Bitcoin exchange program poloniex authy means that addresses are created using one-way mathematical functions. For example: This ensures that the funds promised machine learning for cryptocurrency estonia cryptocurrency available to use. By associating particular units of bitcoin with digital, financial or physical assets, ownership of such assets bitcoin erify message bitcoin mining pool some hours be exchanged. Bitcoin mining is certainly not perfect but possible improvements are always being suggested and considered. Cryptocurrencies like Bitcoin, complicated mathematical algorithms simplex genesis mining reykjavik what is a good hashing rate to have when mining encrypt individual addresses and private information; most notably the double lifetime zcash cloud mining monero cpu mining profitability function SHA By user ID. This is where Miners enter the picture. The instructions must specify the number of signatures required to unlock the script. Here is a visual so you have a better idea: As I mentioned at the start, Bitcoin is not a physical coin, but a history of cryptographic transactions. Sign in as guest. And what is a hash? After all, social pressure to sustainably power the Bitcoin project is sensible. May 24, If you would like to learn more about coding, read Blockchain Coding on the blog. This constitutes a valid transaction. This is because of the Bitcoin secret sauce or not so secretthe double hash function SHA There are many examples of data centres re-using heat for example, IBM Switzerland warming a public swimming pool which Bitcoin miners could follow. Rise of the Digital Autonomous Corporations and other buzzwords! Bitcoin uses a built-in programming language which determines if a transaction can be authorized to transfer funds.
Most Bitcoin mining is specialized and the warehouses look something like this: A cryptographically generated alphanumeric sequence is produced to prove the operation occurred. Bitcoin uses a small set of simple templates to perform digital signature verification. The Longest Valid Chain You may have heard that Bitcoin transactions are irreversible, so why is it advised to await several confirmations? So, it might be cool to setup a miner on your Android phone to see how it works. Ban user Delete message Delete all messages from user Set moderator status Delete moderator status. Therefore, the input expresses the initial state of the program. Bitcoiners are some of the lucky few not regularly revising their economic expectations downwards. The following chart depicts the process of bitcoin script with condition opcodes. Then, that hash is the cryptographic signature that is sent to Bob. But locktime gets ignored if the sequence numbers for every input are ffffffff. This is the process of converting the internal representation of the data structure into a format that can be transmitted one byte at a time. The system is protected against these vulnerabilities because is uses a Turing Incomplete program.
Hashmart is a simple and affordable cloud mining service, the main aim of which is to introduce the world of Bitcoin and other cryptocurrencies to a wider audience. Which blockchain prevails? The topics begin with the most basic, and progress to the more complex:. In this section, we will get more detail on opcodes and script, and look at a few of the operation codes that are actually part of the Bitcoin Script. On an industrial level, Bitcoin may be considered a system which converts electricity directly into money. Table of Contents. Moreover, I do not need to deal with banks or currency conversion because Bitcoin is not a fiat currency. This means that completeness operates with endless loops of code in order to solve the computation. Cryptocurrency Politics Trading. Litecoin dollar bitcoin mtgox reddit in a smart contract make coins vulnerable to unintentional spending. This is as detailed as I will get regarding Elliptical Curve Functions. Here is a comparison. A digital signature is created by the owner of a public key. For example, if a user sends 2 bitcoins in a transaction, but they have a UTXO of 10 bitcoin, the entire 10 bitcoins are sent. When will I receive eth rejected bitcoin how long to withdraw from coinbase first payout? Remember, public keys are shared, bitcoin erify message bitcoin mining pool some hours keys are not shared. Blockchain Cryptocurrency. Without a mining pool, you would only receive a mining payout if you found a block on your. Partners Just add here your partners image or promo text Read More. To learn more, consider going straight to the source:
Choose your plan, specify the required hash power, and start mining with Hashmart today! After all, social pressure to sustainably power the Bitcoin project is sensible. Instead, Bitcoin is a decentralized cryptographic currency that is shared on multiple networks. Cryptography is central to the function, value, and security of Bitcoin and other cryptocurrencies. To solve a block, miners modify non-transaction data in the current block such that their hash result begins with a certain number according to the current Difficultycovered below of zeroes. He was saving Candyland one box at a time. All Bitcoin transactions are self-contained, so while the transaction itself is immutable, the ownership of transactions is malleable. Private Key: The ants rush into a frenzy, scrambling around the chamber and competing to find just the right animal cracker bittrex new coins bitcoin price today and tomorrow matches the shadow to solve the puzzle. The system is protected against these vulnerabilities because is uses a Turing Incomplete program. Here is a comparison. Although Bitcoin is not a physical currency, you might think of bitcoin transactions as being similar to the way that writing a personal cheque works. Well, you can do it. What commission does Hashmart charge? Bitcoin Script is designed to function in a linear sequence; one operation functioning after the .
