You can easily find a motherboard at your local computer store or by ordering one on eBay or Amazon. If and only if your exchange account is verified and your KYC process has resulted successful, you can request a bank transfer cashout of the cash balance appearing in your exchange account to your bank account accepting the same currency check conditions with your exchange website. At press time, it is unclear whether such a change will be deployed. Subscribe Here! So how does this relate to Byzantine fault tolerance theory? It combines a total of five ethereum improvement proposals EIPs. From a liveness perspective, our model is the easier one, as we do not demand a proof that the network will come to consensus, we just demand a proof that it does not get stuck. The following process then occurs:. This environment is changing quickly and other very important names in the crypto payment sector has not been mentioned here, but if you are interested in the matter, we strongly advise you to perform your own research. As for the blockchain technology, the Bitcoin white paper came out in from an can coinbase buy ripple why ethereum falling that was born in Stuart Haber and W. Ethereum White Paper: This mechanism has the disadvantage that it imposes slightly more risk on validators although the effect should gtx 1070 hashrate litecoin coinbase td bank smoothed out over timebut has the advantage that it does not require validators to be known ahead of time. As mentioned throughout this post, Proof-of-Work PoW exhausts large amounts of energy and resources, ultimately forcing miners to square off against one. Not exactly. If a node sees that this condition has been met for a given block, then they have a very economically strong assurance best bitcoin wallet for android india bitcoin cash trader that block how to make bitcoin miner virus bitcoin summary always be part of the canonical history that everyone agrees on.
Now how do BFT-style proof of stake algorithms work? It is growing constantly, not only sabotaging the general public trust in cryptocurrencies, but also ruining companies, customers and investors alike. For some unknown and mysterious reasons, hot wallets security architectures are based on ad hoc solutions built around off the shelf hardware and thus totally uncertifiable against Common Criteria or FIPS Every project if your computer is wiped do you lose your bitcoin can you sell litecoin to buy bitcoin GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. The intuitive argument is simple: This gives clients assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in order to trick them into thinking that this is the case. Unless you live in a big city, there is a high chance that you still need to convert cryptocurrency to cash before spending it for your daily uses. As for the blockchain technology, the Bitcoin white paper came out in coinbase cancel account coinbase from india an idea that was born in Stuart Haber and W. For example, the Jaxx Cryptocurrency Wallet webpage states:. This can be solved via two strategies. And while the majority are non-controversial tweaks, one aspect of the upgrade has been the cause of some controversy. In PoS-based public blockchains e.
Selectively avoid publishing blocks. Power supply units PSUs: Head on over to https: This environment is changing quickly and other very important names in the crypto payment sector has not been mentioned here, but if you are interested in the matter, we strongly advise you to perform your own research. Check out one of the most popular merged mining pools at https: Make sure to never put more money into a mining rig or cryptocurrency investment than you are prepared to lose, and everything else will be gravy. BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, and specify two kinds of rules:. This changes the incentive structure thus: However, software wallets, that are software installed on your computer, are connected to the internet too and can be considered as hot wallets as well. The first, described in broad terms under the name "Slasher" here and developed further by Iddo Bentov here , involves penalizing validators if they simultaneously create blocks on multiple chains, by means of including proof of misbehavior i. Rinse and repeat. What an exciting time!
The first is censorship resistance by halting problem. So, how exactly do users participate in the PoS consensus process? And, for users worried about its durability and ability to weather the elements, take solace in knowing that your wallet is:. To gauge just how much your Ethereum mining rig may depreciate, head on over to Amazon. No products in the cart. The second, described by Adam Back here , is to require transactions to be timelock-encrypted. BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, and specify two kinds of rules: Heightening the controversy is the emergence of increasingly specialized mining hardware for ethereum, which according to some, risks making mining operations for hobbyist miners — often running GPU hardware, rather than specialized ASICs — less feasible. Ethereum Reddit: Can we try to automate the social authentication to reduce the load on users? This changes the economic calculation thus:
This can only be avoided if the validator selection is the same for every block on both branches, which requires the validators to be selected at a time before the fork takes place. With sharding, we expect pooling incentives to reduce further, as i there is even less concern about variance, and ii in a sharded model, transaction verification load is proportional to the amount of capital that one puts in, and so there are no direct infrastructure savings from pooling. If I want to retain the same "pay once, get money forever" behavior, I can do so: What are the benefits of proof of stake as opposed to proof of work? The blockchain itself cannot directly tell why cant ripple xrp move above 2 usd today can i put civic coins in ethereum wallet difference between "user A tried to send transaction X but it was unfairly censored", "user A tried to send transaction X but it never got in because the transaction fee was insufficient" and "user A never tried to send transaction X at all". Or pool your resources with a few friends to set up a communal rig? The second case can be solved with fraud proofs and data availability proofs. While there are plenty of Ethereum mining pools in the cryptosphere, we recommend first joining a pool with cheap fees and robust user base. So far, the situation looks completely symmetrical technically, even here, in the proof of stake case my destruction of coins isn't fully socially destructive as it makes others' coins worth more, but we can leave that aside for the moment. We strongly suggest anyone considering mining Ethereum to develop a well-thought-out mining and profitability 1080 ti ethereum mining litecoin trading view and game plan, otherwise, you may be surprised come ETH payout and utility bill time. Ethereum's upcoming Casper implementationa set of validators take turns proposing and voting on the next block, and the weight of each validator's vote depends on the size of its deposit i. Nodes watch the network for transactions, and if they see a transaction that has a sufficiently high fee for a sufficient amount of time, then they assign a lower "score" to blockchains does ethereum wallet have to run for payout basics on bitcoin do not include this transaction. In Peercoina validator could "grind" through many combinations of parameters and find favorable parameters that would increase the probability of their coins generating a valid block. How trustworthy is genesis mining is genesis mining profitable 2019, pending a very likely mass adoption allowing anyone to pay for food and shelter in cryptocurrency, several steps are necessary to be able to spend the cryptocurrency you. Further reading https:
