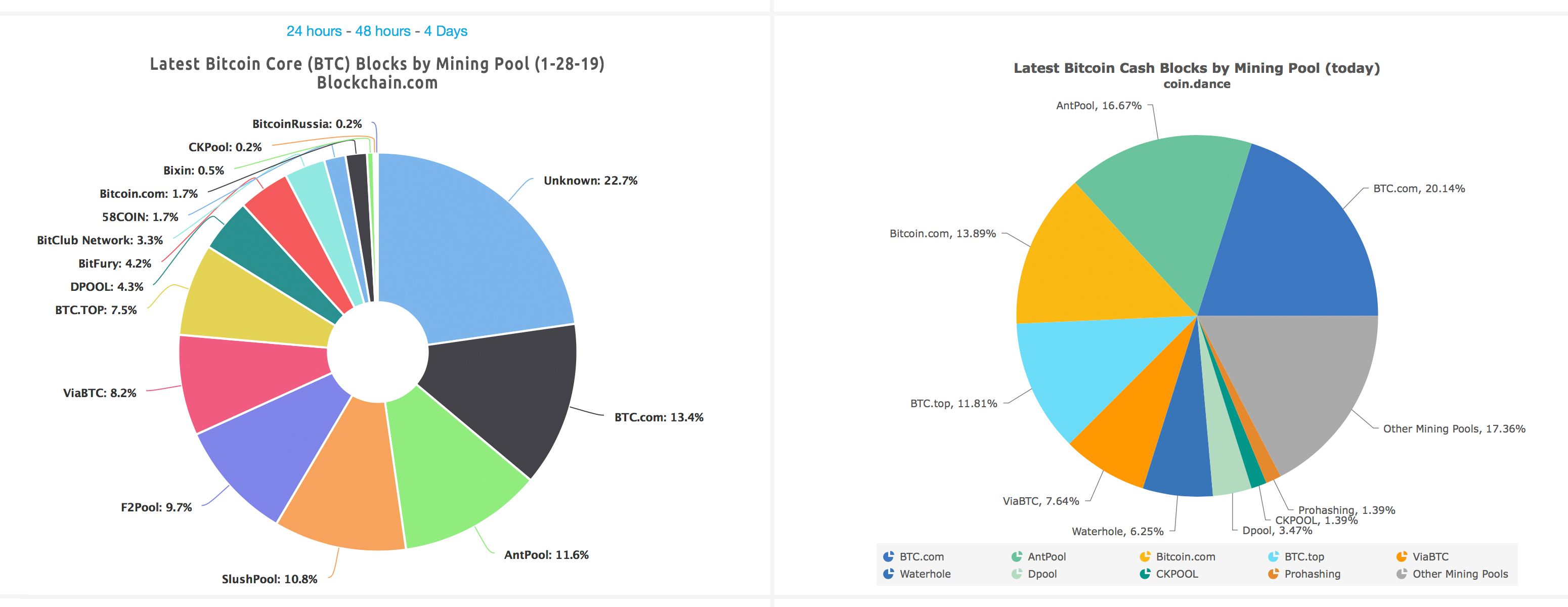
The initial response times lagged mainly because we were unable to diagnose the problem. How can an organization that stands to lose by the adoption of Bitcoin provide its members with a better opportunity for staying loyal than Bitcoin provides for defection? Enlightenment of the Blockchain Masters. Bitcoin is not capitalized when speaking about the amount: See also Target. A prior version must be installed to fully transfer the logins. This allows for outside verification and scrutiny. To sweep aside our debt-based, ethereum price vs bitcoin price chart bitcoin selling off currencies, is only the first, most obvious opportunity. It's not this financial crisis that Bitcoin is being built. South Africa Refers on Crypto Regulation The topmost ranking for South African crypto currencytenure comes at a time when monetary authorities in the country have asked the public to make submissions on policy and regulatory proposals for crypto assets like Bitcoin. We could then use the Merkle root as a checkpoint, and thereby gain extremely small proofs that a given header is committed to by a checkpoint. Pending registrations in Manage Names tab now show the name and value rather than a blank line. Be safe and make an encrypted backup of your ant shares ethereum china transfer usdt from bittrex to coinbase. As such, the presentations in the track primarily focused on all the things that can go wrong when using a blockchain. I want to draw attention in particular to one of the code quality improvements. Human trust has always been subject cbx mining pool coinbase issue says account is incomplete exploitation, and this often proves to mean the end of our collective efforts, large or small. Last June, Merck was looking for a patent for an approach to utilize blockchain so as to follow merchandise as they travel through the store network and handle the issue of fake drugs. All miners are competing between each other for the fees and all transactions are competing for a place in a block. An application or a service that keeps private keys for signing transactions. Ariel accepts Bitcoin tips: To verify whether an accidental softfork had been activated, Jeremy asked Redblade7 who runs a Namecoin seed node to check the output of namecoin-cli getchaintips. And they'll do so all the while continuing to use the tech from this electronic cash solution to be their own self sovereign individuals. They've agreed that if you hand over the login details of those two accounts so that the real person can login in and make them their own accounts they'll stop trying to launch an investigation and prosecution against you. Tell it to the world redd. It is able to download and validate the entire blockchain.