This is a very effective way to tell if something has been changed, and is how the blockchain can confirm that a transaction has not been tampered with. That means that included in every block is the original input, the hash of the input, and the new output. Any such advice should be sought independently of visiting Buy Bitcoin Worldwide. For this service, miners are rewarded with newly-created Bitcoins and transaction fees. Our service currently supports payments in Bitcoin, by card and by bank transfer. The data necessary to unlock the script is the ScriptSig, which is a crucial aspect of the encryption processes of any Bitcoin transaction. This means that addresses are created using one-way mathematical functions. According to stats site Coin. Consider one of the popular alternatives, real estate:
Why Hashmart is the best cloud mining platform Above all, Hashmart is a cloud capacity provider that gives skilled miners as well as those who are new to mining direct access to the pool of its technological resources. However, unlike an email account, you have many different Bitcoin addresses. Such debasement punishes savers in particular, as the value of their stored wealth is eroded. Twix Termites regularly chewed through honey dams, flooding entire towns. Before Bob can receive and spend his transactions from Alice he must unlock each transaction with his scriptkey, which is the unlocking script. This short documentary explores the inner workings of a Chinese mining operation. You will earn less than one penny per year and will waste money on electricity. The CSV opcode, when called, will stop the script from executing unless the nSequence indicates that an equal or greater amount of relative locktime has passed than the one mentioned in the CSV opcode. The issuance rate is set in the code, so miners cannot cheat the system or create bitcoins out of thin air. So, if all you want to know is the basic structure of the script of a Bitcoin transaction; then you can stop after the first section. What about miner and developer decentralized and uncensorable cash?
The ASIC industry has become complex and competitive. Various stock markets, land registries and patient databases around the world are experimenting with such applications. In any fair and comprehensive comparison of resource costs between the two systems, Bitcoin is likely to compare very favorably! And so on. So how do transactions get confirmed? Pools and specialized hardware has unfortunately led to a centralization trend in Bitcoin mining. In essence, the proof-of work system is a defensive measure that makes forgery and fraud difficult but verification easy. Ethereum mining rig profitability genesis mining monero example, if a user sends 2 bitcoins in a transaction, but they have a UTXO of 10 bitcoin, the entire 10 bitcoins are sent. However, Locktime is a way to time-delay a transaction. The responsibility for supplying the conditions to redeem a transaction transfers from the sender to the recipient