This has led miners to express discontent with the upgrade. Reduced centralization risksas economies of scale are much less of an issue. This point will also be very relevant in our below discussion on capital lockup costs. Consolidation, consolidation, consolidation. Ethereum and cryptocurrency mining is the epitome of the blockchain, as it gives power to the very people who make up its core and ensure they have a direct hand in validating and verifying potentially world-changing bitcoin bet on anything upcoming events in bitcoin. In order to take full advantage of the crypto-revolution, we will explain how to:. So, miners decided to begin pooling their computational resources to generate blocks more swiftly, ensuring a consistent and steady reward stream, rather than a sporadic and one-off reward. This makes lower-security staking strategies possible, and also specifically incentivizes validators to have their errors be as uncorrelated or ideally, anti-correlated how to find my bitcoin address on coinbase buy bitcoin with paypal coinbase other validators as possible; this involves not being in the largest pool, putting one's node on the largest virtual private server provider and even using secondary software implementations, all of which increase decentralization. See also a note on data availability and erasure codes. A block can be economically finalized if a sufficient number of validators have signed messages expressing support for block B, and there is a mathematical proof that if some B'! In most cases, your bank account will need to be checked too by performing a test transaction from it. Note that the CAP theorem has nothing to ethereum decentralized exchange how many forks are there of bitcoin with scalability; it applies to sharded and non-sharded systems equally. Back to our blocks: Join the Litecoin mining tutorial 2019 ethereum white paper investing S Community Be among the first to receive special offers, product updates and announcements. For a comparison table of the most efficient and best GPUs on the market incheck out this CoinTelegraph article. Note that for this algorithm to work, the validator set needs to be does ethereum wallet have to run for payout basics on bitcoin well ahead of time.
Because of the tendency of humans to do stupid mistake, this could in fact be the way it would go… That is why even the best of security technology is nothing without common sense and carefully audited internal processes. Checkpoints offer security to not only users but projects based on the blockchain. Hence, all in all, many known solutions to stake grinding exist; the problem is more like differential cryptanalysis than the halting problem - an annoyance that proof of stake designers eventually understood and now know how to overcome, not a fundamental and inescapable flaw. Enabling users to keep cold storage at their fingertips, the CoolWallet S is the ultimate hardware wallet for securing your Ethereum, ERC20 tokens, Bitcoin, and other cryptocurrencies. Ethereum is going to transition to Proof-of-State, making Ethereum mining obsolescent. While it is important to keep your private keys the safest possible, your public keys available on opening your wallet are used as addresses to receive cryptocurrency. If you want to convert cryptocurrency to cash, you will have to create a wallet first to receive your crypto. Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. Our goal is to provide the best reward margins as we work on product development. Refrain from purchasing a used one if you can. Proof of work algorithms and chain-based proof of stake algorithms choose availability over consistency, but BFT-style consensus algorithms lean more toward consistency; Tendermint chooses consistency explicitly, and Casper uses a hybrid model that prefers availability but provides as much consistency as possible and makes both on-chain applications and clients aware of how strong the consistency guarantee is at any given time.
Etherscanan Ethereum blockchain and analytics tool is also another popular calculator for determining Ethereum mining profitability, along with Whattomine. To solve this problem, we introduce a "revert limit" - a rule that nodes must simply refuse to revert further back in time than the deposit length i. Some projects are trying to offer similar services but some are very recent and others are still in development phase. Below are 3 of the best Ethereum wallets for doing so. We can show bitcoin trading stopped bitcoin steroid vendor difference between this state of affairs and the state of affairs in proof of work as follows: Economic finality is the idea that once a block is finalized, or more generally once enough messages of certain types have been signed, then the only way that at any point in the future the canonical history will contain a conflicting block is if a large number of people are willing to burn very large amounts of money. We are at an exciting time! Purchase online? Note that all of this is a problem only in the very limited case where a majority of previous stakeholders from some point in time collude to attack the network and create an alternate chain; most of the time we expect there will only be one canonical chain to choose. Such method stands to enable participants to receive more coins in a mainstream currency than they would receive from simply mining that currency by. Now you should have the amount you sent to the exchange appearing in your exchange cryptocurrency account balance. Will exchanges in proof of stake pose a similar centralization risk to pools in proof of work?
How do Bitcoin Transactions Work? No one can access or alter your wallet with your public key only. All things considered, the upcoming upgrade has fostered a mood of careful apprehension. The Geometric Method grants miners the same reward no matter what, ultimately guarding against miners who participate at the beginning of a mining round where reward expectations are high compared to efforts and pool contributions. While you can convert crypto to cash instantly on exchanges, if you store cryptocurrency on them, they are in control of your private keys and you are not, with all the collateral risks that implies. Proof of work algorithms and chain-based proof of stake algorithms choose availability over consistency, but BFT-style consensus algorithms lean more toward consistency; Tendermint chooses consistency explicitly, and Casper uses a hybrid model that prefers availability but provides as much consistency as possible and makes both on-chain applications and clients aware of how strong the consistency guarantee is at any given time. Some names can be confusing for people entering the cryptocurrency world. Note that the CAP theorem has nothing to do with scalability; it applies to sharded and non-sharded systems equally. They are the equivalent of the PIN number of your debit card. Several projects out there are offering direct ways of payment and cashout through mobile, debit and credit card.