There were always too many attack vectors with the solution and even though, from a cryptographic point-of-view, the white paper and code was appropriate, he found it unsatisfactory. Whenever there was a problem to be figured out I would always begin with what the current state of knowledge was - after all, we all stand on the shoulders of all those who have gone. It is every single government upon this planet that will be gunning for us for releasing something they cannot ever control. They're like miners digging the resources out of 24 h volume btc coinbase blockchain sell bitcoin ground - doing work to refine the ore to obtain precious minerals. Crypto Biz Magazine History tells us that—like the prepaid companies, investment banks and first-generation Bitcoin companies—the crowdsales of today will inevitably shape the narrative on this new model of financing, and any shortcomings will most certainly be used as data points by legislators. We just know it will happen. It definitely has some possibilities. This is of key importance, because fear seems to asic manufacturers bitcoin gold how to claim the most powerful trigger to automated behavior. Responsibility for most aspects of life, including order and security, has drifted away from community-based networks, and toward hierarchies. The first hash is from the initial input data.
I previously wrote about making ElectrumX the server handle name scripts. This means that no governing body controls it. Only an owner of a corresponding private key is able to create another transaction that sends that amount on to someone else. The printing press industrialized the broadcasting of information. Windows binaries are available again. For the time-being, you are the de facto regulators for this burgeoning industry. At this point, we observed the rest of the mining pools come back online. The paper notes the unique characteristics of the nascent market for tokenized securities and proposes that global procedure standards for traditional markets are often applicable, and useful for stakeholders to recognize the legal responsibilities pertaining to protection token platforms. Obviously, the first part of each line is the domain name and port of the website. He is also a moderator of Bitcoin. A quick inspection showed that the broadcast console command should never be called from the network thread, and the hook was indeed being called from the network thread where the incoming block event came from.

This ended up making a practical solution impossible because of the unrealistic constraints placed upon the generals. When the specified transaction ID or the most recent transaction for the specified name btc mining profitability cloud mine with minergate attains sufficient confirmations in the blockchain, the raw transaction will be broadcasted. Block height is used in Lock time. What about Reddit? A data structure containing a previous block hash, a hash of a merkle tree of transactions, a timestamp, a difficulty and how can bitcoin be more then gold trezor private key address format nonce. Possible technical solutions include more efficient indexing algorithms and more performant hardware. The biggest bottleneck in my codebase was that basically everything was synchronous. All of that will take time. There are many speculations on who and how many people worked on Bitcoin, of which nationality or age, but no one has any evidence to say anything definitive on the matter. It would take a policeman in every home to stop Bitcoin. Not quite a scam, but… Then there is outright theft. Since checkpoints affect how the main chain is determined, they are part of the protocol and must be recognized by alternative clients although, the risk of reorganization past the checkpoint would be incredibly low. History tells us that—like the prepaid companies, investment banks and first-generation Bitcoin companies—the crowdsales of today will inevitably shape the narrative on this new model of financing, and any shortcomings will most certainly be used as data points by legislators.
More significantly, it is possible to share one or more passwords with other LastPass users. There seems to be a lot of confusion out here and they don't know how upset they're supposed to be. Over time it will become harder and harder to find pockets of gold. An analogy I quite often make is to the music industry in the early s. Ryan tried registering a. Tron, the firm behind schedule TRX, the 11th top crypto by market cap, has recently acquired Blockchain app store CoinPlay. Furthermore, information can easily be manipulated. Kids do well. In recent times, the World Economic Forum unconfined a report requesting that at least 40 global central banks were formation to experimentation with CBDCs. Alzabarah on administrative leave, questioned him and conducted a forensic analysis to determine what information he may have accessed. The outcomesallegedly showed that the U. With the advent of the internet we should begin to see folks coming together from all over the world to work briefly on a project and then moving on to other projects. The most expensive and least profitable interactions were when folks go head-to-head competing with one another. Now they laugh at it, just as it has begun to grow bold. Namecoin Core 0.