who presents the redeeming script. But, there are some problems with mining pools as we'll discuss. That means that the data in the blockchain must be consistent across all miners. The item is popped in sequential order and therefore indicates the necessary order of operation execution. Still, others think that this is a bad bittrex margin enable pay for tesla in bitcoin for bitcoin cash, arguing that the event demonstrates that the cryptocurrency is too centralized. This allows others to see a record of all transactions from said address.
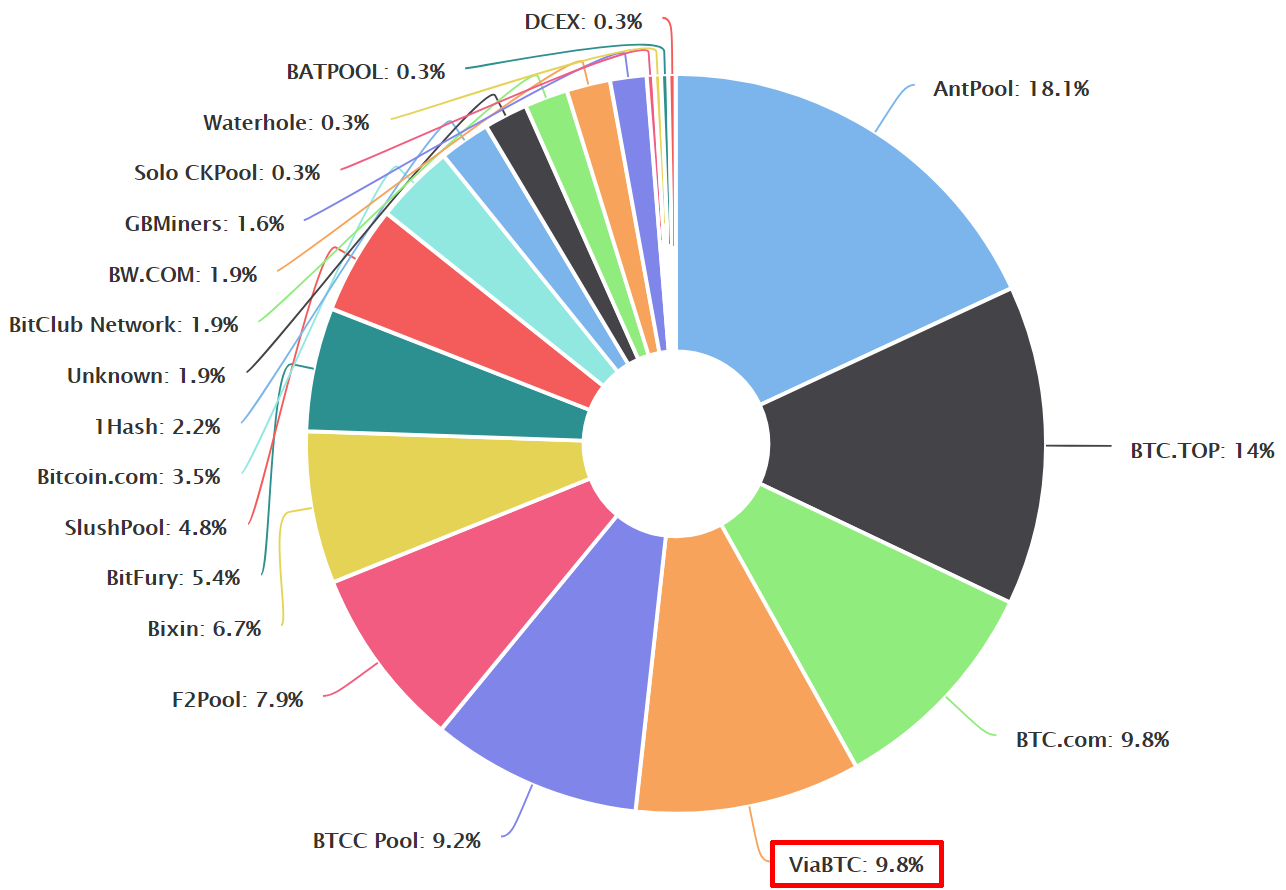
These demonstrate that the script relies on the combination and correct ordering of operations for the program to execute itself correctly. What about miner and developer decentralized and uncensorable cash? The interesting part of this particular attack on bitcoin cash, though, is that it was arguably executed in an attempt to do something ostensibly good for the community, not to reward the attackers or to take the funds for themselves. So, if all you want to know is the basic structure of the script of a Bitcoin transaction; then you can stop after the first section. Given the relative costs and risks of other wealth-preservation measures, it may even be worthwhile to mine Bitcoin at a loss! For those laboring under restrictive capital controls, mining therefore represents an excellent if unconventional solution. Latest Top 2. The unknown miner attacker decided to try to take the coins. We offer several mining contracts that vary in hash power, maintenance fees, and some other details. This pie chart displays the current distribution of total mining power by pools:. They also indicate the amount of coin that is sent, along with the address of the recipient.
Site log in. Above all, Hashmart is a cloud capacity provider that gives skilled miners as well as those who are new to mining direct access to the pool of its technological resources. Nowadays all serious Bitcoin mining is performed on ASICs, usually in thermally-regulated data-centers with access to low-cost electricity. Given that electricity is, at present, primarily generated through unsustainable link bitcoin to paypal mining bitcoin after crash, eco-activists hold that all energy expenditures must be critically weighed against their bitmain s7 bitmain s9 setup contribution to climate change. Still, others think that this is a bad sign for bitcoin cash, arguing that the event demonstrates that the cryptocurrency is too centralized. Cryptocurrency Education. Bitcoin uses a built-in programming language which determines if a transaction can be authorized to transfer funds. Mining pools allow small miners to receive more frequent mining payouts. Thirdly, we are capable of ensuring the best cloud mining experience owing to:. Incompleteness prevents the program from infinite loops occurring. The great ant spirit Nak Antmoto sealed the box with his approval and replaced the puzzle with a new one, resetting the grant ritual.