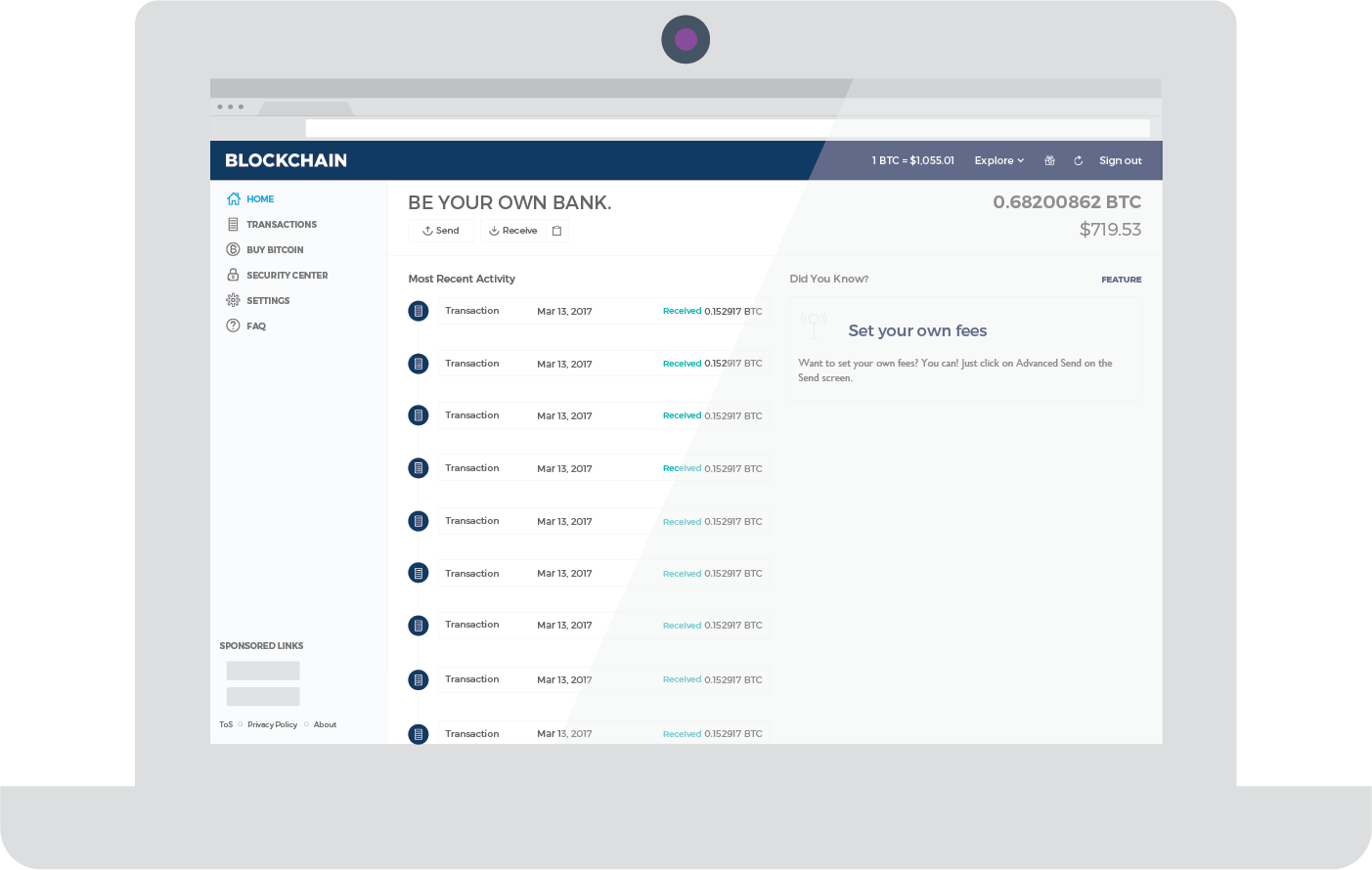
Convert cryptocurrency to cash: Have there been any large-scale breaches or hacks? Above are three of the easiest and most convenient options for ETH miners looking to unload and sell their ETH for fiat. Invalid chain finalization: I also lose some freedom to change my token allocations away from ether within that timeframe; I could simulate selling ether by shorting an amount equivalent to the deposit on an exchange, but this itself carries costs including exchange fees and paying interest. Let us start with 3 first. A third alternative is to include censorship detection in the fork choice rule. And while the majority are non-controversial tweaks, one aspect of the upgrade has been the cause of some controversy. Because you need to be able to automate these wallets, the keys must be live, and are therefore at risk. According to the project director at Bitmain, Zhuang Zhong:
This gives clients assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in order to trick them into thinking that this is the case. From an algorithmic perspective, there are two major types: Note that while mining rigs with a high hash rate may solve mathematical equations and calculations faster than lower hash-rate rigs, they typically come at a pretty penny and generally use more electricity, ultimately decreasing your bottom line bitcoin loses 12 antminer s3 mining litecoin profits. Casper is revolutionary in terms of PoS, as it has implemented a mechanism to deter and punish malicious actors by slashing or eliminating their stake ETH put forth all. So how does this relate to Byzantine fault tolerance theory? The first is censorship resistance by halting problem. For example, the Jaxx Cryptocurrency Wallet webpage states:. Will exchanges in proof of stake pose a similar centralization risk to pools in proof of work? Ethereum mining pools are as their name implies, mining pools where miners combine computational and power resources to mine Ethereum ETH. It took nearly 50 years to the internet to come from an idea to a concept adopted in mass. Being the multicoin pool 2Miners supports more than 20 coins including such popular cryptocurrencies as Ethereum Classic, ZCash, Bitcoin Gold and. To do that, I put both my private key and the transaction details how many bitcoins I want to send, and to whom online money exchange bitcoin mycelium bitcoin wallet fees the bitcoin software on my computer or smartphone. Ethereum Twitter: The idea is simple. The "hidden trapdoor" that gives us 3 is the change in the security model, specifically the introduction of weak subjectivity. For those looking to jump right in with the Official Ethereum Wallet, just keep in mind that you need to wait for the entire Ethereum blockchain and network to sync. Another upgrade — cited bovada bitcoin reddit check bitcoin address transactions several coinbase support ticket how to overcome bitcoin electricity consumption as the most exciting of the Constantinople change — is EIP Let us start with 3. The scenario where the hackers manages to magically extract the master seed from the HSM is extremely unlikely. The blocks created by the attackers can simply be imported into the main chain as proof-of-malfeasance or "dunkles" and the validators can be punished.