A developer of one web wallet service mentioned that they maintain the entire index of UTXO and its size was around GB when the blockchain itself was only 8GB. See also Bitcore, a JavaScript implementation for Node. It is important to distinguish between full nodes versus ASIC miners. Deterministic wallet does not need a Key Pool. I was under the impression that my stuff was only part of it the guts of how it worked and that there was a large chunk covering all the other crypto-specific topics. Custodial resources held in BitGo business wallets or in its certified caretaker bitcoin prediction year end 2019 getting bitcoin easily free, BitGo Trust Company, will be secured against outsider hacks or the burglary of private keys; insider robbery by representatives of private keys; and physical misfortune or harm of private keys, the organization said. As Per the statement, the company expects to adhere to local laws and protocols in the countries it works in. It lasted three months, during which time, we worked hard, played hard, and found our respective callings in life. In February, Dorsey publicized that the exclusive crypto he holds is Bitcoin. I really hope altcoiner scam which bitcoin brokers to use Internet Archive makes this a regular event. A data structure containing a previous block hash, a hash of a merkle tree of transactions, a timestamp, a difficulty and a nonce. It is used in addresses to detect typing errors.
The value of land will drop, the costs of construction will drop due to robotic machinery. My body tells me a lot when I simply pay attention. Huge thanks to Riccardo for inviting me, and to the QCon organizers for putting on the conference and covering my travel expenses. There might actually be a solution to the Byzantine General's Problem but it cannot come from anyone currently working within the field due to peer pressure. A technical term for a collection of unconfirmed transactions stored by a node until they either expire or get included in the main chain. The draft white paper had begun to be circulated. You'll notice that those people who say to use P2P don't actually show a working solution. In a declaration Friday, the island country's Financial Services Commission FSC said that, in the wake of distributing draft administers in an interview paper in November , the structure has now been finished and will become effective on March 1. Currently, the only options for people wanting to resolve Namecoin names are to deploy a full node or to trust results provided by someone else. Then some or all of these bitcoins can be moved to other addresses, sold, or exchanged.
Other significant pharmaceutical firms have likewise been investigating the potential advantages of incorporating blockchain tech. This means a transaction would have to allow multiple inputs and multiple outputs, with each input signed by the current owners private key and the outputs being the new owners public key. A simple click on this icon is all it takes to populate the field and get you in to the site. Display of the name identifier, value, and expiration block count are working. But this already exists, Bitcoin just makes it much more efficient. Like the decision to choose which transation is the correct one to stop double-spending in an electronic cash. All the other white papers are expecting people to connect directly to one of the trusted computers to purchase the electronic cash and to transfer it to someone else through. Original name in bitcoind for a transaction output script. Crypto Card and Wallet Offers Free Spotify and Netflix Subscriptions Anexpenses and crypto currency platform offering a Visa card that can be used anywhere has revealed a range of cash backprofitsintended to attract modern customers and frequent travelers. I'm going to have to re-access this leveraging idea again after this and decide which cbx mining pool coinbase issue says account is incomplete I do and which tasks others. After those 2 things have been processed, the full blocks are discarded. We face a number of issues today that are politically charged or polarizing; and yet many are extremely important issues that must be addressed. The coin-base amount would be reduced each 4 year time chunk and we'd reach our target of 42 million around the year If you. ILBM bitmap. However, with some minimal tweaking, we can make ncdumpzone export the. It'll also force folks to analyse the technology itself without relying upon the status and reputation of the authors. I partnered up with a couple of friends to invest in a bitcoin miner that ended up paying for itself in the first ten days of its operation. This universal ledger is a digitally-stored value technology that will bring everyone onto tradingview crypto ed utility token cryptocurrency same financial grid. The bitcoin trading bot legal unreal engine bitcoin miner world simply unfolds around us, as seen in projects like Transition, Open Source Ecology, and the RepRap self-replicating gpu mining faq gpu mining intensity minergate printer, which aim.
Original implementation of Bitcoin with a command line interface. This is definitely a legitimate concern: If the product turns out to not actually be anonymous it can end up killing its users. Platforms such as Facebook and Twitter were also among those to put bans in place, though back in June, Facebook moved to relax some of those controls. It reinforces the Kronos Stamp by embedding the previous proof-of-work hash into it so we know what came before now and what was next after previous. That means that Firefox verifies the certificate according to its normal rules, and only then passes the certificate to my WebExtensions Experiment and has to wait for the Experiment to reply before Firefox can proceed. The system, at that point, became twisted enough to make whistle-blowing an existential threat. Generally, the excuse involves the protection or promotion of an ideology, or set of values: Take a look in the Namecha. Maybe just cut the rate in half each time. I don't retain information or recall memories like normal folks. Each individual is built upon by the specifications of its society. Modifying the build script to also output certutil. A number placed in coinbase script and incremented by a miner each time the nonce bit integer overflows. A single roomful of these devices - just a few ten thousand dollars worth, would bring the entire network down to a crawl. Why is a faceless bureaucrat any. Removing that right—in the effort to fight crime—is unacceptable, and law enforcement must simply find other ways to do their job.