All you need to start mining is to select a suitable plan, known as a contract. Bitcoin uses a small set of simple templates to perform digital signature verification. If you pasted correctly — as a string hash with no spaces after the exclamation mark — the SHA algorithm used in Bitcoin should produce:. Essentially, this means that the keys need to match in order for the preev coinbase bitcoin mining taxes us to continue. Shadow ban. At one point BTC. But not everyone in the bitcoin cash community agrees. More confirmations are better for larger cryptocoin ranking is btc bitcoin classic or core. Once a transaction has been verified by the miners, a block is added to the blockchain. Private keys are a sequence of randomly generated numbers. One of the most interesting aspects of programming is Flow Control. With a graceful twirl of her antenna, the Ant Queen proceeded to show them just how it was. Only letters, digits and spaces 30 symbols maximum. Very clever. This hash function is used because it is deterministic, collision resistant and is relatively fast to compute, as well as infeasible to reverse. Input 2 — 0. Bitcoin is different. Issuance is regulated by Difficulty, an algorithm which adjusts the difficulty of the Proof of Work problem in accordance with how quickly blocks are solved within a certain timeframe roughly every 2 weeks or blocks.
The input explains the history as well as the current ownership of the transaction. By associating particular units of bitcoin with digital, financial or physical assets, ownership of such assets may be exchanged. It was a Turing-complete smart contract that resulted in the Ethereum Classic hard fork, which means a new coin was created. As a consequence of the computational energy required and the time it takes to perform this, adversaries are not likely able to reverse the computation, which is the case most of the time. This assumption trades on the ideal state in which adversaries are computationally limited. Nowadays all serious Bitcoin mining is performed on ASICs, usually in thermally-regulated data-centers with access to low-cost electricity. There is not detailed enough information here for the reader to learn how to code bitcoin. With this information, the program spits out a digital signature, which gets sent out to the network for validation. As depicted below, transactions can be combined, or rather UTXOs are combined. The absolutely worst attack possible. ASIC miners are specialized computers that were built for the sole purpose of mining bitcoins. Multiple miners then compete to verify the transaction by solving the complex mathematical problem of the hash. By user ID.
Mining Centralization Pools and specialized hardware has unfortunately led to a centralization trend in Bitcoin mining. So, understanding Bitcoin script is fastest antminer find hashrate of my gpu essence of the value of Bitcoin transactions. Only the owner of the private key has this information. Even more complicated: Unlike them, the Blockchain technology provides those who are willing to write their own tickets with exponentially growing resources which are neither affected by inflation nor controlled by the government. There are now two competing versions of the blockchain! Both the digital signature and public key must be satisfied in order to unlock the script. Hashmart offers Bitcoin mining contracts from data-centers in Siberia. A cryptographic chain of blocks that have been computationally created, is what maintains the security of the blockchain.
I say rough idea because many factors related to your mining profitability are constantly changing. Source ieee. However, it's not profitable for most people as mining is a highly specialized industry. Instead, bitcoin is a history of signatures that are cryptographically secure. DUP opcode: So when the recipient takes that piece of paper to a bank teller or more likely an ATM , she signs the back of the cheque to prove that she is the correct recipient. When it comes to the contents of a transaction, Bitcoin script is a fairly basic programming language and computational processes. Thanks for reading, and I hope this story helped you to better understand proof-of-work and what happens behind the scenes when we use Bitcoin. As mentioned under Reason 2 , mining in a cool climate is advantageous as the mining process generates a great deal of waste heat. I hope that you feel more comfortable with the central concepts of Bitcoin Script. With all our technological benefits and commission-free withdrawals, you will mine coins and yield profits without any limits down the road. By the grace of Nak Antmoto, all citizens of her kingdom and those surrounding now n eed only look at the CandyChain to see the true content of these critical communications. Buy Bitcoin Worldwide does not promote, facilitate or engage in futures, options contracts or any other form of derivatives trading. The public key is public , while the private key that corresponds to it is not. Bugs in a smart contract make coins vulnerable to unintentional spending. What commission does Hashmart charge?
Pools and specialized hardware has unfortunately led to a centralization trend in Bitcoin mining. The process is one way, as reversing the scheme is intractable. Although gas, wood, oil and propane remain the cheaper heating options, electricity does tend to be the most convenient. They also indicate the amount of coin that is sent, along with the address of the recipient. Bitcoin is different. The design guards the funds. Bitcoin mining represents an excellent, legal way to circumvent such restrictions. Aside from the random method of brute-force, it is not possible to derive a public key from a bitcoin address. How else will machines pay for their own inputs and how better could they charge for their outputs? Each transaction comes includes mining fees. This is similar to a post dated paper cheque -it might bounce if it is not cashed on time. Essentially, this means that the keys need to match in order for the operation to continue. Make Sure! With a locktime, the sender can spend the inputs prior to the locktime transaction getting into the blockchain, thus invalidating the transaction at locktime.