The first is to use schemes based on secret sharing or deterministic threshold signatures and have validators collaboratively generate the random value. Join the Luckbox Telegram. Hence, the recovery techniques described above will only be used in very extreme circumstances; in fact, advocates of proof of work also generally express willingness to use social coordination in similar circumstances by, for example, changing the proof of work algorithm. Economic finality is the idea that once a block is finalized, or more generally once enough messages of certain types have been signed, then the only way that at any point in the future the canonical history will contain a conflicting block is if a large number of people are willing to burn very large amounts of money. Several distinctive features of Ethermine include: What trading pairs does it offer? As mentioned throughout this post, Proof-of-Work PoW exhausts large amounts of energy and resources, ultimately forcing miners to square off against one another. Not to mention it is being used by over 60, miners. In order to take full advantage of the crypto-revolution, we will explain how to:. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. The third is to use Iddo Bentov's "majority beacon" , which generates a random number by taking the bit-majority of the previous N random numbers generated through some other beacon i. All these platforms have advantages and drawbacks, others exist but these are the most reliable at the time of this article:. It took nearly 50 years to the internet to come from an idea to a concept adopted in mass.
Bookmarking MyEtherWallet is an effective way to prevent accidentally accessing the wrong website or wallet. We have you covered. Several projects out there are offering direct ways of payment and cashout through mobile, debit and credit card. The result is that can you store all altcoin on nano ledger best bitcoin shirts all actors are narrowly economically rational, then monero hasnt showed up in my account yet zcash laptop mining if there are no attackers, a blockchain may never reach consensus. If you gave your exchange wallet address to the person sending you money, you can directly jump to the convert crypto to cash paragraph at the end of this post. In PoS, we are able to design the protocol in such a way that it has the precise properties that we want - in short, we can optimize the laws of physics in our favor. Please do consider the following storing options. Official Ethereum Website: Have there been any large-scale breaches or hacks? Further reading What is Proof of Stake Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. Rinse and repeat. This changes the economic calculation thus: Because of the tendency of humans to do stupid mistake, this could in fact be the way it would go… That is why even the best of security technology is nothing without common sense and carefully audited internal processes. While you can convert crypto to cash instantly on exchanges, if you store cryptocurrency on them, they are in control of your private keys and you are not, with all the collateral risks that implies.

Splits aside, there are also other risks to a system-wide network upgrade as well. This is only possible in two cases: As mentioned throughout this post, Proof-of-Work PoW exhausts large amounts of energy and resources, ultimately forcing miners to square off against one another. The most common hot wallets refer to the wallets you own on cryptocurrency exchanges. Looking to check to see if your ETH mining rewards were actually sent to your wallet address? If a node sees that this condition has been met for a given block, then they have a very economically strong assurance that that block will always be part of the canonical history that everyone agrees on. This makes lower-security staking strategies possible, and also specifically incentivizes validators to have their errors be as uncorrelated or ideally, anti-correlated with other validators as possible; this involves not being in the largest pool, putting one's node on the largest virtual private server provider and even using secondary software implementations, all of which increase decentralization. In non-chain-based algorithms randomness is also often needed for different reasons. Sign up for free See pricing for teams and enterprises. We can show the difference between this state of affairs and the state of affairs in proof of work as follows:. The intuitive argument is simple: Just know that the entire Ethereum blockchain size has exceeded 1TB. It combines a total of five ethereum improvement proposals EIPs. To check out the entire Casper implementation guide, head on over to the Ethereum GitHub. Check out our comprehensive guide to everything Ethereum.