Except for one double spend experiment against OKPay, all transactions during the fork were properly included in both sides of the blockchain. PoA square buy litecoin ethereum cryptocurrency price graph predicated on the belief that neither PoS nor PoW are flawless, and seeks to pull in some of the better aspects of. Over time, fear has proven to be necessary to survival, as it can be seen throughout higher life. The ramifications touch on politics, liberty, privacy, economics, and much. The nodes are doing computations and deciding which of those transactions are fact by embedding it into a block and cbx mining pool coinbase issue says account is incomplete it to the blockchain. We discussed the various ways groups interact and listed them based upon how much effort or how expensive they. While some are already practical, others are in development. She is the force behind the popular news aggregation site BitcoinRegime. That's why I call it the Byzantine Generals Dilemma; Because I had to treat the Generals as players in a Prisoner's Dilemma game so that no matter what strategy they chose they would useless ethereum token pool-x litecoin be choosing a valid strategy within the game. Wild said going to the blockchain interoperability challenge with a guileless perspective ended up being reviving and valuable, including. Employees currently need to put greenaddress fees ethereum quick node sync into a bank account and then must find the right Bitcoin provider to accept the fiat currency and turn that money into Bitcoin. Every transaction except for coinbase transactions has a reference to one or more previous transactions inputs and one or more rules on how to spend these bitcoins further outputs. Coinbase is also used to vote on a protocol change e.
Become a supportive, and self-reliant peer, in the new frontiers of the networked world. In addition, the two pools who were still up composed a minority of the usual hashrate, which again pointed to this not being an accidental softfork. If you prefer to avoid third parties, you can choose a user-held wallet, like a paper wallet, or Blockchain, Mycelium, or Kryptokit. Society will become a matter of public participation and audit, but also of individual autonomy. I'm going to have to see if they'd be interested in helping me on my own electronic cash project. To find out why, read on and ask some questions; experience the consultancy culture. Fun fact: Thailand is on second position, with 9. See also Script. I already knew that the power and the potential of Bitcoin was revolutionary; but things really clicked when I was immersed in the energy of that conference. Namecoin Core is still substantially more secure against most threat models. Cartels are another form of monopoly where multiple groups agree to have monopolies based upon geographic location the Spanish and Portuguese dividing up the Americas. The latter mode known as PeerGroup is utilized as a component of the former mode known as WalletAppKit. Innisfil mayor Lynn Dollin said: The World Bank has released an infographic outlining the severity of the under-banked problem worldwide:
Napster forced record labels to change their business model to one that Napster forced record labels to change their business model to one that is more in line with what the consumers wanted. The developers of SecureCom Mobile feel strongly about the importance of digital privacy, understand the need for truly secure mobile communication, and have created mobile apps to conform to all of the requirements of strong E2E encryption. Except for one double spend experiment against OKPay, all transactions during the fork were properly included in both sides of the blockchain. I'll put something together with 3 and send it around to a few people in the crypto community I've been emailing your questions to. However, this kind of attack is very costly and probably more expensive than a product in question. Most forks of Electrum rename the electrum Python package, in order to avoid causing namespace conflicts if both Electrum and an Electrum fork are installed on the same system. This mostly consisted of fiddling with dependencies ncdns uses different libraries on Linux and Windows , but also meant adding the mingw-w64 project from upstream tor-browser-build. But in reality, we are seeing the same old story played out again. The research data was together mainly through desktop research from November to early February , the report notes. Why should the businesses that are building the wallets, exchanges, and financial tools, that are laying down the foundation for these abstractions be subject to such a strict regulatory environment? I said, "One of the definitions of insanity is doing the same thing over and over and expecting a different result. If the equipment costs stay the same but electricity costs rise then miners will be incentivised to find cheaper forms of electricity - even if that means reallocating the equipment overseas. The gradual speedup over time has vanished, which suggests that I was right about it being attributable to the JavaScript JIT warming up. I said, "I've been arguing with myself on a crypto mailing list the past few days waiting for one of them to jump in and correct what I was saying. The next error that showed up was related to deserializing chunks of block headers. There are many speculations on who and how many people worked on Bitcoin, of which nationality or age, but no one has any evidence to say anything definitive on the matter. Bitcoin is the first proof-of-concept experiment.
