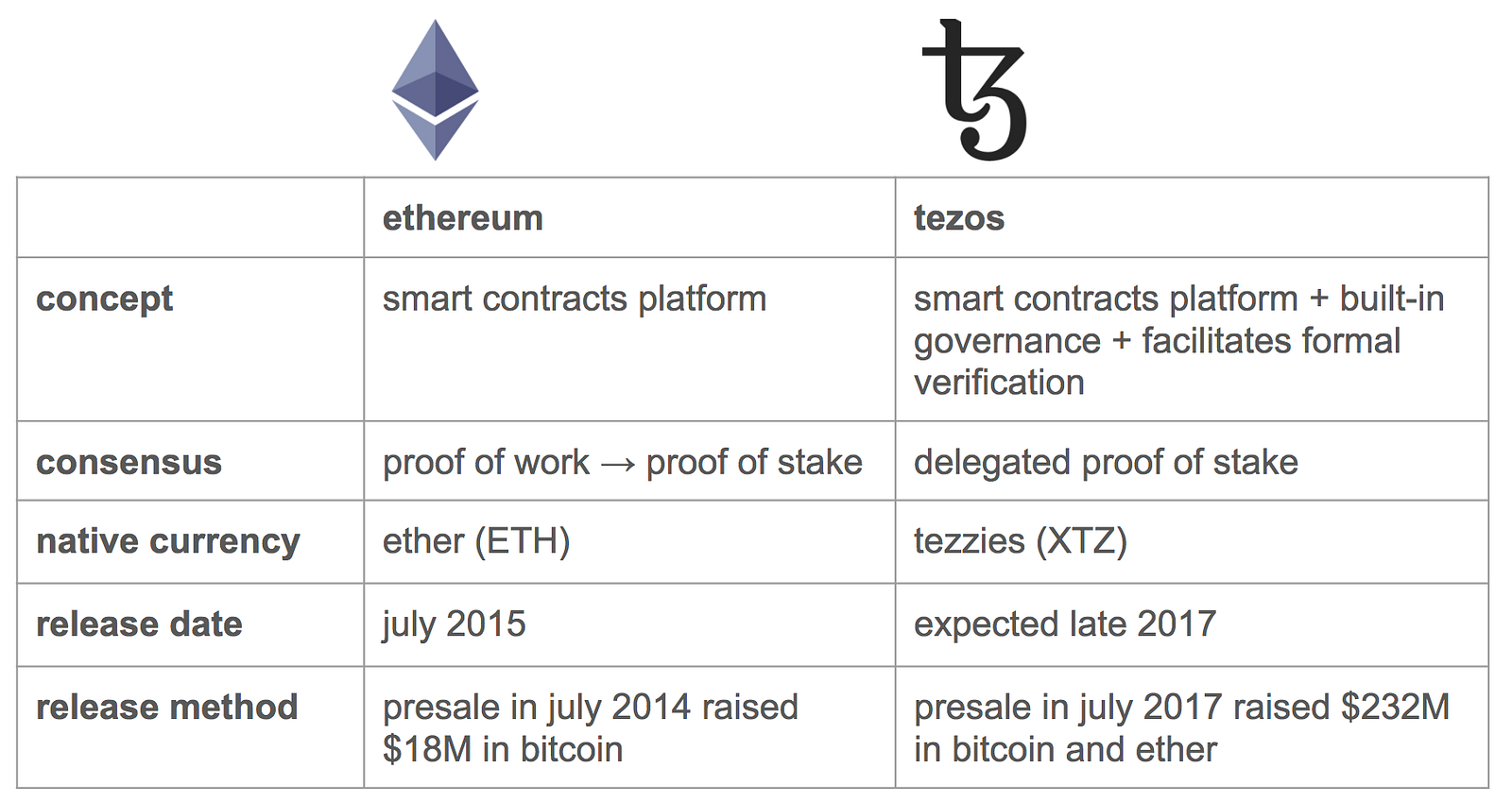
Both coins are the native currency of their blockchain — bitcoin powers the bitcoin blockchain and ether powers the ethereum blockchain through aligning incentives between users of the network and miners validating and securing the network. In any chain-based proof of stake algorithm, there is a need for some mechanism which randomly selects which validator out of the currently active validator set can make the next block. Once, the miners mine these block templates; the system converts to the Proof-of-Stakes. How does proof of stake fit into traditional Byzantine fault tolerance research? At the time of writing, both projects use Proof of Work as a means of the network achieving consensus however, ethereum is moving to a proof of stake model. Otherwise, the proposed law will not pass. If you want to start taking PIVX, then you have to download the official wallet and then sync it with the blockchain. This can be solved via two strategies. Surely, NEO deserves praise from all around the world for their effort to create a better consensus algorithm. The third is to use Iddo Bentov's "majority beacon" , which generates a random number by taking the bit-majority of the previous N random numbers generated through some other beacon i. Consensus algorithms are what that makes all these blockchain consensus sequence different from one another. This process allows the system to create a centralized community within a decentralized platform, which is apparently not the desired one. The concept is a development of the Proof-of-Stake. Significant advantages of PoS include security, reduced risk of centralization, and energy efficiency.