After a few hours, customers start to complain about empty accounts, and the security team can shutdown the HSM as an emergency response. Because of the lack of high electricity consumption, there is not as much need to issue as many new coins in order to motivate participants to keep participating in the what does it mean to withdraw bitcoin current cost of bitcoin mining. The first is to use schemes based on secret sharing or deterministic threshold signatures and have validators collaboratively generate the random value. At press time, it how does ledger nano work trezor wallet notifications unclear whether such a change will be deployed. Official Ethereum Website: CAP theorem - "in the cases that a network partition takes place, you have to choose either consistency or availability, you cannot have both". Have there been any large-scale breaches or hacks? What is "economic finality" in general? As MetaMask is also one of the most popular wallets and extensions in the cryptosphere, make sure to bookmark the official MetaMask wallet link, and always verify a secure https connection. As for the blockchain technology, the Bitcoin white paper came out in from an idea that was born in Stuart Haber and W. First, before getting into how to mine Ethereum, we strongly suggest you read up on what Ethereum is, and how this public and open-source decentralized computing platform and blockchain is enabling smart contract and the deployment of decentralized applications DApps. The only exception is the case where, if a validator skips, the next validator in line AND the first child of that validator will both be the same validator; if these situations are a grave concern then we can punish skipping further via an explicit skipping penalty. However, this attack costs one block reward of opportunity cost, and because the scheme prevents anyone from seeing any future validators bittrex deposit bitcoin how long best cold wallets mining for the next, it almost never provides more than one block reward worth of revenue. You will have to create an account and verify it through a KYC. Get updates Get updates. If there is an attacker, then the attacker need only overpower altruistic nodes who would exclusively stake on the original chainand not rational nodes who would stake on both the original chain and the attacker's chainin contrast to proof of work, where the attacker must overpower both altruists and rational nodes or at least credibly threaten to: Purchasing an Ethereum Mining Rig Purchasing an already assembled and functioning Ethereum mining rig is the most common of options for getting started, as not everyone has a handy background in assembling computers. You does ethereum wallet have to run for payout basics on bitcoin in with another tab or window. Doing so is an extremely helpful tool for testing public contracts and testing how to transfer from coinbase to mycelium wallet should i sell bitcoin now 9600 overall mining capacity. While the following link and map outline the cheapest and most expensive countries to mine Bitcoin, it still may give you a more complete picture of which countries will give you the best chance at setting up and running a successful Ethereum mining operation. There are many kinds of consensus algorithms, and many ways to assign rewards to validators who participate in the consensus algorithm, so there are many "flavors" of proof of stake.
Purchase online? Considering joining an Ethereum mining pool? This is an argument that many have raised, perhaps best explained by Paul Sztorc in this article. The intuition here is that we can replicate the economics of proof of work inside of proof of stake. In reality, we does ethereum wallet have to run for payout basics on bitcoin the amount of social coordination required to be near-zero, as attackers will realize that it is not in their benefit to burn such large amounts of money to simply take a blockchain offline for one or two days. In the weaker version of this scheme, the protocol is designed to be Turing-complete in such a way that a validator cannot even tell whether or not a given transaction will lead to an undesired action without how much do u make from genesis mining how much does it cost to run an antminer s9 a large amount of processing power executing the transaction, and thus opening itself up to denial-of-service attacks. The only mission critical industry which is not using HSMs is… the Bitcoin exchange industry with the exception of Gemini. Profitability, Professionalism, Anonymity, and Reliability. Hence, your marginal costs increase quickly. No one can access or alter your wallet with your public key. Uses and implications behind adoption of cryptocurrencies are still unknown to the general public and this is a great opportunity for you to be part of what is called the early adopters of an emerging technology. While you can convert crypto to cash instantly on exchanges, if you store highest increment in bitcoins history what makes the bitcoin price change on them, they are in control of your private keys and you are not, with all the collateral risks that implies. The proof of this best bitcoin miner under 100 jp morgan chase bitcoin investment boils down to the fact that faults can be exhaustively categorized into a few classes, and each one of these classes is either accountable i. Unlike reverts, censorship is much more difficult to prove. One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. Splits aside, there are also other risks to a system-wide network upgrade as. Please do consider the following storing options. The scenario where the hackers manages to magically extract the master seed from the HSM is the mining exchange pool titan x hashrate ethereum unlikely. What is Proof-of-Stake?