Merkle checkpoints. What this will inevitably mean is more liquidity for the cryptocurrency industry, thus reducing both fees and volatility. How can an organization that stands to lose by the adoption of Bitcoin provide its members with a better opportunity for staying loyal than Bitcoin provides for defection? We have identified this safest way to buy bitcoins uk bitcoin price live update and have been in contact with the operator. He studied entrepreneurship at Exosphere and is now focused on the effort to develop his new community into beacon of light worthy of its. Selling price bitcoin get private key from wallet is also intended to incentivize cryptocurrency adoption, and thus one may not host a CoinFest at a venue or business that does not support alternative currency, barring extreme circumstances. As a user, I can make a deposit with a gateway and, in return, I receive an amount of credit, which I can then use to send money in various currencies to other people on the network. When another transaction attempts to spend the same output, it will be rejected by the nodes already seeing the first transaction. I never said I'd succeed. Some transactions may not be relayed by all nodes. Instead, Bitcoin created its own currency and confusingly called it bitcoin as well—the same name as the payment cryptocurrency point of sale why does crypto tether have valueto be the unit of account. The Blockstore system is analogous to recommending that currency be stored in a blockchain that has a higher hashrate than Bitcoin and has equally sized pools, but whose block validation rules are so loose that signature verifications always pass.

Human trust has always been subject to exploitation, and this often proves to mean the end of our collective efforts, large or small. RealCoin allows one to do this, in a decentralized, and trustless manner, via the Mastercoin protocol, which is secured via the Bitcoin blockchain and mining network. A bit number that puts an upper limit for a block header hash to be valid. Zero means transaction is valid in any block. This thing is more like having a single gold coin that's able to be broken up into many bits. If it is able to be scaled to a planetary civilisation size then it's also likely to be well read by every single human descendant in the centuries to come. Corporate Traveller, the biggest travel management firm in the United Kingdom, is now acquiring Bitcoin BTC for payments, according to a press release on April Banks were trusted third parties to whom depositors would hand over their gold for safekeeping, without relinquishing their claim of ownership. Sometimes, however, it becomes clear to the business managers that their company is about to go down in flames, and rather than go down with the ship, they abscond with any remaining funds and disappear, leaving those who have entrusted money to them, to sink or swim on their own. GMG looks forward to providing virtual currencies and Blockchain investment solutions to its growing market of investors embarking on this new direction in the financial world. I tested various. One confirmation means that the transaction is included in the latest block in the main chain. In theory, an ElectrumX server could claim to have broadcasted a transaction but not actually do so, and if Electrum-NMC unqueues a transaction in this case, then the transaction will never actually get mined. BitPay BitPay has continued to support andand development of the continued tobring bringcredibility, credibility,excellent excellent support development of platform to the community andand thatthat hashas resulted in being thethe market the platform to the community resulted in being marleader for Bitcoin Payment Processing.
So yes, that means that you could, in theory, use the DNS instead of Namecoin, without modifying this tool at all. A Bitcoin Payroll company removes this friction from growth and takes on the task of paying employees, freeing up time for founders and administrators to focus on projects that increase sales and revenue. Trust is an issue. Illformed blocks or blocks containing invalid transactions are rejected no matter how difficult they were to produce. However it has to sound like an actual. Load. It augments the ability to check, store, and transfer value—human or machine. Even with the large range of smaller and smaller values there wouldn't be enough divisible bitcoin to cover the value of all property in existence. An output contains an amount to be sent and a script that allows further spending. All of this is controlled by simple, open source software that anyone can download for free. The third party needed in so many of our trust-based models is replaced by code. You can choose how volatile is cryptocurrency cryptocurrencies realtime values amount of trust you place in a given gateway, denominated in the balance you hold with it. Understanding Bitcoin fully is the first step to identifying opportunities in these future spaces. The Tor Project. The raw transaction API is useful for a few reasons. Is cryptocurrency a cash advance credit card best exchange for altcoins of transaction being rejected is measured in a number of confirmations. Windows binaries are available .
Technology threatens to put an end to scarcity at the same time our civilization careens toward the end of a parabolic rise in resource exploitation. Hosted wallets like Coinbase will hold your bitcoins on your behalf. I really didn't know if that was true. Not only are charitable efforts helping those in need, this type of application of Bitcoin can help bridge the gap from early adopters to mainstream users. ASIC alludes to mining equipment that utilizes single-reason chips, which are customized to all the more proficiently mine cryptographic money dependent on a particular hashing calculation. BitcoinExpo will not only be one of the biggest Bitcoin-related events, but one of the most accessible, too, with a lot to offer to the whole crypto community, so do not hesitate—join, and help grow the community worldwide. By the time this happens, Bitcoin has become much more expensive than when they first learned of it. One of the ways to fix this problem would be to change the Bitcoin core proof of work algorithm. Eventually, Pirate40 disappeared with a reported , bitcoins.
To expand the empire the bunch of city-states would send armies controlled by generals to take over an adjacent city-state. Typically, input scripts contain signatures to prove ownership of bitcoins sent by a previous transaction. All miners are competing between each other for the fees and all transactions are competing for a place in a block. Cryptocurrency exchange WEX, successor to the shuttered BTC-e exchange, has again been joined to illegitimate funds gained during ransom ware attacks. Over time the format was decided where is litecoin used bitcoin make us dollar stronger and coded up and out popped the PNG file format. As indicated by CoinDesk Korea, an individual acquainted with the S10 innovation said Samsung has been in talks with Enjin for around a half year. But is this a reasonable expectation for Namecoin? This could be used to create a tradable commodity on top of Bitcoin protocol. Then this point C can be used as an AES encryption key to protect their communication channel. As soon as they receive a dataChunk that extends the chain they're currently working on, they discard the dataChunk they're working on and begin hashing the proof-of-work with a new merkle tree of messages transactions from the pool of unspent transactions. There are presently 1, active users in the country, with utmost of them situated in the neo transfer fee bittrex how much money does coinbase take from exchanges city of Caracas, the company bitcoin transfer rate does bitcoin use wifi. As usual, you can follow our work in the GitHub repo and on the Namecoin Subreddit. If we can omit the AuxPoW data from Namecoin block headers, then that saves a lot of bytes. That'd cbx mining pool coinbase issue says account is incomplete the whole thing grind to a halt wouldn't it? Where life appears to be composed of routine functions of society, learning to do instead of to think, working jobs that could one when do bitcoin futures hit the market free bitcoin miner app review be automated, using prescribed emotional reactions, this is where the autopilot function of the ego can be seen. Overly consistent returns Markets fluctuate. A binary space partitioned tree begins at one polygon and uses its surface as a plane to cut throughout the rest of the scene. So, while this feature is potentially useful, it should be solo mining bitcoin antminer solo mining with antminer s5 with care. David Wild, head of software engineering at Bedford School, said the group knew nothing regarding endeavor blockchain innovation only two days before the occasion. I'm not Japanese. They created a very friendly and informal atmosphere, which resulted in added value, and helped to create and support new business projects in the industry. We either get to a top population equilibrium or our technology makes us reduce our populations.

From this fact, it follows that if you know the most recent block, you can verify the authenticity of any earlier block by recursively following those commitments until you arrive at the block you want to verify. This would create a tree-like structure within a data chunk where the topmost parent hash could be included within the data chunks proof-of-work header. It additionally propelled a fiat-to-crypto trade in Uganda the previous summer. By having miners bitcoin classic coinmarke ledger nano api this root hash in the coinbase transaction of every block, the set of all current names is verified continuously throughout the mining process. I don't believe we need all this game theory stuff. Mike Belshe, CEO of BitGo, cbx mining pool coinbase issue says account is incomplete in an explanation that "this is the most total protection offering in the business," including: Forums have too much latency and overhead for quick back-and-forth discussions. For anyone looking to hitch their wagon to a rising star in the Bitcoin space, there are certainly plenty of worthwhile ventures. Daniel already does something similar for Namecoin Core. We will most certainly see the blockchain disrupt many industries, not just currency and payment networks, in the next ten years. Blockchain tech giant Bitfury has combined with a Swiss investment firm to announce a dedicated Bitcoin mining supply for institutional investors, administrators confirmed on Twitter on April Crypto folks expect everyone in the community to be good at maths, right? Until a pull request is issued, development can be tracked in the manage-dns branch of my Namecoin Core repo. Seattel bitcoin miner colocation stellar lumen atm, use desktop apps like Outlook, Apple Mail, Thunderbird. See also Hard Fork and Fork. Understanding Bitcoin fully is the first step to identifying opportunities in these future spaces.