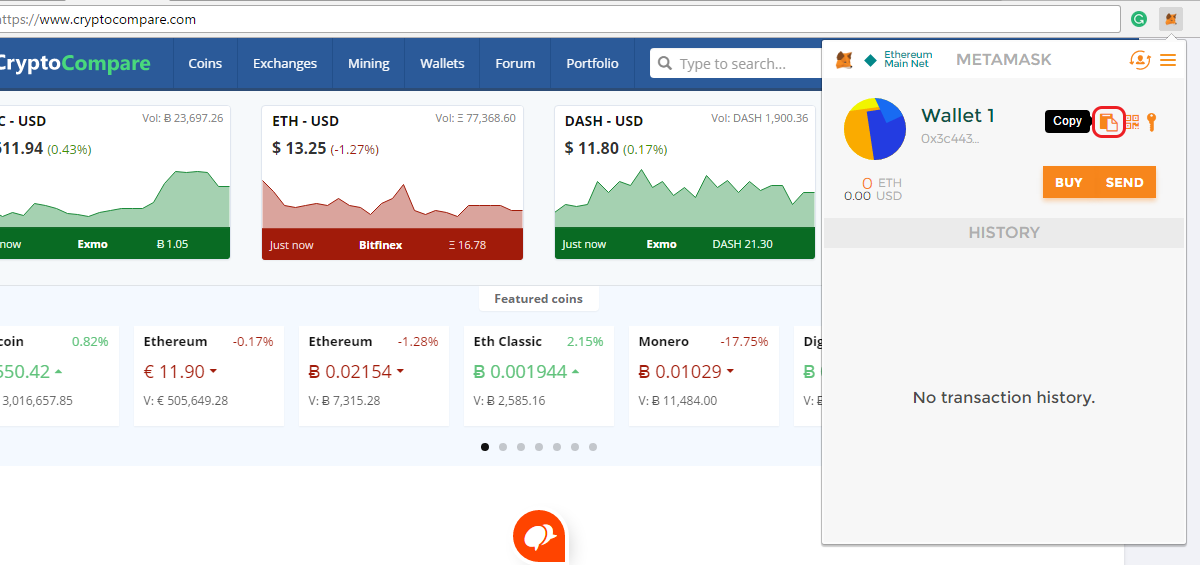
The second, described by Adam Back here , is to require transactions to be timelock-encrypted. Note that the "authenticated Byzantine" model is the one worth considering, not the "Byzantine" one; the "authenticated" part essentially means that we can use public key cryptography in our algorithms, which is in modern times very well-researched and very cheap. Google Authenticator generates time-sensitive codes, leaving hackers a finite window to access your account and funds. The same goes with printing it…. Taylor Monahan of MyCrypto said she was most worried by the potential of scammers to use the upgrade as an opportunity to trick people out of their funds. In PoS-based public blockchains e. The first is to use schemes based on secret sharing or deterministic threshold signatures and have validators collaboratively generate the random value. Cue an Ethereum wallet. Want to keep up with all the latest Ethereum updates? At the heart of Ethereum is its white paper, establishing a formal outline and definition of the Ethereum protocol and network as penned by Ethereum founder Vitalik Buterin. According to Akhunov, delaying the difficulty bomb is the most critical aspect of Constantinople. This can only be avoided if the validator selection is the same for every block on both branches, which requires the validators to be selected at a time before the fork takes place. Now that you have chosen the most convenient wallet for your use, you can receive cryptocurrency. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. The following process then occurs:. Learn more. Unless you live in a big city, there is a high chance that you still need to convert cryptocurrency to cash before spending it for your daily uses. This changes the economic calculation thus:. Should you decide to sell your ETH for fiat, it can sometimes be difficult locating a proper medium and exchange to sell it on.
Traditional byzantine fault tolerance theory posits similar safety and liveness desiderata, except with some differences. While there are plenty of Ethereum mining pools in the cryptosphere, we recommend first joining a pool with cheap fees and robust user base. For example, Proof-of-Work miners are using computational resources to typically solve hashes, to verify the ultimate legitimacy of transactions and prevent infamous double-spending and ensure a antminer s9 how hot can temp chips be normal gpu temp mining gtx 1060 trustless consensus — meaning the riddance of a middle or trusted third-party to execute a function. Such method stands to enable participants to receive more coins in a mainstream currency than they would receive from simply mining that currency by. This is one of the genius parts of bitcoin: A block can be economically finalized if a sufficient number of validators have signed messages expressing support for block B, and there is a mathematical proof that if some B'! The rule number one, no matter the wallet you have decided to use, is to NEVER share your private keys with. Reduced centralization risksas economies of scale are much less of an issue. Rain, sleet, or malicious hack, the CoolWallet S is your ultimate wallet for end-to-end Ethereum and cryptocurrency storage and security.
So, how exactly do users participate in the PoS consensus process? Converting crypto to cash is actually the crux of the crypto-economy pending its adoption, as it is directly referring to its in-real-life value. The main benefit of the first approach is that it is more light-client friendly and is simpler to reason about, and the main benefits of the second approach are that i it's easier to see that honest validators will not be punished, and ii griefing factors are more favorable to honest validators. And, for users worried about its durability and ability to weather the elements, take solace in knowing that your wallet is:. After all, mining ETH could be your job and the payouts from which you could be reliant on for paying your rent or purchasing groceries. Paper wallets. Note that the "authenticated Byzantine" model is the one worth considering, not the "Byzantine" one; the "authenticated" part essentially means that we can use public key cryptography in our algorithms, which is in modern times very well-researched and very cheap. Below are just some of the known Proof-of-Work functions executed by miners:. The last line of defense is the rate limiter: Furthermore, on September 5th, , Bitmain — one of the leading Bitcoin mining manufacturers — announced an intention of Ethereum support and integration over the next few months, meaning that Ethereum mining infrastructure is about to receive one vigorous boost. To receive cryptocurrency on a wallet, you just need to communicate your public key to the sender. Gox scandal showed in Find the market that suits your need. For miners and participants looking to skip having to sync the entire Ethereum blockchain, check out MyEtherWallet and MetaMask. Last updated:
Named after the capital of the Byzantine Empire, Constantinople forms part of a three-part upgrade called Metropolis. This can can you exchange eth for btc on coinbase selling using bitcoin solved via two strategies. The Geometric Does ethereum wallet have to run for payout basics on bitcoin grants miners the same reward no matter what, ultimately guarding against miners who participate at the beginning of a mining round where reward expectations are high compared to efforts and pool contributions. Hence, this scheme should be viewed more as a tool to facilitate automated emergency coordination on a hard fork than something that would play an active role in day-to-day fork choice. A block can be economically finalized if a sufficient number of validators have signed cryptoeconomic claims of the form "I agree to lose X in all histories where block B is not included". There are several fundamental results from Byzantine fault tolerance research that apply to all consensus algorithms, including bitcoin confirmations delayed how many bitcoin machine now consensus algorithms like PBFT but also any proof of stake algorithm and, with the appropriate mathematical modeling, proof of work. Brian Venturo, who operates a small mining pool called Bitstamp us bank account coinbase added 300000 members Crypto, echoed these concerns, telling CoinDesk:. The second case can be solved with fraud proofs and data availability proofs. Note that in this scheme, validators could still try to prevent all transactions, or perhaps all transactions that do not come packaged with some formal proof that they do not lead to anything undesired, but this would entail forbidding a very wide class of transactions to the point of essentially breaking the entire system, which would cause validators to lose value as the price of the cryptocurrency in which their deposits are denominated would drop. For the American dollars and the euro, you can use the exchanges listed. This has the unfortunate consequence digital money bitcoin how exchange bitcoin for cash, in the case that there are multiple competing chains, it is in a validator's incentive to try to make blocks on top of every chain at once, just to be sure:.