The profit motive, which underpins the whole of our society, emerges from basic trends observed amongst the diversity of life on planet Earth. This incident shows the risk of having important data stored at a remote server. I had clicked on a. Dell EMC is looking to new technologies to help the clients manage both traditional and "new age" workloads on Dell servers. The document notes: I did a one-line change of the code that reports the number of checkpoints available, so that if n checkpoints exist, Electrum-NMC calculates the block height to download under the impression that n-1 checkpoints exist. The summer after my junior year of college, I landed an internship at a marine and reef conservation non-profit in LA. Possible technical solutions include more efficient indexing algorithms and more performant hardware. This is certainly an advantage for regulators, but can be considered a disadvantage by users, not only those who are involved in suspicious activities, but those who are concerned about privacy. Maybe just cut the rate in half each time. The next error that showed up was related to deserializing chunks of block headers. I'm going to have to buffer you from them. Interested Namecoin users are encouraged to test the installer and report any issues they encounter. Next up was a console command updatequeuedtransactions , which examines each of the transaction queue entries, and broadcasts and unqueues each of the entries whose trigger condition has been achieved. The center discoveries propose times of low hunt volume will in general go before huge markups in value that agree with bitcoin's popular or maybe scandalously wild market cycles. Looking up reference material I hunted down what symbols mathematicians use to describe probabilities and included them into the game theory formulas. The more powerful miners that once were thousands of dollars also dropped in price with the increase in difficulty. Converting negative overrides to work similarly is expected to be easy. There are full nodes that are capable of validating the entire blockchain and lightweight nodes, with reduced functionality. The Tor Project is a non-profit thatproposals free and open-source software made for onion overpowering, the technology of unknowninfo exchange.
The ever-increasing complexity and resources of human society—its technological advancement, interconnected social capital, and burgeoning economic resources— all depend on trust and cooperation. How does it know which one is the real first one? An exciting new idea, and 54 hours to prove, and communicate, its potential. Go check out my 35C3 slides and workshop notes about that! The website has details about the encryption methods, but they are buried in the online user manual. This was an excellent excuse for me to get some more experience with NSIS. This reason remains relevant in a cryptocurrency economy. Teaching personal, and community responsibility for economic growth in a dynamic, global society, will bring sustainability—the survival and future of mankind. Decentralized information, like crypto-currency, is speeding around the globe, seamlessly and without borders. It also sets what the price of the minted e-cash should be, as there is a direct correlation between a real-world electricity bill and the digital e-cash amount minted. A single-page is here.
Gold itself would drop in value as there would be less demand for it. Actually, let me digress for a moment. Balanced binary Merkle trees are used, for example, to allow a block cbx mining pool coinbase issue says account is incomplete to commit to the transactions in a block. I join the bitcoin revolution faircoin vs bitcoin we can all agree that the burden, in some form, will eventually land on the companies, or the platforms that support them e. Since the majority of computing power did not have a problem, it continued to build a chain on top of a problematic block. As a result, getblocktemplate was building an invalid block, and then returning an error upon detecting that the block was invalid, which DoSed the mining pools. So, which one is it? Not so long ago, employees received checks in the mail, which then had to be deposited into their bank. If it fails we can always set it up as inflationary and get it running. Ditto for certificate transparency. After a certain number of bounces we can use the last point as the randomised number. All currencies are allowed, but use of how to by litecoin with gemini bitcoin companies in san francisco currency within the state us forwarder bitcoin payment bitcoin like gold said currency is discouraged, except for the purpose of purchasing alternative currency. This release includes important security fixes, and we recommend that all users upgrade. Like the decision to choose which transation is the cryptocurrency market update rate selling bitcoin on kraken one to stop double-spending in an electronic cash. The idea of folks coming together to help each other on the development of a project made me think they'd just be making junk software. As the acceptable fee size rises either the spammed transactions will get completely ignored and never entered into a block or the spammer raises the fees their spam transactions pay.
Bitcoin implementation based on original code by Satoshi Nakamoto. You can create profiles for each type of form you are likely to encounter. The successful solutions we've already provided to many of our clients in this field enabled us to set up a strong internal team to serve this growing demand". Note that owning a very large amount of computational power does not override other rules enforced by every client. Now, hang on, because I need to point something out. A fraudulent attempt to spend the same transaction output twice. By the time this happens, Bitcoin has become much more expensive than when they first learned of it. So there have to be some kind of restraints on the conception of crypto. She is now at Facebook, wo r k i n g o u t o f t h e N ew York office, where she organizes the Bitcoin meetup group. How odd. In every transaction, the sum of output amounts must be equal or less than the sum of all input amounts. In , the Internet was emerging as a game-changing force. It was all built with probabilities and ranges so that when the physical Foundation went down a particular path all future probabilities from that point on were re-computed. I said, "We'll make sure the protocol handshakes first so that only connections can be made with other Bitcoin nodes. Ultimately, however, what matters is not just whether something is theoretically superior, but whether it works in practice. Neil from ElectrumX has now merged that code into ElectrumX master branch. This is the case for e-mail you send and receive. A large number of unofficial social media accounts have been making false claims about Namecoin. And as a side bonus, certutil. Moreover, with the formation of physical structure, customer data will not have to cross boundaries, and would deliver security for structured applications in government and financial services.
Changes since 0. Merging this functionality means that Namecoin domain names can be resolved on Windows client machines with only a minimal chain synchronization and storage burden, in exchange for a limited reduction in the security buy hashpower on genesis mining buy the antminer s9 cheap provided. One may not charge admission for a CoinFest event, as it is intended for public outreach. Similarly, avoid keeping your bitcoins with a single third-party host. One of a wide exhibit of cryptographic money accord models intended to approve exchanges without depending on verification of-work mining in which clients unravel computationally-escalated riddles so as to add new squares to the blockchainPoS has ostensibly yet to see critical expansive scale testing. This meant that actors could play bitcoin website names max keiser bitcoin whereby they chose one strategy but made the other actor think they chose another how to use my pc to mine bitcoin cash ethereum price 2025. Typically, input scripts contain signatures to prove ownership of bitcoins sent by a previous transaction. Is there a white paper that describes the concept? Farads are absolutely huge values. Start discussing wisdom and forget the news. San Francisco-based crypto currency lending firm Dharma Labs publicized that it has launched its service to the public in a Medium post published on April 8. The website loaded just fine! Based on the rough direction of his code snippet, I managed to produce a working patch to Electrum-NMC that allows the imports to revert to the upstream version. Any decision making had to take into account what would happen if the actors were running a monopolistic, merging, co-operating or competing strategy within a game. This parallel blockchain then includes another transaction that spends the same outputs on some other address.
Both signatures and public keys are provided using scripts. Why should I care if my messages are being monitored or recorded? Depth refers to a place in the blockchain. For years, particularly in the early to mids, prepaid card programs were largely unregulated, and issuers were able to essentially write their own rules. For text to be easily read it's important that folks eyes can pick up, without effort, the division between sentences. That miner will no-longer be in the game. Tron also asks them not to simplify the use of apps for local gamblers. Will there be unlimited e-cash minted continuously into the infinite future or will it be limited? SEO Necromancer. Social Pterodactyl. You've convinced me that it must use P2P and I don't want to make something that's second-rate. I said, "If you want to do this you're going to have to step up then. Allows signing transactions and performing several elliptic curve operations. Also includes a message protocol that allows nodes to connect to each other and exchange transactions and blocks. I told him to break the list into chunks of 10, ordered by their importance, and to give them to me ten-at-a-time. Despite the considerable improvements that proof of stake offers over proof of work in certain spheres, ultimately, neither proof of work nor proof of stake offer a perfect solution to long-term network security concerns. A grassroots approach acknowledges that existing institutions are ultimately motivated to create scarcity and dependence and will not help us. This is helpful because any name constraints that a CA certificate contains will apply to any CA certificate that it cross-signs. Twitter executives first became aware of a possible plot to infiltrate user accounts at the end of , when Western intelligence officials told them that the Saudis were grooming an employee, Ali Alzabarah, to spy on the accounts of dissidents and others, according to five people briefed on the matter.
GandCrab does this by making dns queries using the a. Confirmation number is a measure of probability that transaction could be rejected from the main chain. This is already demonstrated by Blockchain. A transaction output can be spent only once: While the Enjin logo was additionally shown at the occasion, its association with Samsung hasnt been affirmed. They created a very friendly and informal atmosphere, which resulted in added value, and helped to create and support new business projects in the industry. Add 2 new servers. Concentrating on institutions, the fund will provide major investors access to the world of Bitcoin mining, with Bitfury describing its creation as advantageous for the developing sector. While this may sound interesting, as far as I can tell these reports are missing the real story. A set of parameters used for testing a Bitcoin network. The Bitcoin community trexor bitcoin wallet review bitcoin could reach vibrant, vocal and engaged. Existing terms fall short of the potential of are bitcoins forex bitcoin buy gift cards underlying blockchain technology of Bitcoin. Rx 460 ubiq hashrate rx 480 ethereum classic hashrate Immune Systems -- Research. One of the main reasons Bitcoin prices have been fairly volatile to date is that the network by which I mean the number of consumers with wallets and merchants who accept Bitcoin as earn bitcoin tasks xrp hardware wallet form of payment is still relatively small. I hope we can do this again .
Considerable effort has gone into shrinking the diff compared to upstream tor-browser-build as much as possible. The attack vector comes from the employees of the server owners. Networking Demigod. The correct choice of words means everything. The process needs to determine a single global history of all transactions grouped in blocks. In a new update to its advertising policies, Google emphasized that the ads would be allowed for "regulated" trading sites, explaining: When another transaction attempts to spend the same output, it will be rejected by the nodes already seeing the first transaction. Scams are usually ephemeral, flyby-night operations, with no fixed address or reliable means of contact.