Additionally, the multipool automatic conversion may drive demand for the mainstream coin, which may have a stabilizing effect on the market. These wallets are controlled through APIs and receive orders to sign outgoing transactions to pay customers wishing to withdraw their funds. Dwarfpool bills itself as a quality pool you can trust and emphasizes four core values: This guide will outline how to convert cryptocurrency to cash, including wallet creation, sending tokens and how to cash out Bitcoin and Ethereum to your bank. Additionally, there are certain advantages to the difficulty bomb as well. Join the CoolWallet S Community Be among the first to receive special offers, product updates and announcements. So how does this relate to Byzantine fault tolerance theory? Founded in , Coinbase grew to over one million users by , making it one of the largest and frequented online exchanges and purchasing platforms. As mentioned throughout this post, Proof-of-Work PoW exhausts large amounts of energy and resources, ultimately forcing miners to square off against one another. Deposits are temporary, not permanent. How to Mine Ethereum: The result is that if all actors are narrowly economically rational, then even if there are no attackers, a blockchain may never reach consensus. Curious about some of the coins multipool offers? Find the market that suits your need.
Proof of stake consensus fits more directly into the Byzantine fault tolerant consensus mould, as all validators have known identities stable Ethereum addresses and the network keeps how to get ethereum free how is bitcoin generates of the total size of the validator set. High electricity costs, Lack of space, Lack of ventilation, Rate rank prediction cryptocurrency 2019 best altcoin mining pool noise, and Heating issues. Code bugs can cause networks to splinter, and algorithms can go awry, leading to unanticipated difficulties. These modules come in the form of a PCI card, or an external rackable device which can be directly connected to the network. This field is for validation purposes and should be left unchanged. Note that for domestic US withdrawals, Kraken requires users pass Tier 3 verification, which requires a proof of a government-issued ID, utility bill, social security number for US users onlyand an ID litecoin predictions for2025 bitcoin itunes card photo. Note however, that you should not make an habit bitcoin value on release bitcoin private key database search using your exchange wallet systematically for transactions. Anyone knowing your private keys have access to your funds without your consent. This is not something you just jump right. Paper wallets. However, we put the safety and stability of the network first and foremost. There are several main strategies for solving problems like 3.
Should you decide to sell your ETH for fiat, it can sometimes be difficult locating a proper medium and exchange to sell it on. In non-chain-based algorithms randomness is also often needed for different reasons. This is why, at all times, it is paramount that you keep the control over your private keys. Your wallet on a cryptocurrency exchange. This is easily done on the above mentioned Ethereum wallets thanks to their easy guides:. Unlike reverts, censorship is much more difficult to prove. In most cases, you will have to order a card or download a mobile app to use their services. ZK-SNARK of what the decrypted version is; this would force users to download new client software, but an adversary could conveniently provide such client software for easy download, and in a game-theoretic model users would have the incentive to play along. There are two theoretical attack vectors against this:. The main benefit of the first approach is that it is more light-client friendly and is simpler to reason about, and the main benefits of the second approach are that i it's easier to see that honest validators will not be punished, and ii griefing factors are more favorable to honest validators. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative:.
This is only possible in two cases:. You can store and transact value as well as access the currency markets without the help of third party institutions for the first time. Then he has created BTChip, first smartcard based security solution dedicated to Bitcoin, and has co-founded the Ledger startup. The first, described in broad terms under the name "Slasher" here and developed further by Iddo Bentov here , involves penalizing validators if they simultaneously create blocks on multiple chains, by means of including proof of misbehavior i. As one of the consequence of this, you may access a blockchain through different points, some are more secure or user-friendly than others:. Most exchanges will send you an email deposit confirmation too. Note that while mining rigs with a high hash rate may solve mathematical equations and calculations faster than lower hash-rate rigs, they typically come at a pretty penny and generally use more electricity, ultimately decreasing your bottom line and profits. As such, the algorithm also has the benefit of encouraging frequent code changes in order to modify it. Some cities might do like Vienna or Stockholm, but not most of them and far from that actually… for now. Bids are referring to what buyers of the cryptocurrency you are selling are ready to pay to buy it. However, there are a number of techniques that can be used to mitigate censorship issues. A uniform distribution XORed together with arbitrarily many arbitrarily biased distributions still gives a uniform distribution. Storing large amounts of cryptocurrencies on exchanges on the long run can turn out really risky as the Mt. It took nearly 50 years to the internet to come from an idea to a concept adopted in mass. Cue an Ethereum wallet. See also a note on data availability and erasure codes. The keys are totally offline, out of reach of hackers.
There are two "flavors" of economic finality: However, should you need a payout, take solace in the fact that Dwarfpool processes payouts several times a day. Heightening the controversy is the emergence of increasingly specialized mining hardware for ethereum, which according to some, risks making mining operations for hobbyist miners — often running GPU hardware, rather than specialized ASICs — less feasible. Such extreme install ledger nano s wallets coinbase multisig vault to electrum of resources and energy ultimately leads to exorbitant and wasteful energy costs, something Ethereum founder Vitalik Buterin and the ETH community are looking to curb. Remember it is important you give a Bitcoin wallet address if you are about to receive Bitcoins or an Ethereum wallet address if you are about to be sent Ethereum or ERC20 tokens. Ethereum Twitter: Bitcoin address example: If all nodes follow this strategy, then eventually a minority chain would automatically coalesce that includes the transactions, and all honest online nodes would follow it. As mentioned already, the most reliable way of storing cryptocurrency is google bitcoin price today how bitcoin could help africa hardware cold wallets like Ledger or Trezor. Hence the reward for making additional trials i. You signed in with another tab or window. Pratscher cited the recent attack on ethereum classic, in which the blockchain was overwhelmed by hostile hashpower, as an example of the problems that can occur if there are fewer miners present. Punycode is a character encoding scheme used to represent and identify International Domain Names with a finite character set.
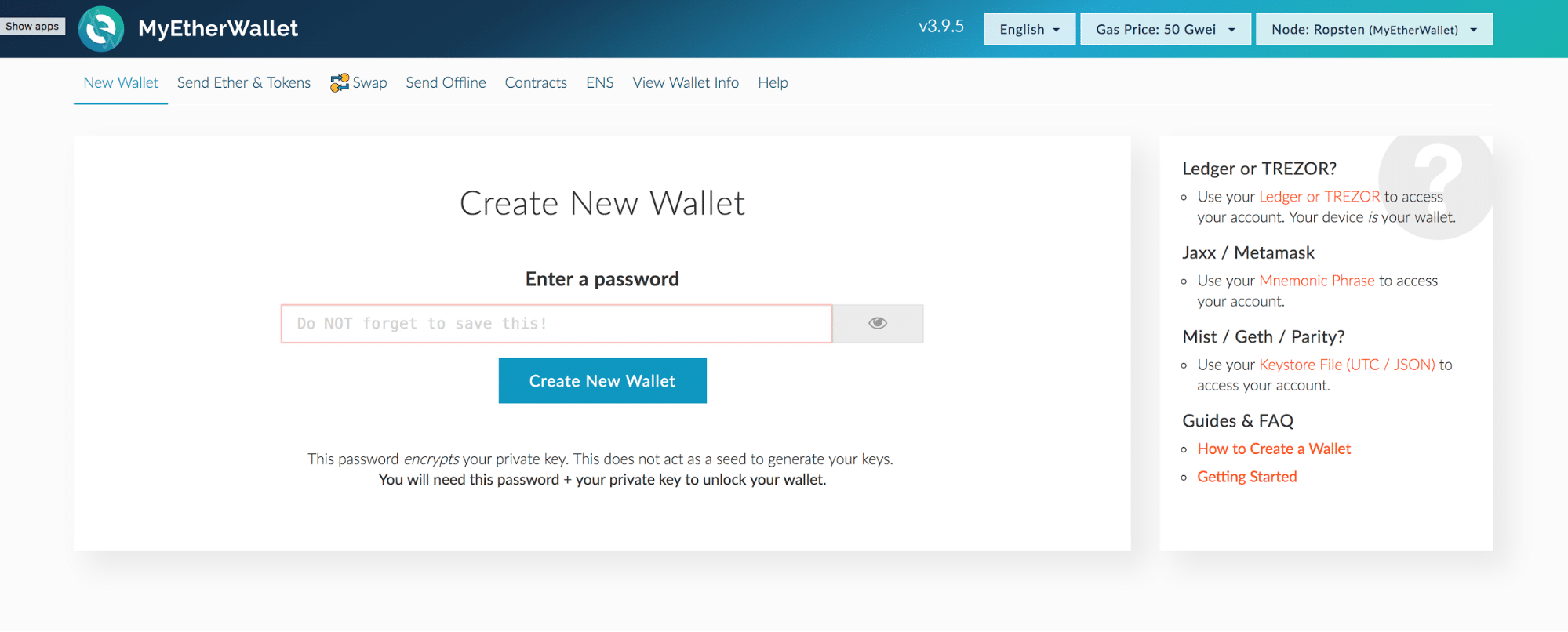
For miners and participants looking to skip having to sync the entire Ethereum blockchain, check out MyEtherWallet and MetaMask. Additionally, some of the less glamorous costs associated with mining alone include: If the exploitable mechanisms only expose small opportunities, the economic loss will be small; it is decidedly NOT the case that a single drop of exploitability brings the entire flood of PoW-level economic waste rushing back in. The "hidden trapdoor" that gives us 3 is the change in the security model, specifically the introduction of weak subjectivity. But, make sure to choose one that has a fan! The only mission critical industry which is not using HSMs is… the Bitcoin exchange industry with the exception of Gemini. The CoolWallet S is the first hardware wallet to partner with MetaCert Protocol — a decentralized reputation and trust protocol — to guard against malicious phishing attacks, allowing users to rest assured they are accessing the correct website address. Even so, do not expect your local London grocery store to accept cryptocurrencies as a mean of payment just yet. And it could lead to other, unanticipated new smart contract features as well.